- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Anyconnect Perfect Forward Secrecy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2018 02:13 PM - edited 03-12-2019 04:59 AM
I want to use PFS for my Anyconnect remote access VPN. I don't see any documentation on how I can make that happen. Any recommendations for the config would be greatly appreciated.
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2018 11:33 PM
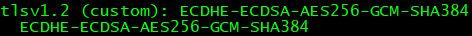
You can enforce Forward Secrecy by disabling all non-DHE ciphers. If you have AnyConnect4 and no legacy clients, it works without any problems. This is my ASA with only forward secrecy:
ssl server-version tlsv1.2 ssl cipher tlsv1.2 custom "ECDHE-ECDSA-AES256-GCM-SHA384 ECDHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES256-GCM-SHA384 ECDHE-ECDSA-AES256-SHA384 ECDHE-RSA-AES256-SHA384 DHE-RSA-AES256-SHA256" ssl cipher dtlsv1 custom "DHE-RSA-AES256-SHA DHE-RSA-AES128-SHA" ssl dh-group group14
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2018 11:33 PM
You can enforce Forward Secrecy by disabling all non-DHE ciphers. If you have AnyConnect4 and no legacy clients, it works without any problems. This is my ASA with only forward secrecy:
ssl server-version tlsv1.2 ssl cipher tlsv1.2 custom "ECDHE-ECDSA-AES256-GCM-SHA384 ECDHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES256-GCM-SHA384 ECDHE-ECDSA-AES256-SHA384 ECDHE-RSA-AES256-SHA384 DHE-RSA-AES256-SHA256" ssl cipher dtlsv1 custom "DHE-RSA-AES256-SHA DHE-RSA-AES128-SHA" ssl dh-group group14
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2019 10:32 PM
Thank you for the custom ciphers. This tweak boosted my SSL Labs score to an A!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2019 03:36 AM - edited 10-17-2019 03:37 AM
@Karsten Iwen Thanks for this - I just came across your answer.
FYI I was able to accomplish pretty much the same thing on an FMC-managed FTD device via Devices > Platform Settings > SSL as follows:
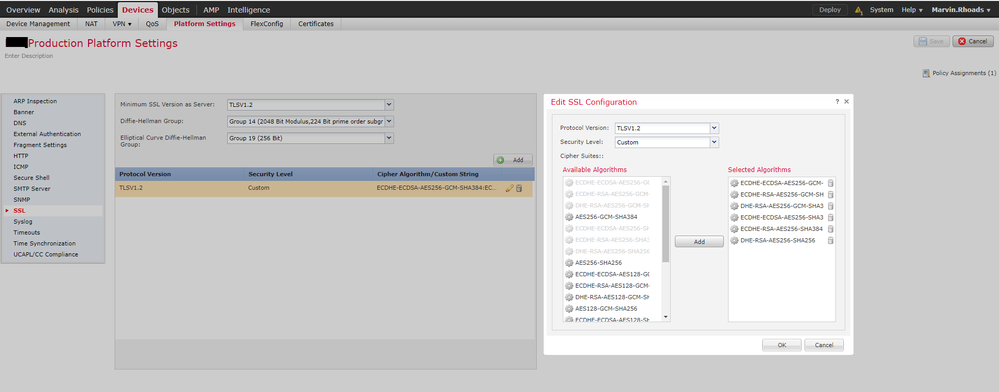
Applying the above settings on an FTD device (mine was running FTD 6.4.0.5) will result in an "A-" Qualys scan score. Cisco's decision not to support secure renegotiation limits us to that:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2021 09:15 PM
FYI all - it appears that Cisco has slipped in "secure renegotation" support recently.
I cannot find it in the release notes (or interim release notes); but I just built a new ASAv in AWS using 9.16(1)28 and was pleasantly surprised to see it earn an "A+" from Qualys. I didn't do anything special beyond the recommendations documented by @Karsten Iwen .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2021 11:22 PM
This is really good news! Took some time …
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2021 10:38 AM
@Karsten Iwen indeed it did!
By the way I just tuned an FTD 7.0 deployment similarly. The settings noted above also result in an A+ for FTD.
Also, as of 7.0 we can make those settings in both FMC- and FDM-managed environments. Previously FDM did not expose those settings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2022 07:36 AM
Karsten,
I have success in using the above ciphers in my ASA-5545's however I am unable to use them in my FP2120's running ASA image, ver 9.16(3)23. I am able to create the custom cipher list for tlsv1.2 only, the rest throw out an error:
ssl server-version tlsv1.2
ssl client-version tlsv1.2
ssl cipher default high
ssl cipher tlsv1.2 custom "ECDHE-ECDSA-AES256-GCM-SHA384 ECDHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES256-GCM-SHA384 ECDHE-ECDSA-AES256-SHA384 ECDHE-RSA-AES256-SHA384 DHE-RSA-AES256-SHA256 "
ssl ecdh-group group20
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 management
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 management vpnlb-ip
PROD-VPN-ASA1-FP2K# config t
PROD-VPN-ASA1-FP2K(config)# ssl cipher tlsv1.1 custom "AES256-SHA:AES128-SHA:D$
ERROR: Unable to create cipher list
ERROR: Unable to update ciphers.
Suggestions? TAC is scratching their heads on this one as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2022 07:50 AM
With "server-version tlsv1.2" you don't need the ciphers for 1.0 and 1.1 as these versions are disabled anyhow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2022 08:04 AM
1. Generate random Diffie-Hellman parameters
a. Configure the server to use a randomly generated Diffie-Hellman group.
2. Disable TLS/SSL support for static key cipher suites
a. Configure the server to disable support for static key cipher suites.
ASA# sh run ssl
ssl server-version tlsv1.2
ssl client-version tlsv1.2
ssl cipher default high
ssl cipher tlsv1 fips
ssl cipher tlsv1.1 fips
ssl cipher tlsv1.2 high
ssl cipher dtlsv1 fips
ssl cipher dtlsv1.2 high
ssl ecdh-group group20
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2022 08:12 AM
Even with "ssl cipher tlsv1.2 high" there are some legacy ciphers enabled. I would manually enable only the best FS-ciphers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2022 09:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 02:13 PM
What are you guys getting for the Key Exchange? Previously, I got 100%, but now I am only getting 90%.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2021 07:24 AM
Yes, key exchange will be scored 90% unless you have a key >= 4096 bits.
https://github.com/ssllabs/research/wiki/SSL-Server-Rating-Guide
Most keys in use today are 2048 bits. Even www.nsa.gov gets 90% due to a 2048 bit key.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2021 08:14 AM
We used to get 100% on Key Exchange, but now we get 90%. We didn't change anything pertaining to our certificate or key.
As you previously mentioned, it looks like Cisco did finally add working Secure Negotitation support because our grade is no longer capped to an A-.
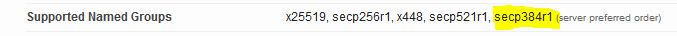
We are only using one cipher (see below).
However, the report lists these.
I assume the score is getting capped at 90% because it's choosing another cipher first. However, I don't understand where it's getting the other ones from. Our goal is to only use (force) secp384r1.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide