- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Ask Me Anything- VPN Configuration and Troubleshooting on Firepower and ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ask Me Anything- VPN Configuration and Troubleshooting on Firepower and ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2019 04:16 PM - edited 02-21-2020 09:44 PM
This topic is a chance to discuss more about the best configuration and troubleshooting practices on Firepower and Adaptive Security Appliance (ASA). The session focuses on solving all queries related to the deployment of VPN on Cisco Firepower and ASA.
To participate in this event, please use the ![]() button below to ask your questions
button below to ask your questions
Ask questions from Wednesday 4th to Friday 20th of September, 2019
Featured Experts

 Puneesh Chhabra is a Technical Consulting Engineer in the Cisco High-Touch Technical Services (HTTS) team. He has total of 10 years of experience in network security. He has delivered multiple trainings on Cisco firewalls and VPN solutions. Prior to joining Cisco, he worked at IBM and HCL as network security consultant. He holds a bachelor of Science degree in IT. He has achieved his CCIE certification in Security. (CCIE Security #30128)
Puneesh Chhabra is a Technical Consulting Engineer in the Cisco High-Touch Technical Services (HTTS) team. He has total of 10 years of experience in network security. He has delivered multiple trainings on Cisco firewalls and VPN solutions. Prior to joining Cisco, he worked at IBM and HCL as network security consultant. He holds a bachelor of Science degree in IT. He has achieved his CCIE certification in Security. (CCIE Security #30128)
Aditya & Puneesh might not be able to answer each question due to the volume expected during this event. Remember that you can continue the conversation on the VPN and AnyConect community.
Find further events on https://community.cisco.com/t5/custom/page/page-id/Events?categoryId=technology-support
**Helpful votes Encourage Participation! **
Please be sure to rate the Answers to Questions
- Labels:
-
AnyConnect
-
Other VPN Topics
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2019 02:47 AM
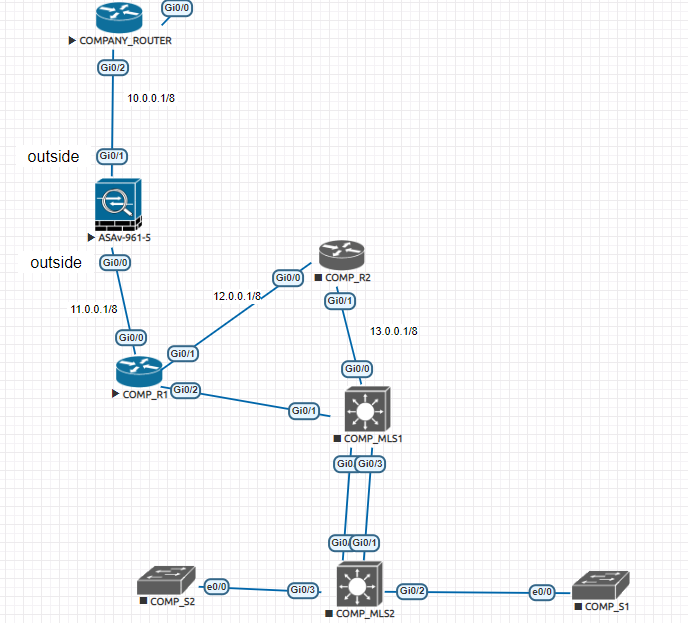
I have configured ASAV IN EVE-NG
on company_router connected to ASA i configured
1: DHCP
2: NAT
ON ASA g0/1 getting ip from DHCP
and this interface is configured as outside with security-level 0
other interface is inside with security-level 100
ping is not working as 10.0.0.1 toward 11.0.0.1 (11.0.0.1 is the inside interface of the ASA)
I configured on ASA for to making ping possible as
icmp permit any any but it does not work then
policy-map global-policy
class inspection_default
inspect icmp the second solution also does not work then
access-list 100 extend permit tcp any any it also does not work
I run EIGRP for neighbor ship
then what the problem is ???????
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2019 07:51 AM
Hi,
Configure the command management-access inside (name of the interface on ASA).
If you have a NAT configured use route-lookup keyword at the end of the NAT on the ASA.
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2019 10:38 AM
Hi Wajib,
Are you able to ping other IPs on the 11.0.0.0/8 network except ASA interface IP. ? May be you can try pinging gig 0/0 on Comp_R1.
We cannot ping the far side interface on ASA by design. The ASA only responds to ICMP traffic sent to the interface that traffic comes in on; you cannot send ICMP traffic through an interface to a far interface. Below is a link which states the same:
Browse to "ICMP" and under it "usage Guidelines":
The exception to above rule would be when you're coming via VPN and you can use management-access as Aditya mentioned.
Regards,
Puneesh
Please rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2019 05:27 AM
Hello Team,
Thank you for this opportunity, i have just purchased a new cisco box and i need to migrate the config from the old one to the new one. the problem is that the older one is an ASA while the newer one runs FDM. i want want the best way to migrate the configs without manually configuring every single thing. or worst case, migrate most of the configs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2019 08:07 AM
Hello Sean,
Unfortunately, the current ASA to FTD migration tool does not migrate VPN configuration and hence the process of configuring VPN on the migrated FTD has to be performed manually.
We will have this request addressed soon in the newer versions for the Migration tool.
Please check these links for the same:
For troubleshooting issues on the VPN, please refer to some helpful commands:
For IKEv1:
show running-config crypto show crypto ikev1 sa detailed show crypto ipsec sa detailed show vpn-sessiondb detail l2l
For IKEv2:
show running-config crypto show crypto ikev2 sa detailed show crypto ipsec sa detailed show vpn-sessiondb detail l2l
For Certificates:
show running-config crypto ca show crypto crypto ca certificate
For RA VPN:
show running-config webvpn show vpn-sessiondb detail anyconnect
Apart from this, ensure that you follow the documents to configure and verify the VPN on the new device.
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2019 11:18 PM
Do we have any way to keep the vpn up beyond the rekey lifetime without sending any traffic on it. If not can we raise an enhancement for the same?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2019 11:26 PM - edited 09-04-2019 11:35 PM
Hi,
Ideally, this is not a good practice due to security constraints and rekey also needs to happen.
You can disable the idle timeout (under the group-policy settings) and increment the association lifetime for phase 2 to the maximum.
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 12:13 AM
Why we use below command what is the significance of it and please don't give me theoretical answer give me practically answer if you have used it .
Route Interface_name 0 0 tunneled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 12:28 AM
It used to set the default gateway for VPN traffic.
Little bit of theory:
You can define a separate default route for tunneled traffic along with the standard default route. Unencrypted traffic received by the ASA, for which there is no static or learned route, is routed through the standard default route. Encrypted traffic received by the ASA, for which there is no static or learned route, will be passed to the gateway defined through the tunneled default route.
In order to define a tunneled default route, use this command:
route <if_name> 0.0.0.0 0.0.0.0 <gateway_ip> tunneled
Ref link:
https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/112182-ssl-tdg-config-example-00.html
Practial use:
For Eg. When you have a default route on ASA pointing towards outside but you want to route all your VPN users to Inside. If you have multiple VPN pools, instead of adding static routes for all the pools, you can simply use the tunneled route to point them towards inside.
Tunneled route is also default route but for VPN traffic only and it can co exist with default route on the firewall.
Regards,
Puneesh
Please rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 12:36 AM
Hi Gaurav,
Sure, this feature is used for multiple scenarios.
I can quote one for your understanding:
If you have an inline web filter installed on the inside interface between the ASA and the inside network router. AnyConnect clients are tunneling all traffic back to the ASA and Internet-bound traffic from the clients will be hair-pinning back out the ASA successfully. That VPN traffic will not be seen by the web filter. Here comes the use of the tunneled default route feature. You can add the tunneled default route for the traffic to the inside network router which in turn would pass the traffic back through the web filter and out the ASA.
It provides an easy way to define a separate default route for the traffic incoming from VPN connections (encrypted traffic) towards internal networks since the device itself needs the normal default route for the VPN connections return traffic which is learned from the external network.
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 01:18 AM
Thanks for the reply on the same .
However I would like to throw another question ..
In case of Site to Site tunnel I have a case where I need to make a VPN tunnel on the peer siting on the inside interface and at the same time I have a default route pointing towards Outside interface so in this case where peer sitting on the inside interface will it need separate default route with tunnelled keyword towards inside interface or a static route for that peer IP will work in this case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 02:25 AM
In this case, you can use a static route.
Regards,
Puneesh
Please rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 08:17 PM
Hi Aditya
When you restore the ASA configuration running any connect with SSL to another ASA of different model i can see that keypair name used in the old firewall is different then the new one which comes up after restoration i used the restore functionality from ASDM so question is will this impact on the anyconnect connections when i will make the device live .
also can you confirm is this the ideal way to restore configuration from OLD box to new one specially if it is having SSL certifcates which is CA signed .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2019 09:05 AM
Hi Adithya / Punnesh,
Trust your doing well! And you guys really rock during the real troubleshooting & have learnt much from you guys during the TAC cases & via your forums. Appreciate it much.
I just wanted to understand the different between the FlexVPN and DMVPN. And also would like to learnt more about different types of VPN in marked except Site to site and RA-VPN.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide