- Cisco Community
- Technology and Support
- Security
- VPN
- Re: AnyConnect Management Tunnel - Disconnected (connect failed)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AnyConnect Management Tunnel - Disconnected (connect failed)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2022 07:46 AM
Hi,
I am troubleshooting an issue with our management tunnel for AnyConnect.
AnyConnect - 4.10.06079
FMC/FTD - 7.0.4
Followed this below guide
I already have an existing AnyConnect profile and associated the new management.xml file within my group policy setting.
Test clients can connect when they click "Connect"
Manually disconnected and monitored "Management Connection State" and this errors with Disconnected (connect failed).
Triple checked everything and looks ok to me.
Any ideas with this?
- Labels:
-
AnyConnect
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2022 11:14 AM
Hi @vineshchauhan,
This could be to numerous reasons. You'll need to check client side logs, to try to understand why is it failing (e.g. unable to read machine certificate, error in XML profile, etc.). To begin with, try with Windows Event Viewer logs.
You could upload DART file to take a look at, but that will probably contain too much information inside to disclose publicly.
Kind regards,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2022 08:51 AM
Hi,
Thank you for the additional checks, I completely forgot about Windows Event logs. I will start reviewing these events.
Machine Cert is good and auths ok when I use AnyConnect app.
Agree DART will have too much sensitive data.
I will keep the forum updated with any updates
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2022 06:51 AM - edited 11-28-2022 06:55 AM
Hi, Further troubleshooting with Management Tunnel. DART file showing the machine is trying to access User Store instead of Machine Cert Store.
Profile is setup to use machine only and override option enabled
Date : 11/24/2022
Time : 15:58:57
Type : Error
Source : acvpnmgmttun
Description : Function: ConnectMgr::certAuthHasFailed
File: c:\temp\build\thehoff\phoenix_mr60.978227566292\phoenix_mr6\vpn\api\connectmgr.cpp
Line: 16807
Certificate authentication requested from gateway, no valid certs found in users cert store.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2022 11:36 AM
You are on the right path to figure out what is going on. Now you need to figure out why is your machine cert not eing selected - e.g. maybe it doesn't have proper EKU, or your cert matching condition is not right. You'll need to figure out what went wrong with machine cert.
Kind regards,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2022 06:39 AM
Hi,
Update on this issue.
With help and guidance from Cisco TAC, I have managed to get the Management Tunnel working.
I had to create a 2nd Connection Profile for Management Only and Custom URL for Management listed.
Profile also has Tunnel Include configuration & SSL authentication.
User Connection Profile. This has all the ACL/Dynamic Split config and XML for User and Management. I've added the Management XML in this profile so that its deployed when the user tunnel is activated. If not, I would need to deploy via SCCM.
Now when the machine is powered on and waiting for a logon, management tunnel is activated.
Once a user logs on, User tunnel takes over.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2023 06:59 AM
Now when the machine is powered on and waiting for a logon, management tunnel is activated.// How did you valiadate this ? While looking at anyconnect session from Firewall ? or you are still logging in as user but not connecting the VPN ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2023 07:07 AM
Hi,
When the machine is on logon screen, I validated the connection via a SSL Certificate (Stored in Machine Store).
I've got 2 profiles for Remote access and XML files deployed to end users:
User profile - Used when the user has logged on
Machine profile - Used when waiting on logon screen. This also has an ACL to tunnel all traffic to inside
Both profiles use same subnet for dhcp.
I hope this helps.
thanks
Vinny
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2023 08:20 AM
I validated the connection via a SSL Certificate (Stored in Machine Store).// I already see Cert at Machine Store. But VPN do not connect.
2 Profile you are referring the xml files in program data > Cisco >Cisco .... > Profile Folder ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2023 09:11 AM
Hi
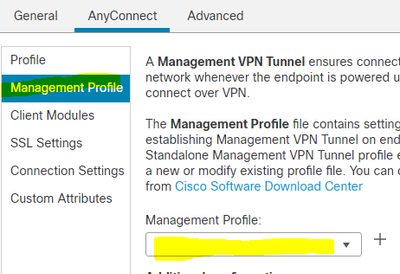
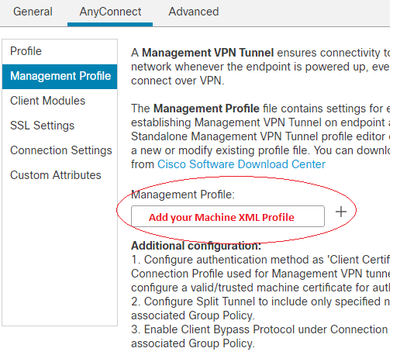
The management xml file will be in its own folder called mgttun
To deploy my management xml file, I used my user group policy to deploy management xml. There is a section to use management under one of the sub section.
I can send a screenshot tomorrow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2023 12:47 AM
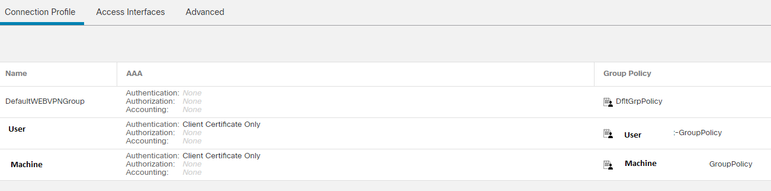
I've got 2 profiles setup.
Machine Group Policy
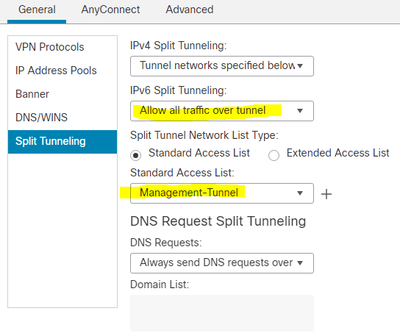
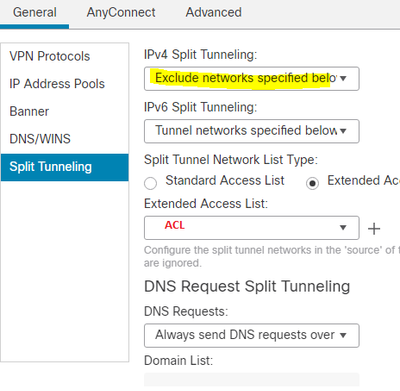
ACL to tunnel Internal subnets
Management Tunnel has a requirement to tunnel all internal traffic. Without this option set, my Mgt failed to activate.
I’ve left this blank under Machine Group Policy. Set under User Group Policy
User Group Policy
After logon and user connects, Management XML profile is download and installed here:
C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\Profile\MgmtTun
We use split tunnel for MS based traffic. This was added here:
I hope this helps.
Thanks
Vinny
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide