- Cisco Community
- Technology and Support
- Security
- VPN
- ASA AnyConnect split-tunnel for local LAN access
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA AnyConnect split-tunnel for local LAN access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2016 07:44 AM - edited 02-21-2020 08:53 PM
I'm running ASA 9.4.2 w/ AnyConnect client v4.2. My VPN configuration uses split-tunneling, I tunnel all RFC1918 networks (10.x.x.x, 192.168.x.x, etc) and let everything else go out the local gateway. The issue I'm experiencing is that many clients are on remote RFC1918 LANs and as a result, when they connect to VPN they can no longer access local network resources.
For instance, a client is on a local LAN 10.0.1.0/24. When they connect to VPN and try to access devices on this network, their traffic gets tunneled instead of hitting the local network. I thought that directly connected networks were supposed to take precedence over VPN routes.
I realize I could make my split tunnel ACL more specific and only tunnel the specific networks that exist inside my environment, but the simplicity of tunneling all private address space is nice and is something I'd rather not change if there's another solution.
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2016 08:29 AM
[@fred.weston@lpga.com]
Seems that we have multi scenarios here, so let me please discuss with you what I have understand so we can proceed on this.
ASA is the VPN device and you want you clients from either your LOCAL network or from internet to connect to you.
These VPN users are allowed to access the RFC1918 networks and this is what is configured in your split tunnel. So if a user connect to VPN, any traffic goes to RFC1918 network will go through VPN, else it will go to the normal gateway. Is this correct ?
You are running into two issues, one is that internet users cannot access your LOCAL network " the RFC1918 network" . The second issue is that you don't want LOCAL VPN users to send their traffic through VPN if they are communicating locally . Is this what you have ?
If we are having that first issue, then we need to check the NAT and ACL config on ASA and check if our traffic left ASA.
For second issue, it is normal for your traffic to go through VPN although it is locally, because when users connect to VPN, the ASA will push the split tunnel routes for them and they will be installed in the machine routing table with the lowest metric ID. If you do "route print" on machines you will see that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2016 09:31 AM
I think you may have misinterpreted what I meant when I say "local" - I mean local to the client.
Here, a diagram may help:
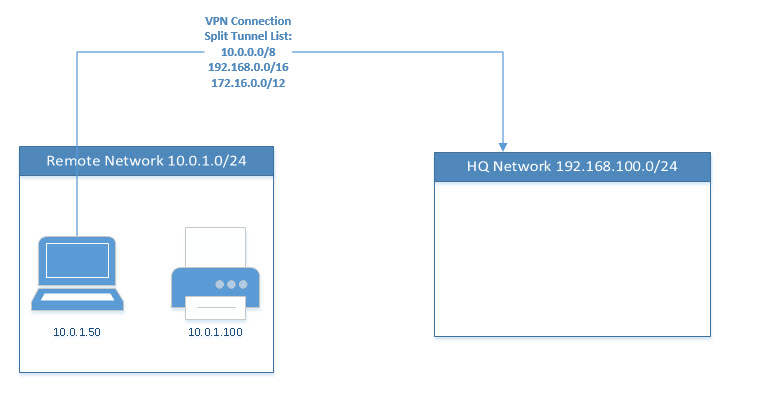
So in this case I have a client 10.0.1.50 on a local network 10.0.1.0/24. This client could be anywhere, the example is just a placeholder for some network which I do not control.
When the client connects to VPN, the split tunnel routes 10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16 get pushed to it. When that happens, the client can no longer access any resources that are on its local LAN because AnyConnect sends the traffic to the ASA instead of allowing it to go out the ethernet port to the local LAN.
If I examine the local IP route table on the client I see that there is an on-link route for 10.0.1.0/24 when the client is disconnected from VPN. When the client connects to VPN, that route is removed and replaced by a secure route for 10.0.0.0/8. So essentially what's happening is the client loses it's route to it's local LAN when it connects to VPN.
I'm trying to figure out if there's a way to prevent this from happening. In the old IPsec client there was an option for local LAN access which would prevent the VPN client from overriding a route to the local network. Is there something similar for AnyConnect?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2016 09:36 AM
Nevermind - there is still an "allow local LAN access" option under anyconnect preferences. Checking this solved the problem.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide