- Cisco Community
- Technology and Support
- Security
- VPN
- Also is there a way to import
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2015 03:27 PM - edited 02-21-2020 08:22 PM
Hello and thank you for reading.
This is a new configuration and I need support. I do have TAC support but it has not proven successful.
Internet - > Cisco ASA -> Juniper SRX -> Extreme L3 SW -> PCA
What I have done so far is install the latest AnyConnect images - anyconnect-macosx-i386-3.1.09013-k9.pkg
and running asa916-6-k8.bin
Please help with the configuration, with the IP space shown, I have last octet available for public space .184, .185, I have drawn the network in question. See picture.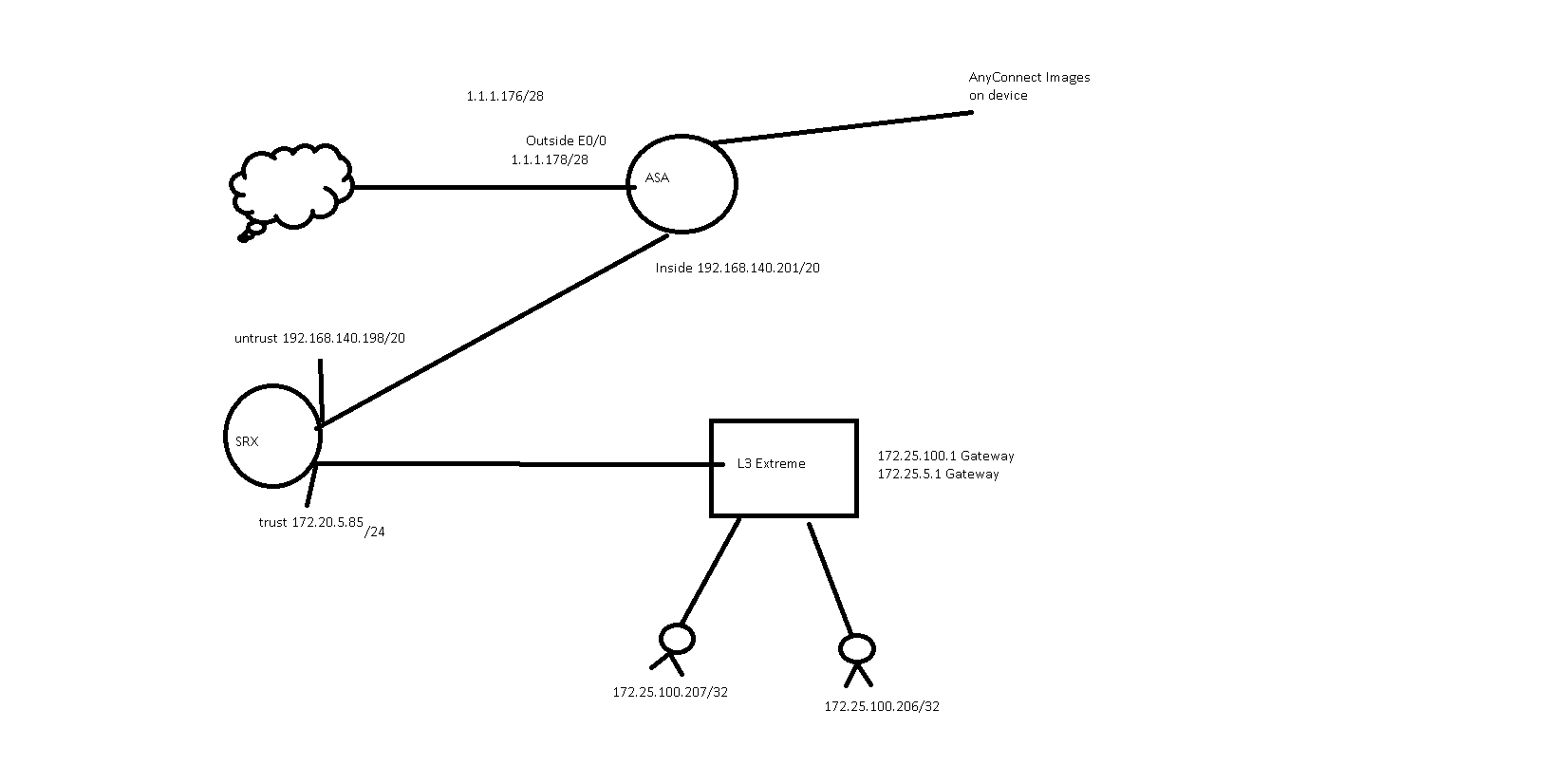
Solved! Go to Solution.
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 12:39 PM
As you show it, those values should be pushed to connected clients assuming they are connecting to a connection profile (aka tunnel-group) that's using that group policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 12:55 PM
What protocol do I allow for the devices in front of this? IPSEC? HTTPS?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 01:02 PM
If there is an upstream firewall you haven't shown, it would need to allow https to the ASA outside interface.
The basic AnyConnect-based remote access VPN is SSL. (You can setup IKEv2 IPsec but that's uncommon so far in most installations I've seen.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 02:15 PM
I allowed DNS (TCP/UDP) and RDP on the SRX in.
I can RDP in, but not by name only by host IP. What do I need to do?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 02:27 PM
I assume you gave the ASA an inside route for the target hosts.
It also needs a route for the VPN clients to get to the DNS servers if they are to resolve addresses.
If your internal networks are all from the 172.16.x.x/12 space, then I'd just add a route for that whole section of RFC 1918 space (vs. the earlier one for only the target /24 where the hosts are). i.e.:
route inside 172.16.0.0 255.240.0.0 192.168.140.198
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 03:20 PM
Okay that makes sense, I still have to type my domain name before I can rdp
Even with this
default-domain value cisco.local
What do I need to add?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 03:47 PM
Also is there a way to import the self signed cert that I created so anyconnect doesn't warn me? Or do I just have to buy one?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 07:33 PM
Regarding the certificate, you can browse to your ASA outside interface and, using your browser's certificate inspection ability, download the certificate to your local host. You can then import that certificate into the Trusted root certificate authority (CA) store (or equivalent on non-windows hosts) and it will be trusted for future connections. This may or may not be feasible per the technological savvy of the end users. For that reason and others, most enterprise deployments elect to use a certificate issues by an established CA.
For the domain issue, you need to add your local domain(s) if you want it/them to be prepended to the DNS suffix search list when a VPN connection is established.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2015 02:00 PM
The DNS is prepended, as far as I can see in ipconfig /all it has the correct domain, however when launching mstsc it is blank.
Thank you for your time Marvin! You have been a great help sir. Have a great week!
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

