- Cisco Community
- Technology and Support
- Security
- VPN
- Anyconnect VPN cert update
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Anyconnect VPN cert update
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2015 01:23 PM - edited 02-21-2020 08:10 PM
Today I had to update the cert for the vpn.domain.com on my Cisco ASA. Now all my vpn based IP phones are broken. Do we need to update something on the phones to get them back online?
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2015 02:03 PM
Not a good scenario. Sorry to be the bearer of bad news, but when you update an ASA certificate in an environment where VPN phones are in use, there are a couple of prerequisite steps.
Basically the new certificate has to be exported from the ASA to Call Manager and then phones need to get the instruction to trust it from the same CM. Unless and until that's done, they will be dead in the water.
There are a couple of TAC articles that talk about the steps in more detail:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2015 10:23 AM
Ok I reverted the cert back to the old one so phones can connect again. I imported the new cert to UCM and applied the config to the phone in hopes it will grab the new cert. Per TAC. but now how can I verify that the new cert was pushed to the phones? Also is there a way to apply config to like 50 phones?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2015 10:33 AM
When you reset a phone it should pull the new certificate trust list from UCM.
You should be able to see it on the phone via Settings > Security Security Configuration > Trust List.
By the way, make sure the new certificate is NOT SHA-2 if you're running UCM 9.x or earlier.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2015 10:37 AM
I am running 8.6 so how do I check that setting? Sorry I am 4 months new to phones...I miss my routing and switching days...so much easier!
Also if I don't have the physical phone in my hands is there a way I can check?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2015 10:43 AM
If you have the actual certificate file, just right click on it in Windows and open it. The Details tab will list all of the attributes, including the Signature Hash Algorithm (SHA) type.
There's a procedure for verifying the update process from UCM described in this thread.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2015 10:46 AM
Sha1
sha256
I think I am good
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2015 02:04 PM
Hi Steven,
You will need to get the new SSL certificate install it on the ASA, place it on the outside as before:
ssl trustpoint <TRUSTPOINT_NAME> <Interface_Name>
Then export it from the ASA and import it on the CUCM certs:
ASA:
crypto ca export <Trustpoint_Name> identity
Then you copy the Base-64 characters and paste them on a notepad and save as extension .pem
Go to Cisco Unified Operating System Administration > Security > Certificate Management > Upload Certificate/Certificate Chain
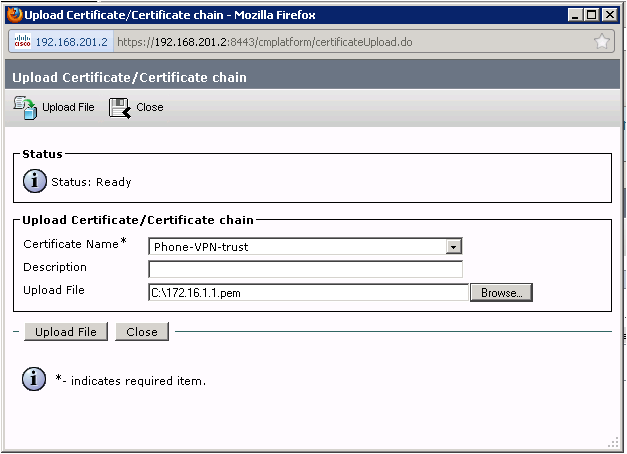
Then removed the previous expired cert, and place the new one on the VPN gateway:
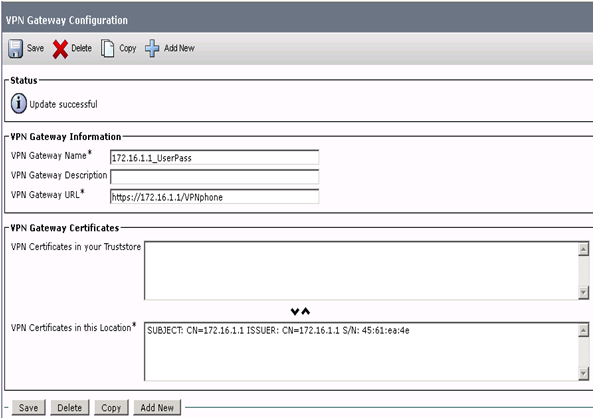
Then connect the phones locally to the CUCM to import the new profile with the new cert, and then try to connect.
Take a look to this guide a peer created just in case:
https://supportforums.cisco.com/document/85976/ip-phone-vpn-basic-configuration-example
Please proceed to rate and mark as correct the helpful Post!
David Castro,
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2015 04:16 PM
This isn't following for 9.1 ASA code. Looks like I can export as a .pem file straight from ASDM.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2015 04:43 PM
You can export the Identity cert from the ASDM as well extension .pem, then afterwards proceed to upload it to the CUCM and the steps I gave you before.
Please proceed to rate and mark as correct this post!
David Castro,
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2015 04:45 PM
Ok I did that and I have added the cert to the certs in this location area for my gateways. The issues is I don't actually have the phones on prem. they are all over the world. So how do they get the update?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2015 04:57 PM
On this case the phones will need to register locally to the CUCM or upload the profile through a TFTP server, under the VPN gateway config on CUCM you will see that:
Enable Auto Network Detect: If enabled, the VPN phone pings the TFTP server and if no response is received, it auto-initiates a VPN connection.
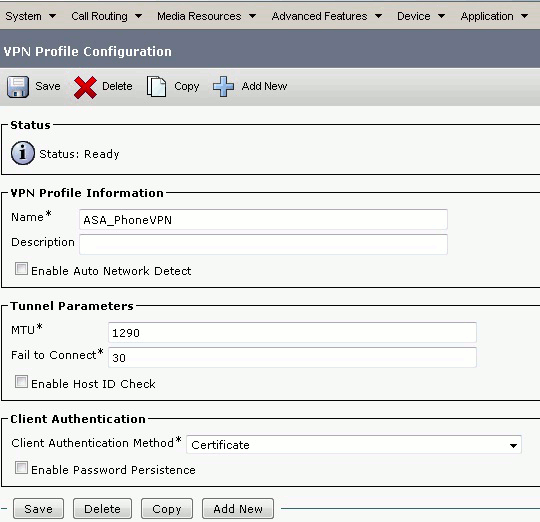
The users will need to get the profile through a TFTP server.
David Castro,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2015 05:03 PM
my client auth method is set to username and password? It was like this when I started my job here so I am unaware of what was done in the past.
Also I assume when we say tftp we mean the CUCM correct? So this would be configured in the phone.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

