- Cisco Community
- Technology and Support
- Security
- VPN
- Anyconnect Configuration Assistance with Juniper SRX
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2015 03:27 PM - edited 02-21-2020 08:22 PM
Hello and thank you for reading.
This is a new configuration and I need support. I do have TAC support but it has not proven successful.
Internet - > Cisco ASA -> Juniper SRX -> Extreme L3 SW -> PCA
What I have done so far is install the latest AnyConnect images - anyconnect-macosx-i386-3.1.09013-k9.pkg
and running asa916-6-k8.bin
Please help with the configuration, with the IP space shown, I have last octet available for public space .184, .185, I have drawn the network in question. See picture.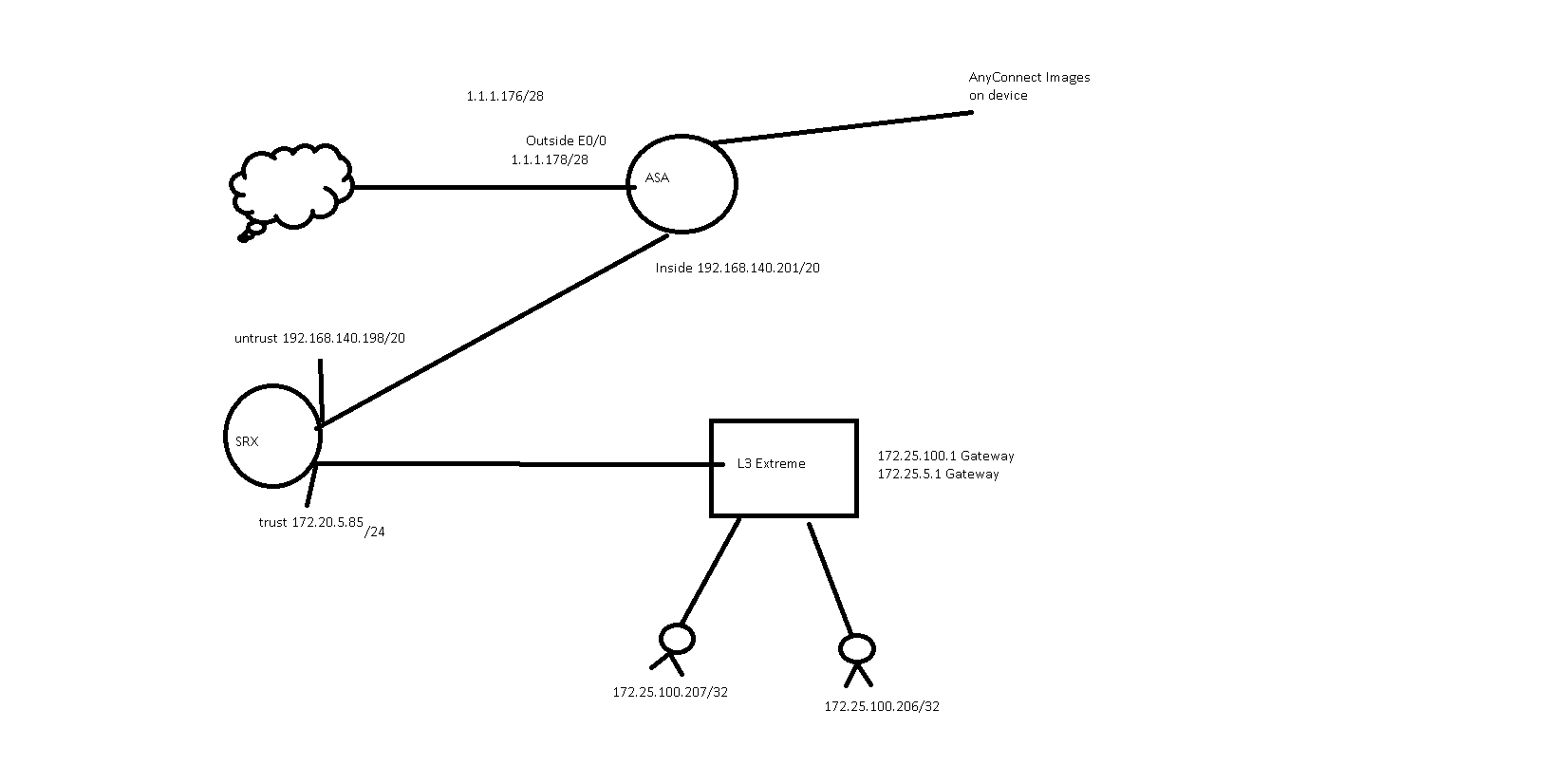
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 07:33 PM
Regarding the certificate, you can browse to your ASA outside interface and, using your browser's certificate inspection ability, download the certificate to your local host. You can then import that certificate into the Trusted root certificate authority (CA) store (or equivalent on non-windows hosts) and it will be trusted for future connections. This may or may not be feasible per the technological savvy of the end users. For that reason and others, most enterprise deployments elect to use a certificate issues by an established CA.
For the domain issue, you need to add your local domain(s) if you want it/them to be prepended to the DNS suffix search list when a VPN connection is established.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2015 04:24 PM
What is your goal?
Which clients do you want to be able to have remote access VPN capability? If it's the ones on your diagram, I can't quite figure out the logic behind that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2015 04:35 PM
The goal is to connect from the internet using anyconnect and traverse this network to the individual host IPs using RDP on the bottom of the diagram.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2015 04:46 PM
OK. breaking the problem down:
- can you establish a remote access VPN to the ASA from Internet-based clients?
- if you can, do they get the necessary route pushed down for the hosts in the 172.16.100.0/24 network?
- if they do, we need to look at the inside of the AS onwards through the SRX.
- can the ASA itself reach the target hosts?
- if it can, does the same rule on the SRX that allows that also allow the VPN address pool through from the Untrust to Trust zone?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2015 05:00 PM
- can you establish a remote access VPN to the ASA from Internet-based clients?
Yes, however I removed the config
- if you can, do they get the necessary route pushed down for the hosts in the 172.16.100.0/24 network?
Currently there is only an all zeros to the internet router (not listed) and of course it just has the connected route
- if they do, we need to look at the inside of the AS onwards through the SRX.
see above
- can the ASA itself reach the target hosts?
return traffic to the hosts, there is not route on the asa to the hosts itself
- if it can, does the same rule on the SRX that allows that also allow the VPN address pool through from the Untrust to Trust zone?
this is not configured
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2015 08:32 PM
You replied telling me about the ASA routes. I was talking about the routes that are pushed to the clients when connected via VPN. That will be represented on the ASA as the access-list name that is used under the " split-tunnel-network-list value <access-list name>" called out by "split-tunnel-policy tunnelspecified" in the group policy profile. The clients will see it on AnyConnect as connected routes.
You will need an ASA route to the 172.25.100.0/24 network as well. And likewise those clients need to know how to route out to the set of addresses assigned to the clients in your VPN pool. That will need to be in place (or included in the default route of their gateway).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 08:17 AM
What should the VPN Pool be? Also the configuration?
Here is where I started.
ip local pool VPN_POOL 192.168.50.1-192.168.50.254 mask 255.255.255.0
webvpn
enable outside
object network NETWORK_OBJ_192.168.50.0_24
subnet 192.168.50.0 255.255.255.0
webvpn
tunnel-group-list enable
anyconnect image disk0:/anyconnect-win-3.1.10010-k9.pkg 1
anyconnect image disk0:/anyconnect-macosx-i386-3.1.10010-k9.pkg 2
anyconnect enable
group-policy GroupPolicy_WebVPN internal
group-policy GroupPolicy_WebVPN attributes
vpn-tunnel-protocol ssl-client
dns-server value 172.27.20.4 172.25.104.16
wins-server none
default-domain value cbfsb.local
exit
tunnel-group WebVPN type remote-access
tunnel-group WebVPN general-attributes
default-group-policy GroupPolicy_WebVPN
address-pool VPN_POOL
tunnel-group WebVPN webvpn-attributes
group-alias WebVPN enable
nat (inside,outside) 13 source static any any destination static NETWORK_OBJ_192.168.50.0_24 NETWORK_OBJ_192.168.50.0_24 no-proxy-arp route-lookup
-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 10:23 AM
OK, so your remote clients will get an address from the address pool 192.168.50.0/24. That subnet is exempted from NAT. So that's all good.
Does the ASA know how to reach the 172.25.100.0/24 network where the internal hosts are located?
Do those hosts or their gateway have a route (default or otherwise) to the 192.168.50.0 pool addresses (i.e. to the ASA)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 10:28 AM
Should I make a pool that is from the ASA insides interface? Due to the fact that it is a /20 or what do you recommend?
Not right now.
They would if it is an address range of the inside interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 10:34 AM
I tend to define the pool as its own discrete subnet. It can be (even more) confusing when it's carved out of an existing network. Either way will work though as long as they are unique addresses and the places they need to reach know how to route back to them.
Having the routing in place is key to making it work. When the ASA is the default gateway for all outbound traffic (i.e. to anywhere on the Internet or otherwise unknown) it's not an issue as the default will take care of it. If that's not the case then we need to account for it in our routing scheme.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 10:45 AM
Okay so now that you know my scenario. What does the ASA config look like?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 10:51 AM
It depends on how you have configured routing on your ASA. If it's all static routes, then you would need something like:
route inside 172.25.100.0 255.255.255.0 192.168.140.198
That tells the ASA how to get to the internal hosts.
The L3 Extreme switch and SRX would similarly need routes directing them to the next hop for the VPN pool. The SRX would also need the access policy as I mentioned earlier.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 11:12 AM
What about the split tunnel?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 11:46 AM
Your configuration didn't have any split-tunnel-policy so the default is no split tunnel. With that in place, all traffic from the clients flows over the VPN when it is active.
If you need it then you would add the following in the group policy:
split-tunnel-policy tunnelspecified split-tunnel-network-list value vpn_acl access-list vpn_acl extended permit ip 172.25.100.0 255.255.255.0 192.168.50.0 255.255.255.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2015 12:34 PM
Okay thank you. What about the domain name and dns server? I had it listed like this, however when connected the laptop does not get these settings.
group-policy GroupPolicy_AnyConnect_VPN attributes
vpn-tunnel-protocol ssl-client
dns-server value 172.27.105.4 172.25.65.16
wins-server none
default-domain value cisco.local
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

