- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Static Routing and Virtual Private Network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Static Routing and Virtual Private Network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 02:03 AM - edited 03-08-2019 01:38 PM
Greetings,
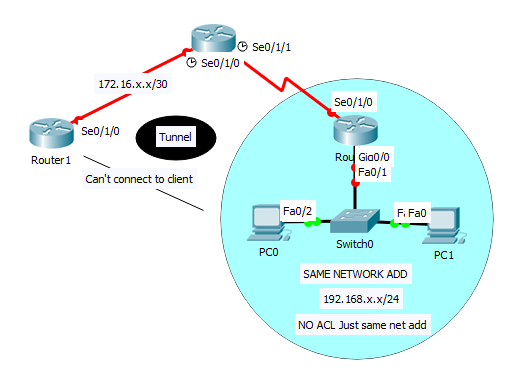
I am currently creating a simple network design consists of Static Routing and Virtual Private Network. The tunnel between two routers works successful. Static Routing is configured on both sides however one router cannot reach the clients. Can someone help me out to troubleshoot the network issue. Thank you and God Bless.
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 02:34 AM
looks like configs didnt load , is the client subnet allowed in the vpn acl to pass down the vpn tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 02:51 AM - edited 01-31-2018 03:05 AM
Hi Mark.
There is no ACL configured yet. In the router where the clients are connected belongs only in the same network address which is 10.x.x.x/8 and can successfully ping each other. The two routers are connected through VPN and it works but one router cannot reach the clients
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 02:57 AM
so taking this example under the crypto there is a acl which states what the routers are allowed speak to down the tunnel , in this case its acl 100 and subnet 1.1.1.x/24
is this the same setup or have you a different setup
https://www.cisco.com/c/en/us/support/docs/security-vpn/ipsec-negotiation-ike-protocols/20641-initaggr.html#configs
crypto map mymap 1 ipsec-isakmp
set peer 14.38.69.71
set transform-set myset
match address 100
access-list 100 permit ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 03:11 AM - edited 01-31-2018 03:13 AM
How can the other router successfully ping the clients regardless of ACL? The topology look like as follows.
Thank you Mark. God Bless.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 07:25 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 07:31 AM
It would help if we knew details about how the VPN is configured. Mark is asking about how the ACL is configured. If this is a traditional IPsec VPN then there should be a crypto map with an ACL. But if this is done using VTI then there is not an ACL. So please provide details of the VPN configuration.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 04:06 PM
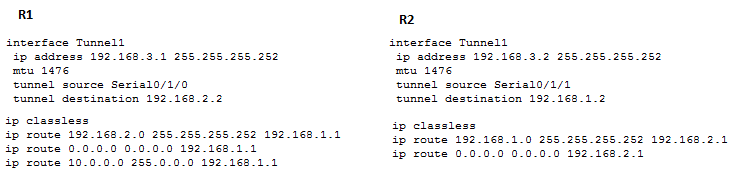
Here's the simple configuration. Thank you God Bless.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2018 02:50 AM
the statics look incorrect if traffic is supposed to be going down the tunnel , none of them are pointing out the tunnel interface ips
T1 side a static like below as example would send traffic down the tunnel interface
If there was as a 10 range behind you were tring to reach in T2 side
ip route 10.10.10.0 255.255.255.0 192.168.3.1
the next hop must be the tunnel ip of the interface 192.168.3.1
I think this might help it breaks down the GRE setup between 2 routers with example, basically what your trying to achieve in your design just with different subnets
https://supportforums.cisco.com/t5/network-infrastructure-documents/how-to-configure-a-gre-tunnel/ta-p/3131970
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2018 06:13 AM
Mark is correct about the static routes. The very limited config that was posted does confirm that this VPN does not use VTI. So there should be a crypto map and ACLs. It would help if we could see those.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2019 03:12 PM - edited 01-15-2019 02:38 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2023 04:01 AM
covernet-vpn.com website proposes to invent the combination of this type of XOr Patch tunnel with the Cisco VPN protocol. Do you think this is possible?
Combining an XOR patch with a Cisco VPN protocol is not a straightforward or common task, and it's important to note that attempting to modify or patch a VPN protocol may not be allowed or supported by Cisco and could potentially violate licensing and legal agreements. Furthermore, making modifications to VPN protocols can introduce security risks and may not be advisable.
If you have a specific use case or requirement that you believe necessitates making such a modification, it's essential to work with Cisco or consult with a professional who is experienced in network security and Cisco VPN solutions. Cisco's VPN protocols are designed to provide secure and reliable communication, and any modification should be done carefully to avoid compromising security.
Keep in mind that making changes to a VPN protocol can also create compatibility issues, which may prevent you from connecting to Cisco VPN servers or other network devices. If you need to customize your VPN configuration or address specific requirements, it is typically best to work with Cisco support or a network professional who can guide you through the appropriate configuration options and best practices within the existing Cisco VPN framework.
Before making any changes to your VPN setup, ensure you have a clear understanding of the security and network implications and consider consulting with professionals who specialize in network security and VPN technology.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2024 10:50 PM
Errors in the interface, gateway address, or subnet mask can interfere with the correct routing of traffic. One of the routers for the subnet where the clients are located might not have a static route. Traffic may be bouncing between routers indefinitely due to a routing loop that is likely the result of a misconfigured route. Verify whether either router's firewall rules are preventing traffic from passing between the subnets. Even though the tunnel seems to be working, the VPN may have internal issues that prevent certain types of traffic from being routed.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide