- Cisco Community
- Technology and Support
- Security
- VPN
- Re: AnyConnect and machine certificate authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2021 04:54 AM
Thanks to this group, I was able to get user certificate authentication working yesterday.
However, machine certificate authentication is still not working and I get a "no valid certificate available for authentication" error when trying to use the AnyConnect XML profile I configured for this.
Looking through the DART logs (See below), it seams like AnyConnect are unable to either find the certificate in the local computer certificate store or don't have the correct permission to search it. I've verified that the certificate is there.
The AnyConnect XML profile is configured with the following relevant parameters:
<AutomaticCertSelection UserControllable="false">true</AutomaticCertSelection>
<CertificateStore>Machine</CertificateStore>
<CertificateStoreOverride>true</CertificateStoreOverride>
<CertificateMatch>
<MatchOnlyCertsWithKU>false</MatchOnlyCertsWithKU>
<DistinguishedName>
<DistinguishedNameDefinition Operator="Equal" Wildcard="Disabled" MatchCase="Disabled">
<Name>ISSUER-CN</Name>
<Pattern>firepower-DC01-CA</Pattern>
</DistinguishedNameDefinition>
For the computer certificate templeate, I followed this guide http://www.network-node.com/blog/2015/12/24/server-2012-configuration-certificate-templates and it's configured to use both Server Authentication and Client Authentication and the computer have the right to enroll and auto enroll.
I've also tried to run AnyConnect as an administrator, but that doesn't work either.
I did run DART to collect some logs and here's the different errors I see in the event log when connecting:
Invoked Function: CVerifyServerName::VerifyCertName
Return Code: -31391725 (0xFE210013)
Description: CERTIFICATE_ERROR_VERIFY_NAME_FAILED
Invoked Function: ITransportCB::OnPeerCertVerificationError
Return Code: -31391704 (0xFE210028)
Description: CERTIFICATE_ERROR_VERIFY_SERVERCERT_FAILED:Server certificate verification failed, and the error was not an askuser error
Function: CTransportCurlStatic::SendRequest
File: c:\temp\build\thehoff\orion_mr40.736949158386\orion_mr4\vpn\api\ctransportcurlstatic.cpp
Line: 2042
CURL error: 60 = SSL certificate verification failed
Invoked Function: Certificate Error
Return Code: -31391704 (0xFE210028)
Description: CERTIFICATE_ERROR_VERIFY_SERVERCERT_FAILED:Server certificate verification failed, and the error was not an askuser error
Translated to CTRANSPORT_ERROR_PEER_CERT
Return Code: -29949920 (0xFE370020)
Description: CTRANSPORT_ERROR_PEER_CERT
AnyConnect cannot confirm it is connected to your secure gateway. The local network may not be trustworthy. Please try another network
File: c:\temp\build\thehoff\orion_mr40.736949158386\orion_mr4\vpn\api\connectmgr.cpp
Line: 16925
Certificate authentication requested from gateway, no valid certs found in users cert store.
Certificate name verification has failed.
Server Name:
<VPN server name>
Subject Alternate Name(s):
ftd01
Invoked Function: CVerifyServerName::VerifyCertName
Return Code: -31391725 (0xFE210013)
Description: CERTIFICATE_ERROR_VERIFY_NAME_FAILED
Is there anything else I could verify
Thanks
/Chess
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2021 08:27 AM
Hi @Chess_N,
Override option is meant for users who are not logged in as power users (if you ask me, noone should be logged in as admin). This gives AnyConnect power to access machine credentials store via service account, and not to depend on user elevation. However, this change does require to reboot your PC (not sure, maybe restart of AnyConnect service is also sufficient). Have you done that after modification of XML profile?
But your initial problem appears to be on the headend side. based on provided logs:
Invoked Function: CVerifyServerName::VerifyCertName
Return Code: -31391725 (0xFE210013)
Description: CERTIFICATE_ERROR_VERIFY_NAME_FAILED
Invoked Function: ITransportCB::OnPeerCertVerificationError
Return Code: -31391704 (0xFE210028)
Description: CERTIFICATE_ERROR_VERIFY_SERVERCERT_FAILED:Server certificate verification failed, and the error was not an askuser error
It appears that your PC is failing to verify your ASA/FTD certificate. If you configured an IP address in your XML profile, then your cert must match it (you must add IP in SAN field). Easiest 'cheating' is for you to issue certificate for some FQDN, configure your profile for same FQDN, and then you modify hosts file locally on the PC.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2021 06:07 AM
Hi @Chess_N
Can you please enable console debugs for "webvpn" and "ssl", go to "system support diagnostics-cli" , then attempt to authentication and view the output of the debugs. Those debugs should hopefully provide enough information to troubleshoot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2021 06:15 AM
Hi,
Unfortunatly, the debug doesn't give much info.
ftd01# debug ssl 255
ftd01# debug webvpn 255
I only see this when connecting with the machine cert profile:
ftd01# Public archive directives retrieved from cache for index 1.
Connecing with the working user cert profile gives me lot of output, but that is expected.
Thanks
/Chess
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2021 06:58 AM - edited 08-10-2021 06:59 AM
I was finally able to get it to work with the machine certificate, but the solution is a bit confusing.
I changed the XML profile to <CertificateStoreOverride>false</CertificateStoreOverride> instead of "true". I am quite sure that it should be set to "true" and not "false", in order for AnyConnect to be able to read the computer cert store, so I am not sure why changing it to "false" made it work. Also, I needed to run the AnyConnect client as an Administrator.
/Chess
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2021 08:27 AM
Hi @Chess_N,
Override option is meant for users who are not logged in as power users (if you ask me, noone should be logged in as admin). This gives AnyConnect power to access machine credentials store via service account, and not to depend on user elevation. However, this change does require to reboot your PC (not sure, maybe restart of AnyConnect service is also sufficient). Have you done that after modification of XML profile?
But your initial problem appears to be on the headend side. based on provided logs:
Invoked Function: CVerifyServerName::VerifyCertName
Return Code: -31391725 (0xFE210013)
Description: CERTIFICATE_ERROR_VERIFY_NAME_FAILED
Invoked Function: ITransportCB::OnPeerCertVerificationError
Return Code: -31391704 (0xFE210028)
Description: CERTIFICATE_ERROR_VERIFY_SERVERCERT_FAILED:Server certificate verification failed, and the error was not an askuser error
It appears that your PC is failing to verify your ASA/FTD certificate. If you configured an IP address in your XML profile, then your cert must match it (you must add IP in SAN field). Easiest 'cheating' is for you to issue certificate for some FQDN, configure your profile for same FQDN, and then you modify hosts file locally on the PC.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2021 04:55 AM - edited 08-11-2021 05:13 AM
Yes, the problem was with the certificate on the FTD and using wrong FQDN in the CSR.
When I did the Cert Enrollment from the FMC, I used the VPN address as CN. Also - by default - the enrollment includes the device hostname as a FQDN and this was the issue. When connecting to the VPN address, it ignored the CN field in the certificate, and only used the FQDN name field and that's why I also got a certificate warning when typing the VPN address in my browser.
At this point I could still use the Machine certificate, but I needed to run the VPN client as administrator and also set the CertificateStoreOverride in the VPN profile XML to "false"
So I created a new CSR, but this time I selected a Custom FQDN and used the VPN address instead of the device name.
After installing the new certificate, I opened a browser and typed in the VPN address - no more certificate warnings.
And best of all, I was now able to use the machine certificate without having to run the AnyConnect client as administrator. This worked after I changed the CertificateStoreOverride in the VPN profile XML back to "true".
So everything is working now, but I'm still a bit curious on why I needed to use the FQDN parameter and not the CN. Is this something that could be adjusted in the VPN profile or should I always use a custom FQDN with the same name as the VPN address?
BR
/Chess
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2021 07:11 AM
Hi @Chess_N,
I'm not sure how your certificate looked like, but, there is a caveat from few years back, that most modern browsers are actually not looking into CN field, but in SAN, and they are expecting DNS name (and also IP address if in use, but I rarely see IPs these days) to be defined in SAN. In that case, same FQDN gets defined in both CN and SAN (of course, SAN can contain multiple entries).
I also recommend using OpenSSL for certificate generation, as from there you are very flexible what can you define, and how it should look like. Once you are happy, you can again use OpenSSL to reassemble private key, certificate and CA chain into a file that can be imported to ASA/FTD.
Normally, you create one DNS record for your ASA/FTD, you purchase (you can use internal PKI too) certificate for that FQDN (or a wildcard one), and then you configure same under XML profile (and also under tunnel-group, if you want to enable that too). Certificate will have same DNS name in both CN and SAN.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2021 12:34 AM
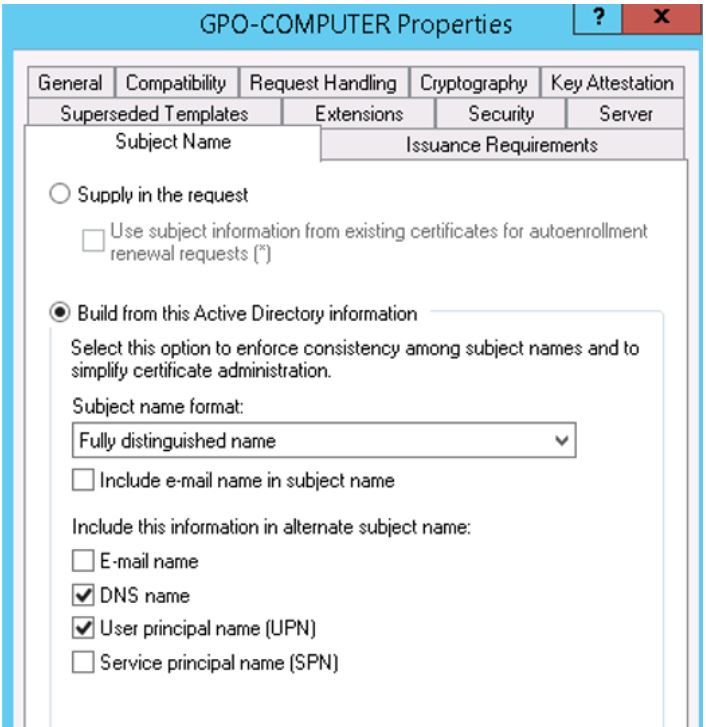
Thanks, I was looking at the template for the machine certificate in the Microsoft Cert server and found an option there to change the subject name format from fully distinguished name to common name. I'll might try that at a later time.
BR
/Chess
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide