- Cisco Community
- Technology and Support
- Security
- VPN
- Hi Heiko,
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AnyConnect not working after ASA firmware update
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2016 07:01 AM - edited 02-21-2020 08:42 PM
Hi all,
we have updated our ASA 5515 to version 9.5(2)2 and now anyconnect from our devices no longer works.
If I try to connect from my Samsung Smartphone I get the following message "connection attempt failed".
Is there any known issue that can cause this problem?
If it is useful I can send the debug log of my smartphone.
Thank you.
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2016 07:33 AM
Hi,
Please check the
Does the request even reach the
Could you share the config of the device as well ?
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2016 02:48 AM
Hi all,
thank you for the quick answers. First I will share the ASA config and the AnyConnect Client debug.
Both file are edited, I have removed the IP addresses and other private data.
ASA config:
: Saved
:
: Serial Number: FCH...JJSU
: Hardware: ASA5515, 8192 MB RAM, CPU Clarkdale 3058 MHz, 1 CPU (4 cores)
:
ASA Version 9.5(2)2
!
hostname 123456789
domain-name 123456789
enable password 123456789 encrypted
names
...
...
...
!
interface GigabitEthernet0/0
description ...
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/0.2
description ...
vlan 2
nameif ...
security-level 50
ip address ...
!
interface GigabitEthernet0/0.17
description ...
vlan 17
nameif inside
security-level 100
ip address ...
!
interface GigabitEthernet0/0.20
description ...
vlan 20
nameif ...
security-level 100
ip address ...
!
interface GigabitEthernet0/0.360
description ...
vlan 360
nameif ...
security-level 100
ip address ...
!
interface GigabitEthernet0/0.610
description ...
vlan 610
nameif ...
security-level 100
ip address ...
!
interface GigabitEthernet0/0.810
description ...
vlan 810
nameif ...
security-level 100
ip address ...
!
interface GigabitEthernet0/0.1110
description ...
vlan 1110
nameif ...
security-level 100
ip address ...
!
interface GigabitEthernet0/0.1310
description ...
vlan 1310
nameif ...
security-level 100
ip address ...
!
interface GigabitEthernet0/0.1510
description ...
vlan 1510
nameif ...
security-level 100
ip address ...
!
interface GigabitEthernet0/0.2010
description ...
vlan 2010
nameif ...
security-level 40
ip address ...
!
interface GigabitEthernet0/1
description ...
nameif ...
security-level 10
ip address ...
!
interface GigabitEthernet0/2
description ...
nameif ...
security-level 100
ip address ...
!
interface GigabitEthernet0/3
description ...
nameif ...
security-level 0
ip address ...
!
interface GigabitEthernet0/4
description ...
!
interface GigabitEthernet0/5
description ...
!
interface Management0/0
description Management
management-only
shutdown
nameif Management
security-level 10
no ip address
!
boot system disk0:/asa952-2-smp-k8.bin
boot system disk0:/asa952-smp-k8.bin
ftp mode passive
clock timezone CEST 1
clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00
dns server-group DefaultDNS
domain-name ...
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network DMZ-NAT-01
subnet ...
object network ...
subnet ...
object network ...
subnet ...
object network ...
subnet ...
object network ...
subnet ...
object network ...
subnet ...
object network ...
subnet ...
object network ...
subnet ...
object network ...
subnet ...
object network ...
subnet ...
object network ...
host ...
object network ...
host ...
object network ...
host ...
object network ...
host ...
object network ...
host ...
object network ...
host ...
object network ...
host ...
object network ...
host ...
object network ...
host ...
object network ...
subnet ...
object-group network ...
network-object ...
object-group network ...
network-object ...
object-group network ...
network-object host ...
object-group network ...
network-object ...
network-object ...
object-group service WEB-Browsing tcp
port-object eq www
port-object eq https
object-group service smtp_smtps tcp
port-object eq smtp
port-object eq 587
port-object eq 465
object-group network Syslog-Server
network-object host Syslog-Server
object-group network ...
network-object host ...
network-object host ...
network-object ...
object-group network ...
network-object ...
network-object ...
network-object ...
object-group network ...
network-object ...
object-group network ...
network-object ...
network-object ...
network-object ...
network-object ...
network-object ...
network-object ...
network-object ...
network-object ...
network-object ...
object-group network ...
network-object ...
network-object ...
network-object ...
network-object ...
network-object ...
object-group network ...
network-object ...
network-object ...
object-group network ...
description ...
network-object ...
object-group network ...
description ...
network-object ...
object-group network ...
description ...
network-object ...
object-group ...
description ...
network-object ...
...
...
...
access-list
...
...
...
no pager
logging enable
logging timestamp
logging buffer-size 262144
logging asdm-buffer-size 512
logging monitor debugging
logging buffered debugging
logging trap notifications
logging asdm debugging
logging from-address ...
logging recipient-address ... level alerts
logging recipient-address ... level critical
logging facility 16
logging device-id hostname
logging host ... Syslog-Server format emblem
...
...
...
...
...
...
asdm image disk0:/asdm-752.bin
asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat
...
...
...
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication enable console LOCAL
aaa authentication http console LOCAL
aaa authorization command LOCAL
http server enable 4443
http server idle-timeout 60
http x.x.x.x y.y.y.y inside
http x.x.x.x y.y.y.y DMZ
http x.x.x.x y.y.y.y outside
http x.x.x.x y.y.y.y ...
http x.x.x.x y.y.y.y ...
http x.x.x.x y.y.y.y ...
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set TS-AES esp-aes-256 esp-sha-hmac
crypto ipsec ikev2 ipsec-proposal IKEv2-AES2G-SHA5
protocol esp encryption aes-gcm-256
protocol esp integrity sha-512
crypto ipsec ikev2 ipsec-proposal IKEv2-AES2-SHA
protocol esp encryption aes-256
protocol esp integrity sha-1
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map outside_dyn_map 10 set pfs
crypto dynamic-map outside_dyn_map 10 set ikev1 transform-set TS-AES
crypto dynamic-map DynMap 1000 set pfs group5
crypto dynamic-map DynMap 1000 set ikev1 transform-set TS-AES
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 135 match address ...
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 135 set ikev1 transform-set TS-AES
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 135 set security-association lifetime seconds 28800
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 135 set security-association lifetime kilobytes 4608000
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 999 set ikev1 transform-set TS-AES
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 999 set security-association lifetime seconds 28800
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 999 set security-association lifetime kilobytes 4608000
crypto map outside_map 10 match address Mobile1_Tunnel
crypto map outside_map 10 set peer x.x.x.x
crypto map outside_map 10 set ikev1 transform-set TS-AES
crypto map outside_map 20 match address Mobile2_Tunnel
crypto map outside_map 20 set peer x.x.x.x
crypto map outside_map 20 set ikev1 transform-set TS-AES
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
subject-name CN=x.x.x.x,CN=swis
crl configure
crypto ca trustpoint ASDM_TrustPoint0
enrollment self
subject-name CN=x.x.x.x
crl configure
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_1
enrollment self
subject-name CN=x.x.x.x,CN=swis
crl configure
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_2
enrollment self
subject-name CN=x.x.x.x,CN=swis
crl configure
crypto ca trustpoint AC-SSL
enrollment self
serial-number
ip-address x.x.x.x
keypair anyconnect
crl configure
crypto ca trustpool policy
crypto ca certificate chain AC-SSL
certificate 55b0d055
0d010902 161e464d 2d415341 312e6c73 62622e73 61636873 656e2d61 6e68616c
742e6465 30820222 300d0609 2a864886 f70d0101 01050003 82020f00 3082020a
02820201 00b8592f be748403 d090971d 6299bdaf 36e52911 89abd536 52510309
8c6e8574 b5efb5d0 6c16d429 aea6b8ac ced21c9a a1851d80 ff15b310 73cd38d8
bd819389 35af00d7 a7742e95 7df57d1e bd4179d7 391484d6 7e38bbb6 30c29fb4
00de21b2 7803300b 39fa22c3 588bce1b f2c99285 21e6dc46 1ceb8b32 7c20e510
5cecbe88 26002b33 a040ab66 f18d3371 846a5307 09c6218c 1d6b4f99 684a804e
111210b0 7b0328cd 26efaebb 474a50c5 e99e635e cebc1b91 15319171 5c8c5562
69262cb3 1a8ef101 96748b16 c8829225 2c59136b a48a6e89 f1978a8a 76cbce68
3082053a 30820322 a0030201 02020455 b0d05530 0d06092a 864886f7 0d010105
0500305f 315d3012 06035504 05130b46 43483138 33334a4a 5355301a 06092a86
4886f70d 01090813 0d313935 2e313435 2e313235 2e32302b 06092a86 4886f70d
01090216 1e464d2d 41534131 2e6c7362 622e7361 63687365 6e2d616e 68616c74
2e646530 1e170d31 35303831 38313133 3130365a 170d3235 30383135 31313331
30365a30 5f315d30 12060355 0405130b 46434831 3833334a 4a535530 1a06092a
864886f7 0d010908 130d3139 352e3134 352e3132 352e3230 2b06092a 864886f7
.....
.....
.....
3082053a 30820322 a0030201 02020455 b0d05530 0d06092a 864886f7 0d010105
0500305f 315d3012 06035504 05130b46 43483138 33334a4a 5355301a 06092a86
4886f70d 01090813 0d313935 2e313435 2e313235 2e32302b 06092a86 4886f70d
01090216 1e464d2d 41534131 2e6c7362 622e7361 63687365 6e2d616e 68616c74
2e646530 1e170d31 35303831 38313133 3130365a 170d3235 30383135 31313331
30365a30 5f315d30 12060355 0405130b 46434831 3833334a 4a535530 1a06092a
864886f7 0d010908 130d3139 352e3134 352e3132 352e3230 2b06092a 864886f7
d8098a26 359da33a 4e17805f 84e179d3 105c5b64 640089e4 ef8b7bab eb477aca
3c6672e1 d403b4a2 fcb04ff1 5163378d 60524cef e8f9198d ac959e72 da057141
7e797160 66cde516 e229babf 31146cd6 84851f19 191f4b49 7a5b2454 c4773428
b410d02a d6abc51a c2418ed8 a3d80da9 f9f298c1 6518ee0a ff9705ef 89e9caf1
3082053a 30820322 a0030201 02020455 b0d05530 0d06092a 864886f7 0d010105
0500305f 315d3012 06035504 05130b46 43483138 33334a4a 5355301a 06092a86
4886f70d 01090813 0d313935 2e313435 2e313235 2e32302b 06092a86 4886f70d
01090216 1e464d2d 41534131 2e6c7362 622e7361 63687365 6e2d616e 68616c74
2e646530 1e170d31 35303831 38313133 3130365a 170d3235 30383135 31313331
30365a30 5f315d30 12060355 0405130b 46434831 3833334a 4a535530 1a06092a
864886f7 0d010908 130d3139 352e3134 352e3132 352e3230 2b06092a 864886f7
b6f7423c 2df5b7f8 2de529fa 317fd5f8 e38b4f98 496f1d4d b5898306 289faded
d9c118fc 94553bec dca7533c 2f590909 23e858bd a0150a01 7aed1bae 45bd54ca
9527ad13 a832a8cb eb8a9b9a 969ec982 70243187 200f5716 82f43639 32b178ef
aebc2341 e104a63d 2eeaea1c e94ed2be 2b525cce 3cb9310a fbfbb60d 376d333e
814cf477 da790821 08289eca 490f552f bc3df215 80e214df 8c90521c 83dd22d6
41763d5c 3f451c53 4a03c026 8f3afefd e63d1b89 8d0d4c51 b9332019 ae6b9c4a
d0d63f34 66126a56 b02ad177 e098153b 0f4351ba 062189b3 acc58f7e c15e
quit
crypto isakmp nat-traversal 60
crypto isakmp disconnect-notify
crypto ikev2 policy 20
encryption aes-256
integrity sha512
group 21 24
prf sha512
lifetime seconds 86400
crypto ikev2 enable outside client-services port 60443
crypto ikev2 cookie-challenge always
crypto ikev2 limit max-in-negotiation-sa 10
crypto ikev2 limit max-sa 64
crypto ikev2 remote-access trustpoint AC-SSL
crypto ikev1 enable outside
crypto ikev1 policy 20
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
crypto ikev1 policy 40
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh scopy enable
ssh stricthostkeycheck
ssh x.x.x.x y.y.y.y
...
...
...
ssh timeout 60
ssh version 2
ssh key-exchange group dh-group14-sha1
console timeout 30
management-access NMS-LAN
!
threat-detection rate scanning-threat rate-interval 600 average-rate 20 burst-rate 40
threat-detection rate scanning-threat rate-interval 3600 average-rate 16 burst-rate 32
threat-detection basic-threat
threat-detection statistics host
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server Syslog-Server prefer
ssl dh-group group24
ssl ecdh-group group21
ssl trust-point AC-SSL outside
ssl trust-point ASDM_Launcher_Access_TrustPoint_2 Management
ssl trust-point ASDM_Launcher_Access_TrustPoint_2 Management vpnlb-ip
webvpn
port 60443
enable outside
dtls port 60443
anyconnect-essentials
anyconnect image disk0:/anyconnect-win-3.1.10010-k9.pkg 1
anyconnect profiles 12345 disk0:/testsbsk.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy SBSK-Policy2 internal
group-policy SBSK-Policy2 attributes
vpn-simultaneous-logins 2
vpn-idle-timeout none
vpn-tunnel-protocol ikev1
password-storage disable
pfs enable
ipsec-udp enable
split-tunnel-policy tunnelspecified
split-tunnel-network-list value 12345
group-policy xyz internal
group-policy xyz-Policy attributes
dns-server value 10.3.255.31
vpn-simultaneous-logins 2
vpn-idle-timeout none
vpn-tunnel-protocol ikev1
password-storage disable
pfs enable
ipsec-udp enable
default-domain value xyz
group-policy Mobile1_GroupPolicy internal
group-policy Mobile1_GroupPolicy attributes
vpn-filter value Mobile1_Filter
vpn-tunnel-protocol ikev1
group-policy Mobile2_GroupPolicy internal
group-policy Mobile2_GroupPolicy attributes
vpn-filter value Mobile2_Filter
vpn-tunnel-protocol ikev1
group-policy xyz internal
group-policy xyz attributes
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelspecified
split-tunnel-network-list value xyz
group-policy xyz internal
group-policy xyz attributes
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelspecified
split-tunnel-network-list value xyz
group-policy xyz internal
group-policy xyz attributes
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelspecified
split-tunnel-network-list value xyz
group-policy xyz-Policy internal
group-policy xyz-Policy attributes
vpn-tunnel-protocol ikev1
group-policy xyz internal
group-policy xyz attributes
vpn-simultaneous-logins 2
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelspecified
split-tunnel-network-list value xyz
group-policy xyz-Policy internal
group-policy xyz-Policy attributes
vpn-tunnel-protocol ikev1
group-policy xyz internal
group-policy xyz attributes
vpn-simultaneous-logins 6
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelspecified
split-tunnel-network-list value xyz
group-policy xyz internal
group-policy xyz attributes
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelspecified
split-tunnel-network-list value xyz
group-policy xyz internal
group-policy xyz attributes
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelspecified
split-tunnel-network-list value xyz
group-policy LAN2LAN internal
group-policy LAN2LAN attributes
vpn-tunnel-protocol ikev1
group-policy AnyConnect-Policy internal
group-policy AnyConnect-Policy attributes
vpn-simultaneous-logins 1
vpn-tunnel-protocol ikev2 ssl-client
default-domain value xyz
webvpn
anyconnect profiles value anyconnect type user
always-on-vpn profile-setting
dynamic-access-policy-record DfltAccessPolicy
webvpn
svc ask none default svc
username xyz password R05WbkvmQIuSeFVE encrypted privilege 15
username xyz attributes
vpn-group-policy AnyConnect-Policy
vpn-simultaneous-logins 2
vpn-idle-timeout 60
vpn-tunnel-protocol ikev2 ssl-client
service-type admin
...
...
...
tunnel-group
...
...
...
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 8192
message-length maximum server auto
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
inspect icmp error
!
service-policy global_policy global
smtp-server x.x.x.x
privilege cmd level 3 mode exec command perfmon
privilege cmd level 3 mode exec command ping
privilege cmd level 3 mode exec command who
privilege cmd level 3 mode exec command logging
privilege cmd level 3 mode exec command failover
privilege cmd level 3 mode exec command packet-tracer
privilege show level 5 mode exec command import
privilege show level 5 mode exec command running-config
privilege show level 3 mode exec command reload
privilege show level 3 mode exec command mode
privilege show level 3 mode exec command firewall
privilege show level 3 mode exec command asp
privilege show level 3 mode exec command cpu
privilege show level 3 mode exec command interface
privilege show level 3 mode exec command clock
privilege show level 3 mode exec command dns-hosts
privilege show level 3 mode exec command access-list
privilege show level 3 mode exec command logging
privilege show level 3 mode exec command vlan
privilege show level 3 mode exec command ip
privilege show level 3 mode exec command failover
privilege show level 3 mode exec command asdm
privilege show level 3 mode exec command arp
privilege show level 3 mode exec command ipv6
privilege show level 3 mode exec command route
privilege show level 3 mode exec command aaa-server
privilege show level 3 mode exec command aaa
privilege show level 3 mode exec command crypto
privilege show level 3 mode exec command ssh
privilege show level 3 mode exec command vpn-sessiondb
privilege show level 3 mode exec command vpn
privilege show level 3 mode exec command dhcpd
privilege show level 3 mode exec command blocks
privilege show level 3 mode exec command wccp
privilege show level 3 mode exec command dynamic-filter
privilege show level 3 mode exec command webvpn
privilege show level 3 mode exec command module
privilege show level 3 mode exec command uauth
privilege show level 3 mode exec command compression
privilege show level 3 mode exec command ospf
privilege show level 3 mode exec command eigrp
privilege show level 3 mode configure command interface
privilege show level 3 mode configure command clock
privilege show level 3 mode configure command access-list
privilege show level 3 mode configure command logging
privilege show level 3 mode configure command ip
privilege show level 3 mode configure command failover
privilege show level 5 mode configure command asdm
privilege show level 3 mode configure command arp
privilege show level 3 mode configure command route
privilege show level 3 mode configure command aaa-server
privilege show level 3 mode configure command aaa
privilege show level 3 mode configure command crypto
privilege show level 3 mode configure command ssh
privilege show level 3 mode configure command dhcpd
privilege show level 5 mode configure command privilege
privilege clear level 3 mode exec command crypto
privilege clear level 3 mode exec command dns-hosts
privilege clear level 3 mode exec command logging
privilege clear level 3 mode exec command arp
privilege clear level 3 mode exec command aaa-server
privilege clear level 3 mode exec command dynamic-filter
privilege cmd level 3 mode configure command failover
privilege clear level 3 mode configure command logging
privilege clear level 3 mode configure command crypto
privilege clear level 3 mode configure command arp
privilege clear level 3 mode configure command aaa-server
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:00378dbdafb8aa4c839e188cf154effe
: end
Client debug:
--------- beginning of /dev/log/main
03-02 15:45:54.962 I/AnyConnect(14173): ProcessOutputParser: Stopping process reading for command: logcat -c
03-02 15:45:54.962 I/AnyConnect(14173): ProcessOutputParser: Stopping process reading for command: logcat -v time AnyConnect:V vpnagent:V acvpnagent:V vpnapi:V vpndownloader:V vpnsnak:V VpnJni:V ConnectivityService:V WifiStateTracker:V WifiMonitor:V AndroidRuntime:V KnoxVpnEngine:V KnoxVpnFirewallHelper:V KnoxVpnEngineService:V GenericVpnPolicy:V *:S
03-02 15:45:55.012 I/AnyConnect(14173): ProcessOutputParser: Starting to read from Process: logcat -v time AnyConnect:V vpnagent:V acvpnagent:V vpnapi:V vpndownloader:V vpnsnak:V VpnJni:V ConnectivityService:V WifiStateTracker:V WifiMonitor:V AndroidRuntime:V KnoxVpnEngine:V KnoxVpnFirewallHelper:V KnoxVpnEngineService:V GenericVpnPolicy:V *:S
03-02 15:45:57.145 I/AnyConnect(14173): ProcessOutputParser: Stopping process reading for command: logcat -v time AnyConnect:V vpnagent:V acvpnagent:V vpnapi:V vpndownloader:V vpnsnak:V VpnJni:V ConnectivityService:V WifiStateTracker:V WifiMonitor:V AndroidRuntime:V KnoxVpnEngine:V KnoxVpnFirewallHelper:V KnoxVpnEngineService:V GenericVpnPolicy:V *:S
03-02 15:45:57.285 E/SpannableStringBuilder(14173): SPAN_EXCLUSIVE_EXCLUSIVE spans cannot have a zero length
03-02 15:45:57.285 E/SpannableStringBuilder(14173): SPAN_EXCLUSIVE_EXCLUSIVE spans cannot have a zero length
03-02 15:45:57.955 E/SpannableStringBuilder(14173): SPAN_EXCLUSIVE_EXCLUSIVE spans cannot have a zero length
03-02 15:45:57.955 E/SpannableStringBuilder(14173): SPAN_EXCLUSIVE_EXCLUSIVE spans cannot have a zero length
03-02 15:45:58.576 D/ProgressBar(14173): setProgress = 0
03-02 15:45:58.576 D/ProgressBar(14173): setProgress = 0, fromUser = false
03-02 15:45:58.576 D/ProgressBar(14173): mProgress = 0mIndeterminate = false, mMin = 0, mMax = 10000
03-02 15:45:58.586 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:45:58.606 I/vpnapi (14173): An SSL VPN connection to x.x.x.x has been requested by the user.
03-02 15:45:58.606 W/vpnapi (14173): Function: getProfileNameFromHost File: ProfileMgr.cpp Line: 1169 No profile available for host x.x.x.x.
03-02 15:45:58.606 I/vpnapi (14173): Function: getHostInitSettings File: ProfileMgr.cpp Line: 1253 Profile () not found. Using default settings.
03-02 15:45:58.606 I/AnyConnect(14241): NetworkComponentHostService: Posting message to run updateComponentState()
03-02 15:45:58.616 I/vpnapi (14173): Function: loadProfiles File: ProfileMgr.cpp Line: 186 No profile is available.
03-02 15:45:58.616 W/vpnapi (14173): Function: getProfileNameFromHost File: ProfileMgr.cpp Line: 1169 No profile available for host x.x.x.x.
03-02 15:45:58.616 I/vpnapi (14173): Using default preferences. Some settings (e.g. certificate matching) may not function as expected if a local profile is expected to be used. Verify that the selected host is in the server list section of the profile and that the profile is configured on the secure gateway.
03-02 15:45:58.616 W/vpnapi (14173): Function: getProfileNameFromHost File: ProfileMgr.cpp Line: 1169 No profile available for host x.x.x.x.
03-02 15:45:58.616 I/vpnapi (14173): Function: getHostInitSettings File: ProfileMgr.cpp Line: 1253 Profile () not found. Using default settings.
03-02 15:45:58.616 W/vpnapi (14173): Function: resetCertRegistration File: ConnectMgr.cpp Line: 6462 Invoked Function: PreferenceMgr::getPreferenceValue Return Code: -30343157 (0xFE31000B) Description: PREFERENCEMGR_ERROR_PREFERENCE_NOT_FOUND CertificateStore
03-02 15:45:58.616 I/AnyConnect(14241): KeychainClientStore: Skipping KeychainClientStore due to JB bug.
03-02 15:45:58.616 I/vpnapi (14173): Function: EnumerateClientCerts File: AndroidSNAKCert.cpp Line: 481 determined there are 0 client certificates
03-02 15:45:58.626 I/AnyConnect(14241): KeychainClientStore: Skipping KeychainClientStore due to JB bug.
03-02 15:45:58.626 I/vpnapi (14173): Function: EnumerateClientCerts File: AndroidSNAKCert.cpp Line: 565 got 0 client certificates
03-02 15:45:58.626 I/vpnapi (14173): Function: getCertList File: ApiCert.cpp Line: 473 Number of certificates found: 0
03-02 15:45:58.646 I/vpnapi (14173): Message type information sent to the user: Kontakt wird hergestellt mit x.x.x.x.
03-02 15:45:58.646 I/vpnapi (14173): Initiating VPN connection to the secure gateway https://x.x.x.x
03-02 15:45:58.646 I/acvpnagent(14494): Using default preferences. Some settings (e.g. certificate matching) may not function as expected if a local profile is expected to be used. Verify that the selected host is in the server list section of the profile and that the profile is configured on the secure gateway.
03-02 15:45:58.646 I/acvpnagent(14494): Function: processConnectNotification File: MainThread.cpp Line: 12337 Received connect notification (host x.x.x.x, profile N/A)
03-02 15:45:58.656 I/AnyConnect(14241): NetworkComponentHostService: Posting message to run updateComponentState()
03-02 15:45:58.656 I/AnyConnect(14241): NetworkComponentHostService: updateComponentState: from=IDLE/Getrennt, to=TRANSITION/Verbindung wird hergestellt... for com.cisco.anyconnect.vpn.android.avf
03-02 15:45:58.666 W/acvpnagent(14494): Function: ObtainProxySettings File: PublicProxies.cpp Line: 128 ProxySettings preference not supported on this platform.
03-02 15:45:58.666 I/acvpnagent(14494): Function: respondToConnectNotification File: MainThread.cpp Line: 5337 The requested VPN connection to x.x.x.x will target the following IP protocols and addresses: primary - IPv4 (address x.x.x.x), secondary - N/A.
03-02 15:45:58.666 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:45:58.666 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:45:58.676 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:45:58.676 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:45:59.307 I/vpnapi (14173): Function: getUserName File: CTransportCurlStatic.cpp Line: 2183 PasswordEntry username is u0_a158
03-02 15:45:59.337 E/vpnapi (14173): Function: VerifyCertName File: VerifyServerName.cpp Line: 150 Certificate name verification has failed. Server Name: x.x.x.x Subject Alternate Name(s): xyz.com
03-02 15:45:59.337 E/vpnapi (14173): Function: VerifyCertName File: OpenSSLCertUtils.cpp Line: 1460 Invoked Function: CVerifyServerName::VerifyCertName Return Code: -31391725 (0xFE210013) Description: CERTIFICATE_ERROR_VERIFY_NAME_FAILED
03-02 15:45:59.347 E/vpnapi (14173): Function: VerifyCertName File: VerifyServerName.cpp Line: 150 Certificate name verification has failed. Server Name: x.x.x.x Common Name(s): xyz.com
03-02 15:45:59.347 W/vpnapi (14173): Function: Verify File: FileCertificate.cpp Line: 648 server name verification failed
03-02 15:45:59.347 I/vpnapi (14173): Function: addToCertChain File: AndroidSNAKCert.cpp Line: 1147 added 1380 bytes to head of 1 cert chain
03-02 15:45:59.347 I/vpnapi (14173): Function: addToCertChain File: AndroidSNAKCert.cpp Line: 1147 added 2212 bytes to head of 2 cert chain
03-02 15:45:59.347 I/vpnapi (14173): Function: initializeCertVerifyRequest File: AndroidSNAKCert.cpp Line: 1261 created message with 2 certificates (3592 bytes) for host='x.x.x.x'
03-02 15:45:59.367 D/AnyConnect(14241): CertificateManager: Certificate #0
03-02 15:45:59.367 D/AnyConnect(14241): CertificateManager: Subject : CN=xyz.com, OID.1.2.840.113549.1.9.1=#1628486F7273742E476F7474736368616C6B406C626261752E7361636873656E2D616E68616C742E6465, L=xyz, ST=xyz, OU=xyz, O=xyz, C=xyz 15:45:59.367 D/AnyConnect(14241): CertificateManager: Issuer : STREET=xyz, L=Netphen, OID.2.5.4.17=57250, ST=Nordrhein Westfalen, CN=TeleSec ServerPass CA 2, OU=Trust Center Services, O=T-Systems International GmbH, C=DE
03-02 15:45:59.367 D/AnyConnect(14241): CertificateManager: Certificate #1
03-02 15:45:59.367 D/AnyConnect(14241): CertificateManager: Subject : STREET=xyz, L=xyz, OID.2.5.4.17=57250, ST=xyz, CN=TeleSec ServerPass CA 2, OU=Trust Center Services, O=T-Systems International GmbH, C=DE
03-02 15:45:59.367 D/AnyConnect(14241): CertificateManager: Issuer : CN=Baltimore CyberTrust Root, OU=CyberTrust, O=Baltimore, C=IE
03-02 15:45:59.367 I/AnyConnect(14241): CertificateManager: Verifying against the system key store...
03-02 15:45:59.387 I/AnyConnect(14241): CertificateManager: checkTrustManager (system): the certificate is trusted
03-02 15:45:59.647 D/dalvikvm(14241): GC_CONCURRENT freed 3245K, 32% free 10106K/14791K, paused 13ms+15ms, total 74ms
03-02 15:45:59.767 D/dalvikvm(14241): GC_CONCURRENT freed 490K, 32% free 10126K/14791K, paused 13ms+22ms, total 66ms
03-02 15:45:59.767 D/dalvikvm(14241): WAIT_FOR_CONCURRENT_GC blocked 5ms
03-02 15:45:59.927 D/dalvikvm(14241): GC_CONCURRENT freed 544K, 32% free 10093K/14791K, paused 17ms+6ms, total 69ms
03-02 15:45:59.927 D/dalvikvm(14241): WAIT_FOR_CONCURRENT_GC blocked 15ms
03-02 15:46:00.080 D/dalvikvm(14241): GC_CONCURRENT freed 511K, 32% free 10093K/14791K, paused 13ms+7ms, total 95ms
03-02 15:46:00.080 D/dalvikvm(14241): WAIT_FOR_CONCURRENT_GC blocked 27ms
03-02 15:46:00.230 D/dalvikvm(14241): GC_CONCURRENT freed 761K, 32% free 10094K/14791K, paused 13ms+6ms, total 58ms
03-02 15:46:00.230 D/dalvikvm(14241): WAIT_FOR_CONCURRENT_GC blocked 21ms
03-02 15:46:00.410 D/dalvikvm(14241): GC_CONCURRENT freed 996K, 32% free 10122K/14791K, paused 3ms+4ms, total 47ms
03-02 15:46:00.410 D/dalvikvm(14241): WAIT_FOR_CONCURRENT_GC blocked 19ms
03-02 15:46:00.630 D/dalvikvm(14241): GC_CONCURRENT freed 931K, 30% free 10470K/14791K, paused 14ms+4ms, total 59ms
03-02 15:46:00.630 D/dalvikvm(14241): WAIT_FOR_CONCURRENT_GC blocked 24ms
03-02 15:46:00.880 D/dalvikvm(14241): GC_CONCURRENT freed 1092K, 27% free 10913K/14791K, paused 14ms+5ms, total 61ms
03-02 15:46:00.880 D/dalvikvm(14241): WAIT_FOR_CONCURRENT_GC blocked 19ms
03-02 15:46:01.180 D/dalvikvm(14241): GC_CONCURRENT freed 1370K, 24% free 11334K/14791K, paused 14ms+4ms, total 70ms
03-02 15:46:01.180 D/dalvikvm(14241): WAIT_FOR_CONCURRENT_GC blocked 40ms
03-02 15:46:01.220 I/AnyConnect(14241): CertificateManager: verifyX509ServerCertForHost: confirm because certificate did not match server: javax.net.ssl.SSLException: hostname in certificate didn't match: <x.x.x.x> != <xyz.com> OR <xyz.com>
03-02 15:46:01.220 I/vpnapi (14173): Function: VerifyServerCertificate File: AndroidSNAKCert.cpp Line: 305 client received response with CONFIRM=0x2
03-02 15:46:01.220 I/vpnapi (14173): Function: ExtractManagedCertificates File: AndroidSNAKCert.cpp Line: 986 got 3 certificates
03-02 15:46:01.220 I/vpnapi (14173): Server certificate validation failed with the following errors: Das Zertifikat entspricht nicht dem Servernamen.
03-02 15:46:01.220 I/AnyConnect(14241): NetworkComponentHostService: Posting message to run updateComponentState()
03-02 15:46:01.220 I/AnyConnect(14241): NetworkComponentHostService: updateComponentState: from=TRANSITION/Verbindung wird hergestellt..., to=ATTENTION/Sicherheitswarnung: Nicht vertrauenswürdiges Zertifikat for com.cisco.anyconnect.vpn.android.avf
03-02 15:46:01.370 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:46:02.471 D/AnyConnect(14173): BannerActivity: User accepted banner
03-02 15:46:02.471 I/AnyConnect(14241): NetworkComponentHostService: Posting message to run updateComponentState()
03-02 15:46:02.471 I/AnyConnect(14241): NetworkComponentHostService: updateComponentState: from=ATTENTION/Sicherheitswarnung: Nicht vertrauenswürdiges Zertifikat, to=TRANSITION/Verbindung wird hergestellt... for com.cisco.anyconnect.vpn.android.avf
03-02 15:46:06.365 E/vpnapi (14173): Function: SendRequest File: CTransportCurlStatic.cpp Line: 1623 Invoked Function: curl_easy_perform Return Code: -30015438 (0xFE360032) Description: CTRANSPORT_ERROR_HTTP_RETURNED_ERROR:The HTTP server returned an error code (>= 400) HTTP status code received 401
03-02 15:46:06.375 E/vpnapi (14173): Function: sendRequest File: ConnectIfc.cpp Line: 3297 Invoked Function: CTransport::SendRequest Return Code: -30015438 (0xFE360032) Description: CTRANSPORT_ERROR_HTTP_RETURNED_ERROR:The HTTP server returned an error code (>= 400)
03-02 15:46:06.375 E/vpnapi (14173): Function: connect File: ConnectIfc.cpp Line: 499 Invoked Function: ConnectIfc::sendRequest Return Code: -30015438 (0xFE360032) Description: CTRANSPORT_ERROR_HTTP_RETURNED_ERROR:The HTTP server returned an error code (>= 400)
03-02 15:46:06.375 E/vpnapi (14173): Function: doConnectIfcConnect File: ConnectMgr.cpp Line: 2124 Invoked Function: ConnectIfc::connect Return Code: -30015438 (0xFE360032) Description: CTRANSPORT_ERROR_HTTP_RETURNED_ERROR:The HTTP server returned an error code (>= 400)
03-02 15:46:06.375 I/vpnapi (14173): Message type warning sent to the user: Connection attempt has failed.
03-02 15:46:06.375 E/vpnapi (14173): Function: processIfcData File: ConnectMgr.cpp Line: 2989 Content type (unknown) received. Response type (failed) from x.x.x.x:
03-02 15:46:06.375 I/vpnapi (14173): Function: processIfcData File: ConnectMgr.cpp Line: 3163 Invoked Function: ConnectMgr::processIfcData Return Code: -30015438 (0xFE360032) Description: CTRANSPORT_ERROR_HTTP_RETURNED_ERROR:The HTTP server returned an error code (>= 400)
03-02 15:46:06.375 I/vpnapi (14173): Message type error sent to the user: Connection attempt has failed.
03-02 15:46:06.375 E/vpnapi (14173): Function: connect File: ConnectMgr.cpp Line: 2211 ConnectMgr::processIfcData failed
03-02 15:46:06.375 E/vpnapi (14173): Function: initiateConnect File: ConnectMgr.cpp Line: 1279 Connection failed.
03-02 15:46:06.375 I/acvpnagent(14494): Function: OnIpcMessageReceivedAtDepot File: MainThread.cpp Line: 4657 Received connect failure notification (host x.x.x.x, profile N/A)
03-02 15:46:06.375 I/vpnapi (14173): VPN state: Getrennt Network state: Es kann auf das Netzwerk zugegriffen werden. Network control state: Netzwerkzugriff: Verfügbar Network type: Nicht definiert
03-02 15:46:06.375 E/vpnapi (14173): Function: run File: ConnectMgr.cpp Line: 749 Invoked Function: ConnectMgr::initiateConnect Return Code: -29622263 (0xFE3C0009) Description: CONNECTMGR_ERROR_UNEXPECTED
03-02 15:46:06.475 I/AnyConnect(14173): VpnFragment: Dismiss spinner!
03-02 15:46:06.485 I/AnyConnect(14241): NetworkComponentHostService: Posting message to run updateComponentState()
03-02 15:46:06.485 I/AnyConnect(14241): NetworkComponentHostService: updateComponentState: from=TRANSITION/Verbindung wird hergestellt..., to=IDLE/Getrennt for com.cisco.anyconnect.vpn.android.avf
03-02 15:46:06.495 I/AnyConnect(14241): NetworkComponentHostService: Posting message to run getAllComponentInfo()
03-02 15:46:06.505 I/AnyConnect(14241): NetworkComponentHostService: Posting message to run updateComponentState()
03-02 15:46:06.515 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:46:06.515 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:46:06.515 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:46:06.515 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:46:06.605 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:46:11.460 D/AbsListView(14173): Get MotionRecognitionManager
03-02 15:46:11.670 E/SpannableStringBuilder(14173): SPAN_EXCLUSIVE_EXCLUSIVE spans cannot have a zero length
03-02 15:46:11.670 E/SpannableStringBuilder(14173): SPAN_EXCLUSIVE_EXCLUSIVE spans cannot have a zero length
03-02 15:46:12.941 D/ProgressBar(14173): setProgress = 0
03-02 15:46:12.941 D/ProgressBar(14173): setProgress = 0, fromUser = false
03-02 15:46:12.941 D/ProgressBar(14173): mProgress = 0mIndeterminate = false, mMin = 0, mMax = 10000
03-02 15:46:12.961 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:46:13.042 I/AnyConnect(14173): LoggingActivity: still gathering logs
03-02 15:46:13.242 E/SpannableStringBuilder(14173): SPAN_EXCLUSIVE_EXCLUSIVE spans cannot have a zero length
03-02 15:46:13.242 E/SpannableStringBuilder(14173): SPAN_EXCLUSIVE_EXCLUSIVE spans cannot have a zero length
03-02 15:46:14.033 D/ProgressBar(14173): setProgress = 0
03-02 15:46:14.033 D/ProgressBar(14173): setProgress = 0, fromUser = false
03-02 15:46:14.033 D/ProgressBar(14173): mProgress = 0mIndeterminate = false, mMin = 0, mMax = 10000
03-02 15:46:14.053 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:46:14.103 I/AnyConnect(14173): ProcessOutputParser: Starting to read from Process: logcat -v time AnyConnect:V vpnagent:V acvpnagent:V vpnapi:V vpndownloader:V vpnsnak:V VpnJni:V ConnectivityService:V WifiStateTracker:V WifiMonitor:V AndroidRuntime:V KnoxVpnEngine:V KnoxVpnFirewallHelper:V KnoxVpnEngineService:V GenericVpnPolicy:V *:S
03-02 15:46:18.867 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
03-02 15:46:18.877 D/AbsListView(14173): Get MotionRecognitionManager
03-02 15:46:19.928 D/ProgressBar(14173): setProgress = 0
03-02 15:46:19.928 D/ProgressBar(14173): setProgress = 0, fromUser = false
03-02 15:46:19.928 D/ProgressBar(14173): mProgress = 0mIndeterminate = false, mMin = 0, mMax = 10000
03-02 15:46:19.968 W/ResourceType(14173): Failure getting entry for 0x010802c9 (t=7 e=713) in package 0 (error -75)
What is the best way to log the connection test? Is there a good CLI debug command?
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2016 03:17 AM
Hi,
Please use debug
Regards,
Aditya
Please rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2016 04:11 AM
The debug shows this:
Mar 03 2016 12:56:37 ASA : %ASA-6-302013: Built inbound TCP connection 16099843 for outside:176.4.66.165/48310 (176.4.66.165/48310) to identity:Outside-IP-Primary/60443 (Outside-IP-Primary/60443)
Mar 03 2016 12:56:37 ASA : %ASA-6-725001: Starting SSL handshake with client outside:176.4.66.165/48310 to Outside-IP-Primary/60443 for TLS session
Mar 03 2016 12:56:37 ASA : %ASA-7-725008: SSL client outside:176.4.66.165/48310 to Outside-IP-Primary/60443 proposes the following 23 cipher(s)
Mar 03 2016 12:56:37 ASA : %ASA-7-725012: Device chooses cipher DHE-RSA-AES256-SHA256 for the SSL session with client outside:176.4.66.165/48310 to Outside-IP-Primary/60443
Mar 03 2016 12:56:37 ASA : %ASA-6-725016: Device selects trust-point AC-SSL for client outside:176.4.66.165/48310 to Outside-IP-Primary/60443
Mar 03 2016 12:56:37 ASA : %ASA-6-302014: Teardown TCP connection 16099843 for outside:176.4.66.165/48310 to identity:Outside-IP-Primary/60443 duration 0:00:00 bytes 2744 TCP Reset-O
Mar 03 2016 12:56:48 ASA : %ASA-6-302013: Built inbound TCP connection 16099955 for outside:176.4.66.165/48311 (176.4.66.165/48311) to identity:Outside-IP-Primary/60443 (Outside-IP-Primary/60443)
Mar 03 2016 12:56:49 ASA : %ASA-6-725001: Starting SSL handshake with client outside:176.4.66.165/48311 to Outside-IP-Primary/60443 for TLS session
Mar 03 2016 12:56:49 ASA : %ASA-7-725008: SSL client outside:176.4.66.165/48311 to Outside-IP-Primary/60443 proposes the following 23 cipher(s)
Mar 03 2016 12:56:49 ASA : %ASA-7-725012: Device chooses cipher DHE-RSA-AES256-SHA256 for the SSL session with client outside:176.4.66.165/48311 to Outside-IP-Primary/60443
Mar 03 2016 12:56:49 ASA : %ASA-6-725016: Device selects trust-point AC-SSL for client outside:176.4.66.165/48311 to Outside-IP-Primary/60443
Mar 03 2016 12:56:50 ASA : %ASA-6-302014: Teardown TCP connection 16099955 for outside:176.4.66.165/48311 to identity:Outside-IP-Primary/60443 duration 0:00:01 bytes 2744 TCP Reset-O
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2016 06:38 AM
Hi,
Can you share the output of show run all ssl output ?
Also try using this :
ssl cipher default custom "RC4-SHA256:AES256-SHA"
ssl cipher tlsv1 custom "RC4-SHA256:AES256-SHA"
ssl cipher dtlsv1 custom "RC4-SHA256:AES256-SHA"
ssl trust-point vpn.sellerdeck-2015 outside
vpn-tunnel-protocol ikev1 ikev2 ssl-client
vpn-tunnel-protocol ikev1 ikev2 ssl-client
Reagrds,
Aditya
Please rate helful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2016 06:55 AM
Hi,
I have tried your CLI commands but there is no change. The client shows the same error messages like before. This is the output you have requested:
show run all ssl
ssl server-version tlsv1
ssl client-version tlsv1
ssl cipher default medium
ssl cipher tlsv1 medium
ssl cipher tlsv1.1 medium
ssl cipher tlsv1.2 medium
ssl cipher dtlsv1 medium
ssl dh-group group24
ssl ecdh-group group21
ssl trust-point AC-SSL outside
ssl trust-point ASDM_Launcher_Access_TrustPoint_2 Management
ssl trust-point ASDM_Launcher_Access_TrustPoint_2 Management vpnlb-ip
ssl certificate-authentication fca-timeout 2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2016 10:44 PM
No ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2016 11:51 PM
Hi Heiko,
On checking the debugs I see the following errors:
Nicht vertrauenswürdiges Zertifikat
Untrusted certificates
Das Zertifikat
Could you please check the certificate on the mobile
Regards,
Aditya
Please rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2016 01:52 AM
Hi Aditya,
thanks for the exertion to work with the german debug (-:
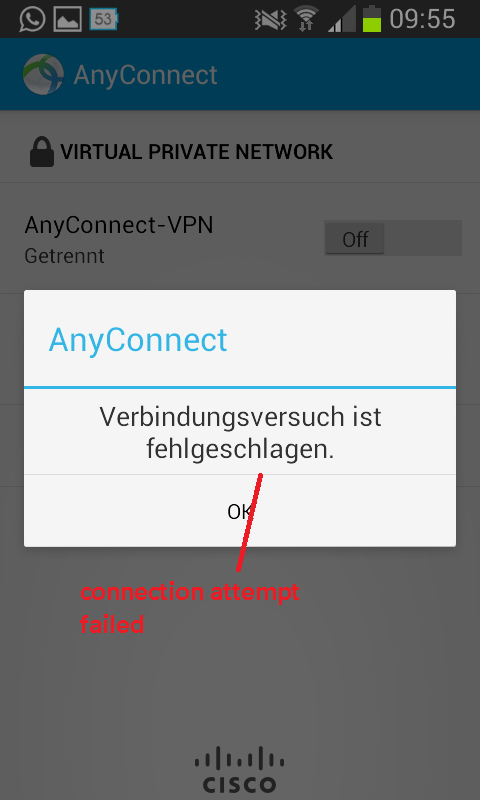
The Anyconnect client shows these messages:
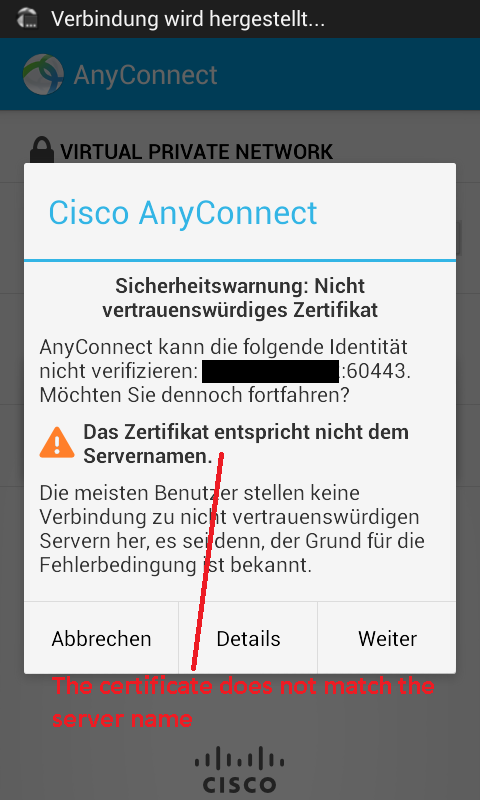
I choose "continue" to accept the certifikate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2016 03:19 AM
Hi Heiko,
This is the reason you are not able to connect.
The certificate on the device is not having the correct server name and since you are using certificates for authentication the connection fails.
Please make sure that we have
Regards,
Aditya
Please rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2016 03:40 AM
Hi Aditya,
I'm not yet so experienced with Cisco ASA and certificate exchange between ASA and the devices. Can you explain the best way to solve the problem. Do I have to create a new certificate on the ASA or do I have install an existing certificate on the devices?
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2016 03:53 AM
Hi Heiko,
I do not think you need to create a new
Apart from mobile devices do other devices work ?
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2016 06:31 AM
I have not managed to install the certificate so far, because for the import in AnyConnect client a password is requested. But I have exported and imported a few times and anyconnect client always says password is wrong.
If I test it with a Windows PC I get the following message:
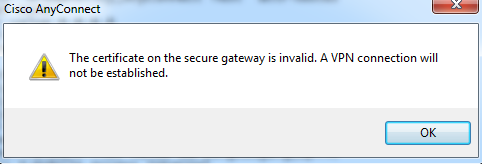
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2016 06:52 AM
Seems to me if you only change was the code update, than backing out of the update should fix things.
I saw one comment above about the hostname/domain name. Rule Number one when dealing with certificates and IPSEC, never, ever, ever change the host/domain name on your ASA without getting new certs and/or trustpoints. Most rely on a match of the hostname and the CN.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

