- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Switch to Switch ( L3) - Connection Solutions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Switch to Switch ( L3) - Connection Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2023 05:42 AM
Hi All ,
I have 2 separate networks each with Core switches , say network 10 and network 192 and wish to connect the 2 networks and also the relevant vlans with 2 cables running from one to the other for a little bit of resilience but it isn't that pressing to have any fault tolerance.
Network 10 is running VTP, So just wondering what is the best method and practices to attain this.
thanks
- Labels:
-
LAN Switching
-
Other Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2023 05:54 AM
two separate network and then you specify two VLAN, can you more elaborate ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2023 06:10 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2023 06:13 AM
the VLAN can connect to each other in both SW through the trunk if you allow VLAN and use same native VLAN
BUT
here since you use VTP in one side I prefer use VTP transparent or make sure the config of VTP is correct in both SW before interconnect.
the VTP effect VLAN in DB and effect VLAN allow in trunk through pruning
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2023 08:34 AM
Hi,
Since each network has its own vlan/subnet, you can simply use a /30 to connect the 2 networks together. If you are looking to add fault tolerance, you can use multiple physical links e.g., 2 cables with 2 /30s, or use the same 2 physical links and put them in an L3 Portchannel with 1 /30. Using this solution, it does not matter if one side is using VTP and the other side is not.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 06:37 AM - edited 06-06-2023 06:38 AM
As I will be doing this on production I just want to be completely sure - so I have the config as below. I have not connected yet.
shouldn't this be a trunk and not an access port like the below ? and what else am i missing ?
Ive got a /30 SVI on vlan 88 ON on vlan 88 on SW1 and SW2
SW1 Config:
interface Port-channel45
switchport access vlan 14
switchport mode access
end
interface GigabitEthernet2/0/11-12
switchport access vlan 14
switchport mode access
channel-group 45 mode on
SW2 Config:
interface Port-channel45
switchport mode access
interface GigabitEthernet2/0/11-12
switchport mode access
channel-group 45 mode on
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 06:50 AM
It should be an access port because all you need is a transit vlan, which in your case is 14. You also need an SVI on each switch and since you are using a vlan to connect these 2 networks together, it does not have to be a /30. It could be a /29, 28, etc..
Also, on switch-2, make sure you specify vlan 14 as below.
SW2 Config:
interface Port-channel45
switchport mode access
switchport access vlan 14
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 08:46 AM
Ok will try that thanks for your input
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 10:07 AM
Ok will try that thanks for your input
Should not.
Also, before you start adding any static routes, make sure your physical interfaces are up, PO is up, and you can ping from one switch to the other and vice versa, link failover works. Static routes should be the last part and then you can test end-to-end.
Don't forget to do all this work in a maintenance window in case something unexpectedly goes wrong.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 07:09 AM - edited 06-06-2023 08:49 AM
One Q' are vlan in both SW is same ?
If same then config trunk and allow all vlan
If not then use access port and SVI in each SW and you need static route in each SW for vlan in other SW.
**SVI for transit vlan' this vlan must add to both SW
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 08:50 AM
The vlans are different on both switch.
thanks again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 09:03 AM
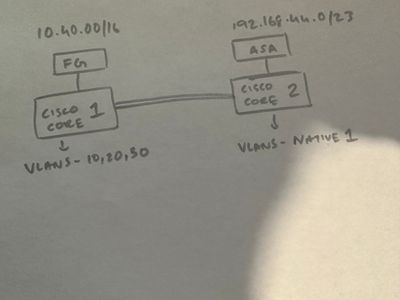
So basically I want to connect sw1 and sw2 and make sure the clients in both subnets can ping and access each other… just put up a picture for ref…thanks again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 09:07 AM
use access port and SVI in each SW and you need static route in each SW for vlan in other SW.
**SVI for transit vlan' this vlan must add to both SW
This solution so what you need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 09:11 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2023 09:15 AM
Yes SVI of vlanX which use only to interconnect both l3sw.
Now you need static route
Ip route <subnet of SW1> svi ip of SW2
Ip route <subnet of SW2> svi ip of SW1
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide