- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: VLAN under a budget (2960s), phisically and logically
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VLAN under a budget (2960s), phisically and logically
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2021 11:00 AM
Hi all, I have been reading some of the answers to a similar question regarding vlans on the same subnet.
Apparently it "may be" possible under some circumstances. Let me explain you my network:
I have this network: 192.168.1.0/23, where the dhcp appliance is 192.168.1.1 (a tplink load balancer router firewall thingy) with a pool of 192.168.0.x to 192.168.0.1xx.
That dhcp pool is for guest devices, my small office devices are on the 192.1681.x side of the network using the same appliance to reserve those ip's. Right now we just have hubs, no vlans, all mixed and we want to have some order and security (finally after 4 year, management decided to give me some budget, not much but something).
What I was able to source were some 2960's 48P and WS2980 24P for the task, with the budget is what I could get, sorry.
To avoid many word, a image of what I have and what I would like to accomplish:
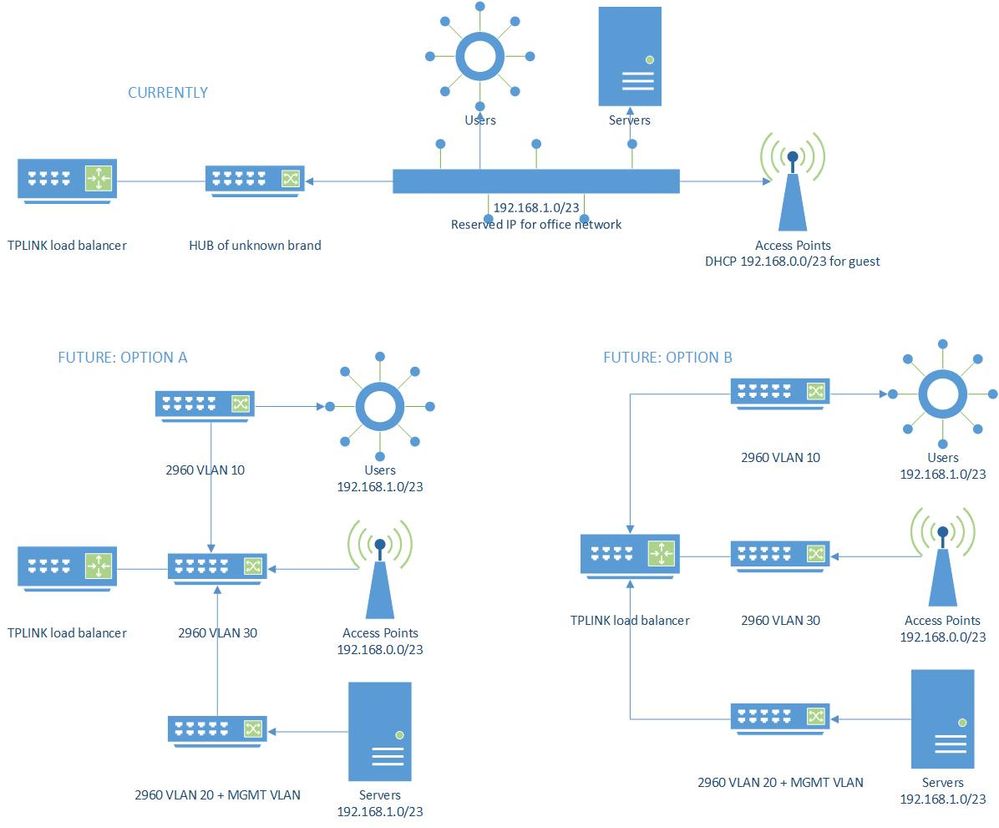
Now, the requirements:
- VLAN10 should have internet access and be isolated from the rest, the ws2960 will power some poe access points for the wireless devices, nothing fancy, just internet access is all they need.
- VLAN20 and 30 may communicate, also have internet access.
- Further VLANs (maybe one or two more; for IP cameras and another devices that are in another building but want to have them on their own switch because cabling budget is tight) will be in that same subnet, since the dhcp device does not offer multi-nat, and static ip's will be a paint to manage.
The future, is all goes good would be to migrate the dhcp to a windows server and then I would be able to create more networks, but right now my hands are tied.
The desired outcome:
Separate the guest from the office, and have a little more network privacy and security. Yes, I'm slowly walking with management to get them into the new era band wagon.
So, what do you think? is it possible? from the course I have seen with cisco, I can picture option a, but with option b I'm still waiting for an answer from the manufacturer to see if it is possible. Now, I said I can picture it, but don't know if it would be possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2021 03:18 PM
Congratulations on finally being able to move in a better direction. There is much about your network that we do not know and that impacts our ability to give really good advice. I would say that much of what you describe should be possible (especially separating the network into 3 separate subnets with appropriate policies for each subnet) but not in the way that you have described. There are several considerations:
- you have both vlan 10 and vlan 20 using 192.168.1.0. That will not work. While it is possible to have 2 different subnets in a single vlan it is not possible to have a single subnet be part of 2 different vlans. To get this to work you need to set it up that vlan 10 has a unique part of 192.168.1.0 (perhaps 192.168.1.0 through 192.168.1.127) and vlan 20 has a different unique part (perhaps 192.168.1.128 through 192.168.1.255)
- You describe 192.168.0.0/23 and 192.168.1.0/23 as if they were separate networks. But both of those describe exactly the same network address block, which starts at 192.168.0.0 and extends through 192.168.1.255. You need different masks for your networks. One set of masks that would work would be /25 for vlans 10 and 20 and /24 for vlan 30.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2021 04:08 PM
Thanks @Richard Burts, sorry for the little info, I will gladly tell you more. (Who knows, this may evolve into a good story hehe).
Also indeed you are right, the whole network that I have so far is 192.168.0.0/23. Now that you mention it, indeed, I would like to have one part of the network as vlan10 and the other part as vlan20, so I think I can work with that.
The network in question is a Heatlhcare network enviromment, meaning that some devices are already working with static IP's in other networks (their private networks) and mixed with the rest of the traffic, so, the chances of having trouble are great... really great.
With the network set to 192.168.0.0/23 I was able to "defragment" part of the network so, the guest are in the 192.168.0.0 side and I have the 192.168.1.0 for the office and the "HIT" part (CT, RX, MR, you name it). I took this case because the place does not have any IT support really, and now I'm even tasked to setup a domain next year, standardize stuff and all... remotely... so even configuration I'll have to do it remotely, I do have some smart hands on the site but not so IT inclined so I have to do most of the keyboarding as precise as possible, any errors will mean resetting and retry (and yes I have had plenty).
Now, (and yes, I'm still grasping some concepts and many times I get them confused), let me put a bigger diagram of the network I want to build. Let's just use option A for simplicity (since I know that the router can handle vlans, but I'm still awaiting from tplink to actually tell me how their config works, as their user manuals sometimes look like a bad translation in some points):
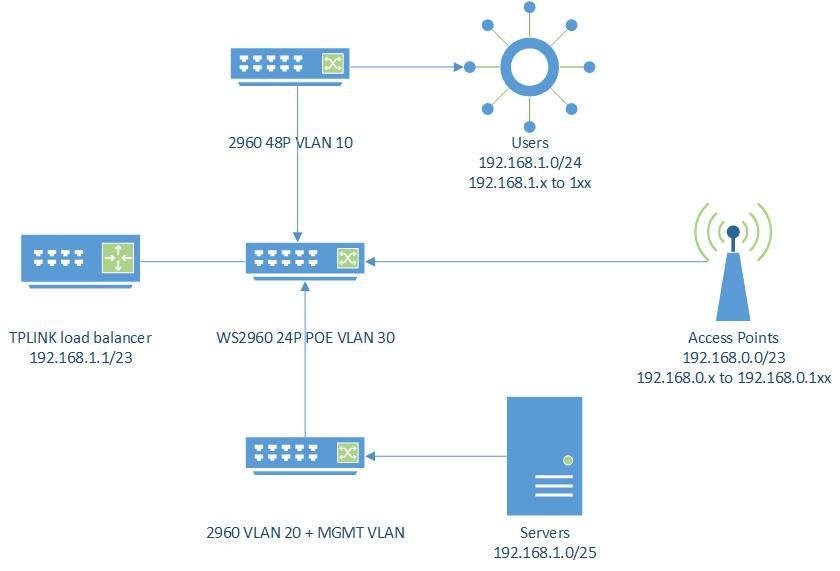
(omit any errors on the diagram, I'll correct them later)
The only problem I see, from a configuration stand point is to set the subnets to 25 and 30; because the router does not have the option to do nats per port. I do have an older netgear that has that option but it is so old that the throughput was just 25mbps and sometimes it will just hang and lock up completely (getting hot and a reset will not fix it, so I had management the r470t+, again, the most economical option I had at the moment).
Before going further, newbie question, do I need a router for subnet 25 and 30 to be able to communicate? because so far, I think I would need a router for that, and the r470t+ does not offer me that, sadly the more expensive r480t+ does have multi-nat but that's another story.
Since, I'm still waiting for the 2960s to arrive, I really do not know what capabilities they have that could help me, I'm under the assumption that they will do just vlans and that's all... unless you tell me they do have some "dhcp" capabilities that could help me? because that would make setting the subnets easier in that case, since most of the devices are in dhcp, then it will be a breeze. Only a a two-handfull of devices are in static ip and they are already in a production environment. I know some cli, and I have seen the 2960s on the field, but not in depth.
So, 192.168.0.x is not fragmented, but 192.168.1.x is a little fragmented, I was able to get some chunks together but at the end, if I need to drop one vlan, then let it be dropped
If I remember correctly I have this on my network today:
Wifi guest 192.168.0.x to 1xx
Office 192.168.1.x to 9x, with two printers, I think they are 192.168.1.5x
5 Servers 192.168.1.10x to 18x
HIT devices 192.168.1.15x-15x, and 192.168.1.13x-13x (yes, there are two groups of devices, sadly with static IP that cannot be touched, you know dicom stuff).
All that working so far in /23, so yeah... it is a mess, and in production state, so the changes I make are done as swiftly as possible.
So yeah, I think we now have a clear scenario.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2021 01:15 AM
Thanks for the additional information. An important part of your network that we are not clear about is the tplink load balancer/router/firewall. I have some questions about its environment and its capabilities:
- at this point the tplink is shown as connecting to a hub. So that is like an access port. Does the tplink have the capability to connect as a trunk port (have multiple vlans in the trunk with vlan tagging on the Ethernet frames)?
- at this point the tplink provides dhcp for a single subnet. Does the tplink have capability to provide dhcp for multiple separate subnets? Is there any limitation on how many subnets it can manage?
- at this point the tplink provides address translation for a single subnet. Does the tplink have capability to provide address translation for multiple separate subnets? Is there any limitation on how many subnets it can manage?
There are multiple models of 2960 switches and multiple feature licenses. We do not know what model and what licenses your 2960s will have.
It may be helpful to think about the changes that you want to make in terms of what happens at layer 2 and what happens at layer 3 (specifically in terms of inter vlan routing, dhcp, and address translation). At layer 2 the 2960 switches certainly have the capability to create multiple vlans and to do forwarding of traffic at layer 2 (perhaps using a combination of access ports and trunk ports). The capabilities of the 2960 at layer 3 depend on the feature licenses that your switches may have. Your 2960 switches might have the capability to do inter vlan routing (and if not then this needs to be done by tplink). Your 2960 switches should have some capability for DHCP or you might want all of this to be done by tplink. Your 2960 switches will not have the capability to do address translation, so the ability to do address translation for multiple networks/subnets must be done by tplink.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2021 03:43 PM
Before answering, this is the exchange I had so far with the tplink forum, I asked them:
------------------------------------------------------------------------------------------------------------
I know that the model I have does not have multi-nat, so all the network would be inside (for example) 192.168.1.0/23; so there's nothing else I can do with the budget I have so far. Knowing that I would have just one network,
can the R470T+ control VLAN communication? (yes I know I can let some VLANS communicate via the switches, but that is for later) Like allowing vlan10 to communicate with vlan20, or like, whoever is in port 3 can talk to port 4 but not port 5, or do some kind of control of "who gets to talk to who".
since I will have just one network, I assume all the current bandwith, firewall and routing controls will still work, right?
Regarding internet access, I'm still confused by the tag and untag settings for the wans, is there any place to find a more detailed manual about it? so far I know that would need to "untag" or "tag" at the port configuration, right?
------------------------------------------------------------------------------------------------------------
To which I got a reply:
------------------------------------------------------------------------------------------------------------
hi there, tag means when internet data outflow the router/switch, the data still obtain the VLAN tag in the data. Untag means when data outflow a router/ switch, the tag will be deleted and there has no tag on data. The PC can only deal with the data without a tag.
The function "control VLAN communication" of this model cannot work. The VLAN function of this router can only work as the network isolation.
But the "control VLAN communication" seems can work on the model ER605 and ER7206, here is the instruction for it: https://www.tp-link.com/en/support/faq/3061/
You can set up the VLAN and the ACL to manage the communication. By default, if there has no ACL, all the VLANs on the router's LAN port can talk to each other .
And this needs to wait for the latest firmware version coming up in few days.
------------------------------------------------------------------------------------------------------------
So apparently, soon the model I have better vlan control, so back to your question @Richard Burts
- at this point the tplink is shown as connecting to a hub. So that is like an access port. Does the tplink have the capability to connect as a trunk port (have multiple vlans in the trunk with vlan tagging on the Ethernet frames)?
Apparently yes.
- at this point the tplink provides dhcp for a single subnet. Does the tplink have capability to provide dhcp for multiple separate subnets? Is there any limitation on how many subnets it can manage?
By this you mean like providing dhcp for each port? (it has 5 ports total, 3 that can work as lan or wan, 1 fixed lan and 1 fixed wan) Now I noticed I never mentioned the model, sorry about that, is a tp-link r470t+ ver. 6 (https://www.tp-link.com/us/business-networking/load-balance-router/tl-r470t+/#overview)
Apparently that model does not have that functionality, that is available in the r480t+.
- at this point the tplink provides address translation for a single subnet. Does the tplink have capability to provide address translation for multiple separate subnets? Is there any limitation on how many subnets it can manage?
That is something that is unknown to me so far, BUT the manual does not mention anything about multiple subnets on this model (r470t+).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2021 11:04 AM
Thanks for the additional information. I find several things in the exchange with the tplink forum to be puzzling:
- They say "The function "control VLAN communication" of this model cannot work. The VLAN function of this router can only work as the network isolation." I am not clear what they are meaning when they mention network isolation. And I am concerned at the part that says control VLAN communication of this model cannot work.
- then they talk about control VLAN communication that does work on some models that are different from your model. How does that help us?
- then they seem to say that setting up VLAN and ACL to control communication is coming in a new release of software.
So I guess you wait for the new version of software and see what is really in it.
I asked about whether tplink could do DHCP for multiple subnets. You ask "By this you mean like providing dhcp for each port?" Not necessarily based on port. If you have vlans 10, 20 , and 30 where each vlan has its own unique IP subnet and all are connected to the LAN port of tplink then there will need to be 3 DHCP pools all on that one port.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2021 02:52 PM
I share your concerns too.
You know what? let's just take the router out of the picture because I feel it will do more harm than good. The software is not "good", the user manual is "meh", and the support is...
Anyways, let's just scratch all and begin from the network 192.168.0.0/23, and work with the switches instead, whatever needs to go to the internet, will be via trunk with no vlan capability, plain simple, let's assume is just a dummy router with no useful features.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2021 04:01 PM
Unfortunately having a dummy router with no useful features is a problem. If you are using private IP address space (192.168.0.0 is private/not registered address space) and you want to get to the Internet (which requires Public IP address to access) then you need something to do address translation. Your 2960 switches can not do address translation. So you need some device to do that address translation. Devices to do that are usually either routers or firewalls.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2021 04:42 PM
I see your point.
This is from the user manual on the "vlan configuration" section:
The router supports 802.1Q VLAN, which can divide a LAN into multiple logical LANs.
Each logical LAN is a VLAN. Hosts in the same VLAN can communicate with each other.
However, hosts in different VLANs cannot communicate directly. Therefore, broadcast
packets can be limited to within the VLAN.
Specs: https://www.tp-link.com/us/business-networking/load-balance-router/tl-r470t+/#specifications (altough I do not see anything useful there)
As for 802.1.q seems supported somehow: https://www.tp-link.com/us/support/faq/2246/
So, apparently, it supports vlans, and vlan routing, so that means with the right configuration, I can get the vlans to work with the 2960's and this router.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2021 01:37 AM
The links you provide are interesting. It does appear that your tplink does support trunking with vlan tags. I note that the document seems to say that the tplink would provide each configured vlan access to the Internet but would not provide vlan to vlan communication. Looking at the original post for what you want to achieve I see this "Separate the guest from the office, and have a little more network privacy and security." It looks like it would work to have one vlan for guest and another vlan for office. I am not sure that it would work to have one vlan for users and a different vlan for servers.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2021 10:09 AM - edited 05-29-2021 10:12 AM
In that case then just two vlans, one for guest and another for the clinic itself, no hassle, no sweating, no complication.
I will take the 192.168.1.0/23 side for guest and the 192.168.0.0/23 for the clinic (or what is the other way around?, anyways).
One port on the router will be for guest vlan, and the other port for the clinic. So that would be one switch on each port.
Via trunk I will only send the mgmt vlan so I can have access to all switches.
And I guess that will be it, easy, right? meanwhile I will push to get a decent cisco router/balancer, nothing new, something old that is economical, just to show them that getting better hardware is the right direction.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2021 12:55 PM
You suggest having 2 vlans, one for guest and one for clinic. That certainly should work and you have several options of how to achieve it. You also talk about a management vlan. So is it 2 vlans you want to have or is it 3?
One approach would be to connect your switch(s) to multiple ports on tplink. If I am understanding their document correctly tplink would let you connect to 2 or to 3 ports on tplink for connecting the vlans. You could connect an access port in the guest vlan to one tplink port, connect an access port in the clinic vlan to another tplink port, and connect an access port in the management vlan to a third tplink port. Each tplink port would be configured for the subnet of that particular vlan. With this approach there is no trunk and there is not any vlan tagging.
A different approach would be to connect one switch interface to a tplink port. This switch port would be configured as a trunk and would carry all 2 or 3 vlans. The tplink port would be configured for vlan tagging and would have tags specified for the guest vlan, for the clinic vlan , and for the management vlan.
In either of these approaches I believe that tplink would be configured with DHCP pools for each vlan subnet and would be configured to add address translation for at least the guest and clinic vlans.
One thing I have mentioned before but it seems you do not yet understand it. Using the /23 mask is not correct. If you define a network as 192.168.1.0/23 and a network as 192.168.0.0/23 they are both really the same network. Instead of using /23 I would suggest that you use /24 or perhaps even /25. How many addresses do you need in each of these networks. With a /24 mask you will have 254 addresses that you can use. With /25 you would have 126 addresses that you can use.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2021 11:06 AM
Sorry, is it true /23 is a whole network, I keep forgetting that, sorry again.
Back to drawing board. I was thinking about the sceanario of having both the office and the dicom network togheter, is not ideal but it could work.
Again, the problem is that the tplink device does not have the capability of multiple dhcp pools, I have the r470t model. The model that has multi nat (or multiple dhcp for tplink) is the r480t, which I do not have.
So I'm stuck with just one dhcp pool for the whole clinic, that's why I keep saying wrongly to divide the network between 192.168.0.0 192.168.1.0, sorry about that. The only way to do that is to have a /24 for each segment, but I do not have a multi dhcp pool router on the site.
I "had" one multi dhcp pool device, from netgear, but that thing is so ancient that this whole problem started when that old router started to lock up when the new internet connection was added, the max throughoutput that it had was like 65mbps and it still locked up, and got hot, probably it has a few bad capacitors but no one would fix it.
I think this whole case can be summarized in one question, if I do not have a multi-dhcp-pool capable appliance, can I implement several vlans in the same network by segmenting them? keeping in mind that:
- the appliance can do vlan tagging per port but no vlan routing,
- meaning that if I set my only dhcp pool to 192.168.1.0/23, I can have a vlan on port 3 (for example) for the guest (which will be 192.16.0.0), and use port 4 for all the reserved dhcp address (those would be 19168.1.0), and I have to make sure to connect the office to the correct swtich and the same for the guest,
- also knowing that altough is the same network, the device cannot do vlan routing, so that would also mean isolating the switches so they do not have a connection between them except via the non-multi-dhcp-pool router.
Because besides the fact that I do not have any multi-dhcp-pool-capable router at hand, I do not know what else I can do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2021 02:33 PM
I had not correctly understood the limitations of the tplink that you have. They talk about doing vlans, but as I read some of the user manual I found through the link you provided I discover that this is the ability on each of their ports to enable a vlan tag on Ethernet frames or not tag Ethernet frames for a port. But it does appear that the LAN port would have a single vlan tag (would not support a trunk with multiple vlans) and has a single DHCP scope. Given these limitations I do not see that there is much you can do to separate traffic for guest and for clinic. Replacing hubs with switches is a significant improvement for the network. And having switches in the network will position you to be able to do other things to improve the network when management will allow you to replace tplink with a more capable device.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
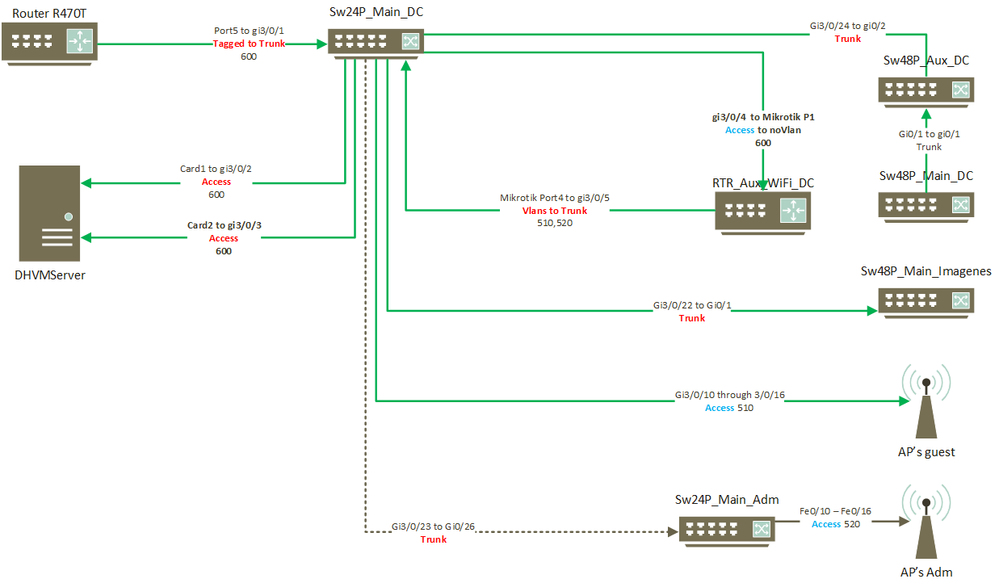
12-24-2022 09:28 AM
Folks, it's been a long time and I wanted to give closure to this case.
Here is the final and current diagram of the solution I was able to come up with, I added a vlan capable router (Mikrotik hAP lite) just to control the wifi traffic and left the R470T to do WAN balancing/failover for the whole network. That simplified a lot the config and also gave me more options to secure the network.
So far, I have also been able to route traffic when needed between vlans securely with the firewall of the Mikrotik so only designated clients can go back and forth.
And I also was able to setup a syslog and Zabbix. I also wanted to share the pictures of the rack before and after but misplaced the files. I promise if I find them I will post them.
Again, thanks a lot everyone. Yes, this project is far from finished but so far the place is more secure, bandwith is now fairly controlled and users and management are happy.
And no... I haven't been paid yet
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide