- Cisco Community
- Technology and Support
- Networking
- Switching
- WAN and LAN separated by VLAN on the same core switch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
WAN and LAN separated by VLAN on the same core switch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2015 04:50 AM - edited 03-08-2019 02:43 AM
What do you think about the security of this architecture?
I have two ISP connected to a core-switch in two VLAN which are shared with the firewall. The LAN VLAN is also connected to this core-switch.
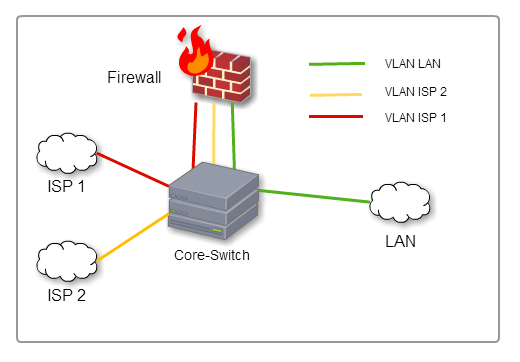
To me, it is a security breakthrough. Isn't it?
Thank you
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2015 05:01 AM
I have seen some people argue it is fine but for me it is an accident waiting to happen.
To get to the internal network you have to go via the firewall so it is protected but your core switch isn't.
So any traffic from the internet goes through the core switch before getting to your firewall which means a denial of service attack, for example, is going to hit the switch first.
I don't have an issue with using the core switch for internal and DMZs but no traffic should be going to it without going through the firewall first.
Like I say though, I have seen others argue it is fine if you use the appropriate security measures.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2015 05:54 AM
Disclaimer
The Author of this posting offers the information contained within this posting without consideration and with the reader's understanding that there's no implied or expressed suitability or fitness for any purpose. Information provided is for informational purposes only and should not be construed as rendering professional advice of any kind. Usage of this posting's information is solely at reader's own risk.
Liability Disclaimer
In no event shall Author be liable for any damages wha2tsoever (including, without limitation, damages for loss of use, data or profit) arising out of the use or inability to use the posting's information even if Author has been advised of the possibility of such damage.
Posting
As Jon says, what you're doing is debatable. Personally, it's the kind of thing I'm willing to do, but Jon is 100% correct, it can be an accident waiting to happen. Regarding such possible accidents, you got to realize the additional risk of connecting any device to the Internet, and treat it with the care it deserves.
Understand such a design exposes your core switch to any and all attacks on its "external" facing interfaces, as they are on the "outside" of the FW. However, if you run those interfaces as pure L2, your switch will be pretty much transparent and, if the switch works correctly, difficult to break into. Perhaps your biggest concern would be some kind of VLAN hopping attack.
If you run the external interfaces as L3, you futher expose your core switch to external attack, but correctly configured interfaces (for security) would mitigate the risk. However, again, as Jon noted, this would be more of an accident waiting to happen, i.e. you "accidentally" start routing traffic between inside and outside without going through the firewall.
From what your diagram shows, why wouldn't you just connect the two ISPs directly to the two FW ports? Are the external VLANs going to host public servers outside the FW? If so, generally you would host them behind a FW on a DMZ VLAN/subnet.
If for some reason, you need switch ports on the outside of the FW, a small L2 or L3 switch would be a good investment from a security perspective. I.e. traffic must transit the FW, there's no physical alternative path.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2015 08:48 AM
Hello,
Just adding to others.
it should be fine If you have only three VLANs, and core switch just switch between those three vlans. However, in real network, you have some trunk interfaces connecting your core switch to LAN depending on your configuration. Traffic from ISP1 and 2 goes to the LAN on trunk interfaces making your LAN vulnerable. Your core switch is also vunerable to DOS attack.
In my opinion, firewall should be placed between ISP1 and ISP 2 in outside zone and switch in inside zone. You can create a server zone also to protect your servers. If firewall is a module, it can be easily placed between all the traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2015 10:48 AM
Hello Tom,
Recommended practice is to have IPS setup in inline mode between ISP and Core switch and have DDOS as service from your ISP as well.
By having above two you can at least save your core switch exposed to internet for attack. As these type of setup is cost saving or may the requirement from client to merge everything in single switch.
Hope it Helps..
-GI
Rate if it Helps..
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide