- Cisco Community
- Technology and Support
- Security
- VPN
- Re: AnyConnect not detecting Machine Store Cert for Auth
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2020 04:53 PM
My Window clients have been enrolled with Machine certs and placed them in the Machine Store. This will be used for AC authentication. When I select the Cert Connection Profile, AnyConnect cannot find the certificate and I get "Certificate Validation Failure". Funny thing is, I had it working before. I removed the cert, auto-enrolled for machine cert again, and now I can't connect.
How do I make sure AnyConnect is searching and selecting the correct Certificate for authentication on my machines?
Is there any way I can see this info with a command?
Firepower 2110 btw
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2020 03:22 PM
SOLVED!
So it seemed that I needed to run the AnyConnect in Admin privileges in order to get it working. Since I don't want it to work that way, I also found out that I needed to remove SSL from the following areas:
1. Group Policy in FMC - In the General/VPN Protocols menu, only have "IPsec-IKEv2" enabled.
2. VPN Prolfile Editor - make sure the .XML you're using has:
- FMC VPN Connection Profile name as the User Group, not the Group Policy. (IPsec specific, SSL used Group Policy here)
- Under Connection Information, "IPsec" is selected, ASA gatewas is deselected.
Once SSL was removed, I was able to establish Machine Certificate Authentication without Admin privileges.
All in all, allowing VPN to connect AC via SSL, you need admin privileges to read Machine Store. If you remove the SSL as an option to connect on the FP, then you force it to use IKEv2 IPSec, in return, AC doesn't need admin privileges to read Machine Store
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2020 05:17 PM
Also, The certificate on my firepower is issued by the same root CA server, so the cert path is good on both. Anything else I can look at on the certs from machine and Firepower?
Another thing, my Management Tunnel VPN, which is Machine Cert authenticate, still works. Kinda wierd. Both should be using the same cert but Connection Profile fails.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2020 06:53 PM
What is the key usage for your certificate, it should include client
authentication and server authentication. Otherwise it won't work and you
will get certificate not found.
**** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2020 08:03 PM - edited 10-13-2020 08:09 PM
Well I got it working again BECAUSE I used the same certificate issued to the Firewall by our Root CA. Even though it works, I need to get AnyConnect to recognize the actual Machine certificate that we have on the machine..
Key usage, is to authenticate with Machine Certificate only. I only want to allow machines VPN access that have a certificate issued by our CA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2020 09:10 PM
So in FMC, I know I need to have the Root CA certificate uploaded as a "Trusted CAs" object. Now, since I need to authenticate users certs, do I have to install the Root CA on the "Interface Trustpoint" for my Outside interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2020 02:30 AM
With AnyConnect the trust point that will be used for VPN authentication should be applied to the FTD outside interface. The FTD would need an identity certificate which will be presented to the AnyConnect clients when they try to initiate the VPN connection.
This behaviour is different with the site-to-site VPN certificate authentication where you can have the authentication trust point configured and used for authentication without having to apply it to the outside interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2020 04:24 PM
So I have the PFX file that was issued by our internal CA Server, which includes (the identity cert, its private key, and the Root CA cert). It's name is AnyConnect5.pfx and I installed that on the Outside Trustpoint on my firewall.
For **bleep**-n-gigs, I installed that exact same PFX file, AnyConnect5.pfx, on my computer, THEN everything works, Cert Authentication and MGMT Tunnel. When I remove the certificates it installed, AnyConnect doesn't want to read the ACTUAL machine cert on my computer and says "No Vailed Cert . . " then "Certificate Validation Failure"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2020 09:27 PM
Hello Gilbert,
The AnyConnect must have permission to be able to look for certificates on the machine store.
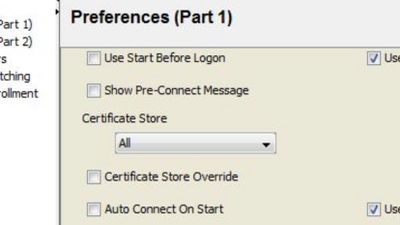
Those permissions are granted via an xml profile with the certificate store “all” or “machine”, and “certificate store override” checked.
Rate if it helps.
Regards,
Josue Brenes
TAC - VPN Engineer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2020 02:05 PM
So I removed the Firepowers certificate and after about a half day, the Mgmt tunnel was able to authentice with the machine cert of my laptop. Not sure why it took that long but it works now. I was able to verify by having my coworker remove the FP cert and about a half day later, his Mgmt tunnel was working with his machine cert.
I still can't get the regular User (non-Mgmt) VPN Connection Profile to work with machine cert, and I had Certificate Store Override turned. I turned it on and lets see if it works after a half day maybe.
I'll report back with anything else I find.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2020 02:16 PM
Yeah, you need to enable Certificate Store Override, that should allow AnyConnect from a limited user session to interact with the machine certs store. The machine needs to have an identity cert issued by the same CA as the one that issued the cert for the FP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2020 10:19 AM
With CSO enabled, it's still not working. Going to see what TAC says about this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2020 12:06 PM - edited 10-16-2020 12:06 PM
So after looking through the DART logs, I see that AC is looking in the User Store, rather than Machine Store. The Profile is set to Machine, not All. Kinda odd.
Date : 10/16/2020
Time : 09:58:41
Type : Error
Source : acvpnui
Description : Function: ConnectMgr::certAuthHasFailed
File: c:\temp\build\thehoff\orion_mr10.989354729559\orion_mr1\vpn\api\connectmgr.cpp
Line: 16883
Certificate authentication requested from gateway, no valid certs found in users cert store.
******************************************
Date : 10/16/2020
Time : 09:58:41
Type : Information
Source : acvpnui
Description : Message type warning sent to the user:
No valid certificates available for authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2020 03:22 PM
SOLVED!
So it seemed that I needed to run the AnyConnect in Admin privileges in order to get it working. Since I don't want it to work that way, I also found out that I needed to remove SSL from the following areas:
1. Group Policy in FMC - In the General/VPN Protocols menu, only have "IPsec-IKEv2" enabled.
2. VPN Prolfile Editor - make sure the .XML you're using has:
- FMC VPN Connection Profile name as the User Group, not the Group Policy. (IPsec specific, SSL used Group Policy here)
- Under Connection Information, "IPsec" is selected, ASA gatewas is deselected.
Once SSL was removed, I was able to establish Machine Certificate Authentication without Admin privileges.
All in all, allowing VPN to connect AC via SSL, you need admin privileges to read Machine Store. If you remove the SSL as an option to connect on the FP, then you force it to use IKEv2 IPSec, in return, AC doesn't need admin privileges to read Machine Store
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide