- Cisco Community
- Technology and Support
- Security
- VPN
- Allow Changing of user passwords through PIX with IAS Radius and
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Allow Changing of user passwords through PIX with IAS Radius and Cisco VPN Client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2012 02:26 PM
We have a windows 2003 DC running IAS. We are currently using this setup to authenticate VPN users connecting through a PIX firewall and Cisco VPN Client. This setup works fine. I would like the VPN client though to prompt users when their passwords expire and allow the users to change their passwords when they do. It seems this can be done somehow but I cannot get it to work. I am told you need to enable MS-CHAP v1 or 2 for the Dial-In profile authentication in IAS to make this fly and add the 'password-management' to the general attributes of the tunnel group. I have done both of these things but when I do I cannot even get the user to authenticate at all, much less allow them to change their passwords. I have read a lot of posts describing how to do this but no one seems to have any success. Can this be done? I have tried declaring the ppp attributes and including MS-CHAP-V2 authentication command as well as leaving it out. I also tried to also enable ms-chap-v1 as well as v2. Either way I get an IAS error of the following:
IAS_INVALID_AUTH_TYPE
Here is the relevant configuration on the PIX and within IAS:
Cisco PIX Security Appliance Software Version 8.0(4)24
aaa-server radius protocol radius
aaa-server radius (inside) host dc1-int
key <key>
aaa-server radius (inside) host dc2-int
key <key>
group-policy company-admin internal
group-policy comapny-admin attributes
wins-server none
dhcp-network-scope none
vpn-access-hours none
vpn-simultaneous-logins 20
vpn-idle-timeout 30
vpn-session-timeout none
vpn-tunnel-protocol IPSec
ip-comp disable
re-xauth disable
group-lock none
pfs enable
split-tunnel-policy tunnelspecified
split-tunnel-network-list value company-admin-split-tunnel
tunnel-group company-admin type remote-access
tunnel-group company-admin general-attributes
address-pool company-admin
authentication-server-group radius LOCAL
default-group-policy company-admin
password-management
tunnel-group company-admin ipsec-attributes
pre-shared-key *
Like I mentioned, this works if I do not enable MS-CHAP-v2 on the server and remove the password-management on the PIX. The end result I am looking for is to allow users to change their passwords via the VPN client, but I cannot seem to even authenticate them at all. Any help would be great.
Thanks in advance
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2012 07:01 PM
Hi,
Could you please try with MS-CHAP?
Thanks.
Portu.
Please rate any helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2012 06:42 AM
I have tried with ms-chap. IAS log just shows invalid auth type. On the PIX if I do the following:
tunnel-group company-admin ppp--attributes
authentication ms-chap-v1
When I view the configuration those command do not show up. The only thing that shows up is ms-chap-v2. Right now there is nothing there even though per your request I placed the ms-chap-v1 command in there. The password-management command is still there in the general attributes. Thats required to get the user passwords to be able to be changed correct? What am I missing here? Thanks for the help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2012 07:01 AM
You do not need to modify any PPP attributes on the ASA, since you are connecting with the Cisco VPN client.
Please try with MS-CHAP and MS-CHAPv2 on the IAS server.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2012 07:54 AM
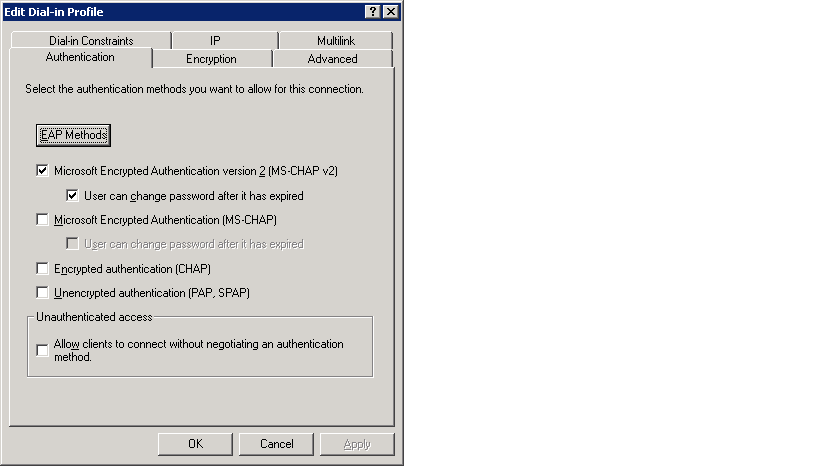
I did try this. See the screentshot from IAS server:

I get an 'invalid_auth' error in the IAS log. IF I put in a known incorrect password then it shows a failed authentication attempt in the IAS log. If I put in the correct password I get an invalid auth message in the log. Thanks for the help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2012 12:53 PM
OK I think I got the chap thing figured out. I had another policy on the IAS server which was configured to use ms-chap-v1. My login attemps were hitting that polciy instead of the VPN policy I had set up to use ms-chap-v1. I added the "Authentication-Type-matches "MS-CHAP v1" to the policy conditions and was able to authenticatate. Now I am testing the password funcionality within the VPN client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2012 01:40 PM
OK I spoke too soon. The user looked like it was working but it was working because it matched another IAS policy further down the list. It seems as though the PIX refuses to use ms-chap of any sort. If I include the authentication type in the VPN policy conditions as ms-chap, it skips the VPN policy I am using to authenticate this. If I remove it, then it gives an invalid authentication type as if whatever the PIX is sending the IAS server does not understand as ms-chap.
It seems like the PIX authentication is totally wrong for use with IAS. What else do I need to add to this configuration to gewt it to work with ms-chap of any kind? I really don't get it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2012 01:50 PM
At this point it would be better to open a TAC case to speed up the resolution of this issue, since we could fix it in a WebEx session.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2012 02:34 PM
OK I have this working. The fix is rather embarrasing though. I had this working all along. I have two different group authentication configurations setup on this PIX. The test connection I was using used a group authentication which was opposite of the one I was applying the password management configurations to. I added those to the right group and everything worked as described. Thanks for the help and very sorry for the time waste. Devil is in the details.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2012 07:27 AM
I am glad to know that it works now.
Please mark this question as answered and rate any helpful post.
Portu.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide