- Cisco Community
- Technology and Support
- Security
- VPN
- Cisco ASA: Dual ISP VPN redundancy.....
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2011 05:47 PM
Hello, if there anyway to configure site-to-site vpn redundancy using a cisco asa. I know that I can configure redundancy using two ISP on my cisco ASA but pointing to the same peer, but what about if I need to point to different peers but to protect the same networks...
I know that this is possible in the routers using tunnels gre + ipsec or VTI, but if there anyway to something similar using cisco ASA?
Any help will be appreciated! Thanks!
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2011 10:40 AM
Hello,
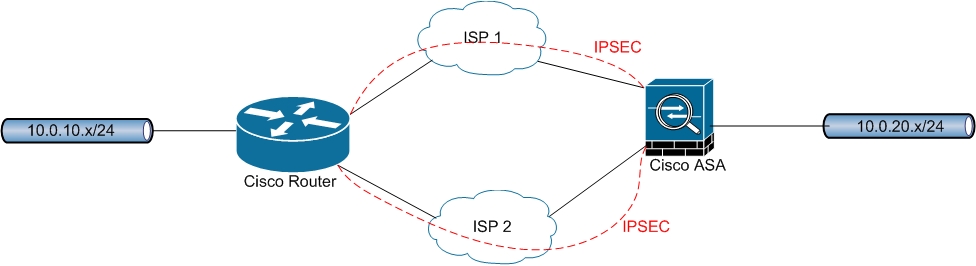
Yes, Nagiswaren is right. For example you have this:
Based on the above image and your replies you would need to setup something like this:
Interface Name IP address Subnet mask Method
Ethernet0/0 outsideVPN 10.198.16.143 255.255.255.224 manual
Ethernet0/1 inside 172.31.255.1 255.255.255.0 manual
Ethernet0/2 outside-VPN2 10.198.29.21 255.255.255.224 manual
Ethernet0/3 INTERNET 12.12.12.12 255.255.255.224 manual
access-list 155 extended permit ip 10.0.20.0 255.255.255.0 10.0.10.0 255.255.255.0
access-list nonat extended permit ip 10.0.20.0 255.255.255.0 10.0.10.0 255.255.255.0
nat (inside) 0 access-list nonat
crypto ipsec transform-set 3DES-MD5 esp-3des esp-md5-hmac
crypto map mymap 10 match address 155
crypto map mymap 10 set peer 1.1.1.1 2.2.2.2
crypto map mymap 10 set transform-set 3DES-MD5
crypto map mymap interface outsideVPN
crypto map mymap interface outside-VPN2
crypto isakmp enable outsideVPN
crypto isakmp enable outside-VPN2
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
tunnel-group 1.1.1.1 type ipsec-l2l
tunnel-group 1.1.1.1 ipsec-attributes
pre-shared-key cisco123
tunnel-group 2.2.2.2 type ipsec-l2l
tunnel-group 2.2.2.2 ipsec-attributes
pre-shared-key cisco123
=============================================================================================
OBJECT TRACKING
track 100 rtr 10 reachability
sla monitor 10
type echo protocol ipIcmpEcho 4.2.2.2 interface outsideVPN
num-packets 3
frequency 10
sla monitor schedule 10 life forever start-time now
route INTERNET 0.0.0.0 0.0.0.0 12.12.12.1 1
route outsideVPN 1.1.1.1 255.255.255.255 10.198.16.129 1 track 100
route outsideVPN 2.2.2.2 255.255.255.255 10.198.16.129 1 track 100
route outsideVPN 10.0.10.0 255.255.255.0 10.198.16.129 1 track 100
route outsideVPN 4.2.2.2 255.255.255.255 10.198.16.129 1
route outside-VPN2 1.1.1.1 255.255.255.255 10.198.29.1 254
route outside-VPN2 2.2.2.2 255.255.255.255 10.198.29.1 254
route outside-VPN2 10.0.10.0 255.255.255.0 10.198.29.1 254
I used 4.2.2.2 but you could use the ISP1 IP address.
==========================ROUTER===================================================================
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
access-list 133 permit ip 10.0.10.0 0.0.0.255 10.0.20.0 0.0.0.255
crypto isakmp key cisco123 address 10.198.16.143 no-xauth
crypto isakmp key cisco123 address 10.198.29.21 no-xauth
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto map primary-map 10 ipsec-isakmp
set peer 10.198.16.143
set peer 10.198.29.21
set transform-set ESP-3DES-SHA
match address 133
crypto map secondary-map 10 ipsec-isakmp
set peer 10.198.16.143
set peer 10.198.29.21
set transform-set ESP-3DES-SHA
match address 133
interface FastEthernet0
ip address 1.1.1.1 255.255.255.0
crypto map primary-map
interface FastEthernet1
ip address 2.2.2.2 255.255.255.0
crypto map secondary-map
Interface Vlan1 *** inside interface ***
ip address 10.0.10.1 255.255.255.0
ip sla monitor 1
type echo protocol ipIcmpEcho 4.2.2.2
timeout 1000
frequency 3
threshold 2
ip sla monitor schedule 1 life forever start-time now
track 123 rtr 1 reachability
ip route 4.2.2.2 255.255.255.255 1.1.1.254 permanent
ip route 10.198.16.143 255.255.255.255 1.1.1.254 1 track 123
ip route 10.198.29.21 255.255.255.255 1.1.1.254 1 track 123
ip route 10.0.20.0 255.255.255.0 1.1.1.254 1 track 123
ip route 10.198.16.143 255.255.255.255 2.2.2.254 200
ip route 10.198.29.21 255.255.255.255 2.2.2.254 200
ip route 10.0.20.0 255.255.255.0 2.2.2.254 200
---josemed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2011 08:10 PM
Hello,
It's actually going to be the same thing. All you need to do is to setup your routing correctly at the remote end, just configure object tracking as well on the Router, set two peers under the static cryptomap and don't forget the two isakmp key addresses. On the ASA the configuration will be the same (Floating routes, crypto map with a secondary peer and a tunnel-group for each peer as well). A good idea is to enable periodic DPDs on the Router.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2011 08:48 PM
Hello Jose,
Thanks for your answer. Still I have a doubt:
Assuming that WANs routers between the ASA and the router are OK:
(ASA ISP 1 address <--> Router ISP 1 address)
(ASA ISP 2 address <--> Router ISP 2 address)
Then I need to set up two static routes with different costs on the ASA pointing to the LAN behind the router, and again, two routes with different costs on my router pointing to the LAN subnet behind the ASA. In order to track the static routes I need to configure object tracking on both endpoints. OK, but how I would configure my interesting traffic on the access-list of the IPSec?
“permit ip 10.0.20.0 255.255.255.0 10.0.10.0 255.255.255.0” ?
But, considering that the ASA has version 8.0.5, I don´t understand how it would track the LAN subnet behind the router considering that the object tracking on the ASA would use the ISP 1 or ISP 2 WAN ip address as source address of the probes.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2011 09:08 PM
Yes, the intereseting traffic should be as you mentioned it on the ASA side and mirrored at the Router side. It depends on how you have the routing configured, are you relying on the default gateway or do you have static routes to the remote LAN pointing to the next-hop (not very likely) remember that the ASA associates a static route with a monitoring target that you define. The SLA will be monitoring the target with periodic ICMP. If an echo reply is not received, the object is considered down, and the associated route is removed from the routing table. A previously configured backup route is used in place of the route that is removed. While the backup route is in use, the SLA monitor operation continues to try to reach the monitoring target. Once the target is available again, the first route is replaced in the routing table, and the backup route is removed. ASA will use ISP 1 or ISP 2 WAN ip address as source address of the probes but it should be tracking the main ISP address. Does that help? Also I see there is a recent blog post regarding DUAL ISP VPN redundancy https://supportforums.cisco.com/community/netpro/security/vpn/blog/2011/04/25/ipsec-vpn-redundancy-failover-over-redundant-isp-links
If something is not clear just let me know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2011 09:37 PM
Thanks again, I need to clarify something here. The ASA has three ISP, where ISP 1 and ISP 2 are used only for VPN traffic and the default route is through the ISP 3.
So, I can track ISP 1 and ISP 2 ip address of the router through ISP 1 or ISP 2 interfaces of the ASA, here is no problem, but I could not monitor the static routes pointing to the LAN subnet behind the router cause the ASA would try to reach this segment using its own ISP 1 or ISP 2 ip address without encrypting the traffic. Am right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2011 10:30 PM
Hi pederson,
By default ASA will auto failover to 2nd peer IP if the 1st peer IP is nt reacheble. You dont need to track availability of Peer IP. What u need to track is is ASA own WAN link. Just track only your Main WAN link by IP SLA, and you should have 2nd default route using Static Float routing with Matric for eg, 0.0.0.0 0.0.0.0 backupWANIP 200 . So once ASA detect Track down, it will auto failover to 2nd WAN link. This same setup should applied to remote end.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2011 10:40 AM
Hello,
Yes, Nagiswaren is right. For example you have this:
Based on the above image and your replies you would need to setup something like this:
Interface Name IP address Subnet mask Method
Ethernet0/0 outsideVPN 10.198.16.143 255.255.255.224 manual
Ethernet0/1 inside 172.31.255.1 255.255.255.0 manual
Ethernet0/2 outside-VPN2 10.198.29.21 255.255.255.224 manual
Ethernet0/3 INTERNET 12.12.12.12 255.255.255.224 manual
access-list 155 extended permit ip 10.0.20.0 255.255.255.0 10.0.10.0 255.255.255.0
access-list nonat extended permit ip 10.0.20.0 255.255.255.0 10.0.10.0 255.255.255.0
nat (inside) 0 access-list nonat
crypto ipsec transform-set 3DES-MD5 esp-3des esp-md5-hmac
crypto map mymap 10 match address 155
crypto map mymap 10 set peer 1.1.1.1 2.2.2.2
crypto map mymap 10 set transform-set 3DES-MD5
crypto map mymap interface outsideVPN
crypto map mymap interface outside-VPN2
crypto isakmp enable outsideVPN
crypto isakmp enable outside-VPN2
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
tunnel-group 1.1.1.1 type ipsec-l2l
tunnel-group 1.1.1.1 ipsec-attributes
pre-shared-key cisco123
tunnel-group 2.2.2.2 type ipsec-l2l
tunnel-group 2.2.2.2 ipsec-attributes
pre-shared-key cisco123
=============================================================================================
OBJECT TRACKING
track 100 rtr 10 reachability
sla monitor 10
type echo protocol ipIcmpEcho 4.2.2.2 interface outsideVPN
num-packets 3
frequency 10
sla monitor schedule 10 life forever start-time now
route INTERNET 0.0.0.0 0.0.0.0 12.12.12.1 1
route outsideVPN 1.1.1.1 255.255.255.255 10.198.16.129 1 track 100
route outsideVPN 2.2.2.2 255.255.255.255 10.198.16.129 1 track 100
route outsideVPN 10.0.10.0 255.255.255.0 10.198.16.129 1 track 100
route outsideVPN 4.2.2.2 255.255.255.255 10.198.16.129 1
route outside-VPN2 1.1.1.1 255.255.255.255 10.198.29.1 254
route outside-VPN2 2.2.2.2 255.255.255.255 10.198.29.1 254
route outside-VPN2 10.0.10.0 255.255.255.0 10.198.29.1 254
I used 4.2.2.2 but you could use the ISP1 IP address.
==========================ROUTER===================================================================
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
access-list 133 permit ip 10.0.10.0 0.0.0.255 10.0.20.0 0.0.0.255
crypto isakmp key cisco123 address 10.198.16.143 no-xauth
crypto isakmp key cisco123 address 10.198.29.21 no-xauth
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto map primary-map 10 ipsec-isakmp
set peer 10.198.16.143
set peer 10.198.29.21
set transform-set ESP-3DES-SHA
match address 133
crypto map secondary-map 10 ipsec-isakmp
set peer 10.198.16.143
set peer 10.198.29.21
set transform-set ESP-3DES-SHA
match address 133
interface FastEthernet0
ip address 1.1.1.1 255.255.255.0
crypto map primary-map
interface FastEthernet1
ip address 2.2.2.2 255.255.255.0
crypto map secondary-map
Interface Vlan1 *** inside interface ***
ip address 10.0.10.1 255.255.255.0
ip sla monitor 1
type echo protocol ipIcmpEcho 4.2.2.2
timeout 1000
frequency 3
threshold 2
ip sla monitor schedule 1 life forever start-time now
track 123 rtr 1 reachability
ip route 4.2.2.2 255.255.255.255 1.1.1.254 permanent
ip route 10.198.16.143 255.255.255.255 1.1.1.254 1 track 123
ip route 10.198.29.21 255.255.255.255 1.1.1.254 1 track 123
ip route 10.0.20.0 255.255.255.0 1.1.1.254 1 track 123
ip route 10.198.16.143 255.255.255.255 2.2.2.254 200
ip route 10.198.29.21 255.255.255.255 2.2.2.254 200
ip route 10.0.20.0 255.255.255.0 2.2.2.254 200
---josemed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2011 11:53 AM
Thanks for your help Jose and Nagiswaren, I would try this.
Regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
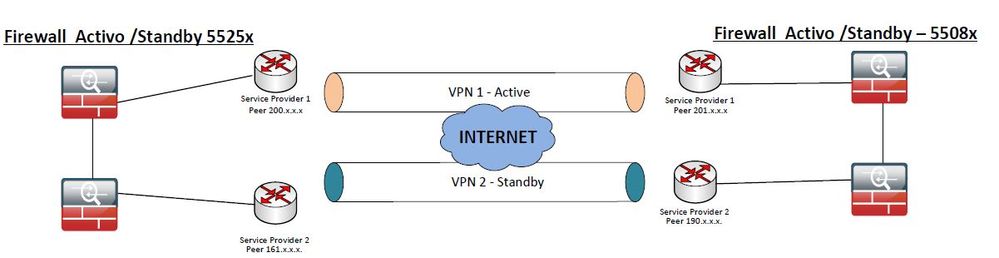
06-08-2019 10:06 PM
@e.pedersen wrote:Thanks for your help Jose and Nagiswaren, I would try this.
Regards!
Hi Experts
I have this scenario, we currently have a VPN Site to Site with some ASA 5508x already active with my Service Provider 1 and I want to configure the contingency with another Peer (New Public IP) with my Service Provider 2,
There is some additional configuration that you have to put in the ASA.
I have only declared the following statement adding the 2nd public ip from the other end of the ASA, here the configuration:
crypto map outside_map 1 match address outside_cryptomap_3
crypto map outside_map 1 set pfs group5
crypto map outside_map 1 set peer 201.x.x.x 190.x.x.x
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA
crypto map outside_map 1 set ikev2 pre-shared-key *****
crypto map outside_map 1 set security-association lifetime seconds 28800
crypto map outside_map 1 set df-bit set-df
Our test will be to disconnect the internet from 1 end and see if it commutes with the other internet 2 link or is there something that I need to configure in the ASA?
Thank you in advance for your help if you have faced a simulated scenario
Regards.
Carlos P.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide