- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Authentication Attempts Logs On FTD FirePOWER 2130 or FTD Cisco ISA 3000
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2019 03:15 PM - edited 02-21-2020 09:39 PM
Community,
Has anyone been able to successfully get syslog messages from an FTD device for successful or failed authentication attempts via SSH? I have my FTD appliances (FirePOWER 2130 and FTD Cisco ISA 3000s) sending logs to a remote syslog server. I see the intrusion and acl logs but not user authentication logs. Any feedback would be appreciated.
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2019 12:43 PM
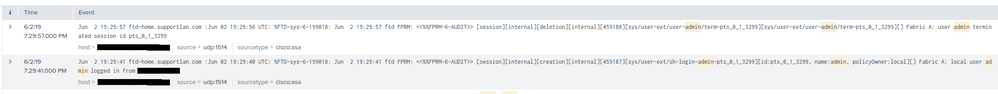
I tried on my FTD 6.4.0 version and it works.
I've a quick and dirty rules to show you an example.
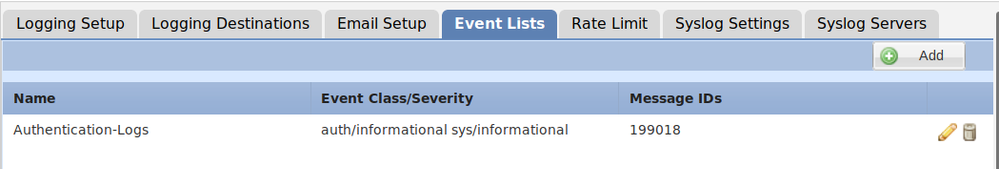
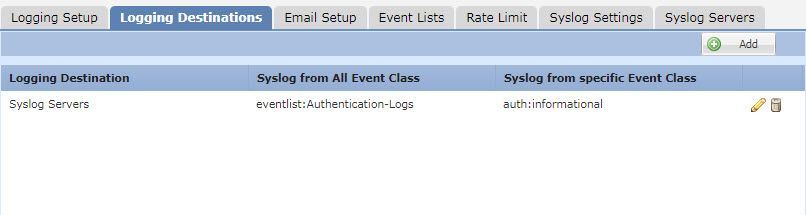
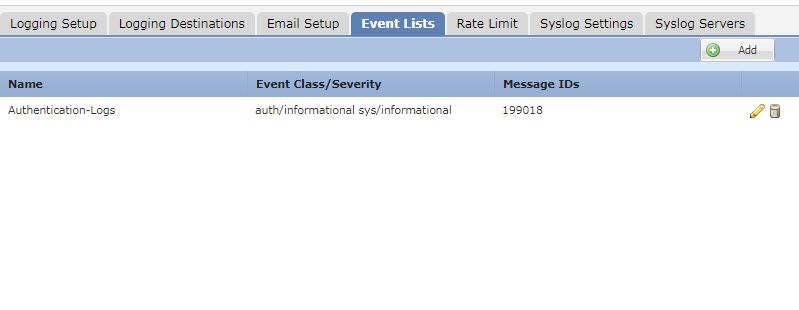
Syslog message ID that is responsible for login and logout is: 199018
On FMC:
On splunk:
Let me know if that works for you as well
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2019 08:50 PM
Are your devices managed by FMC?
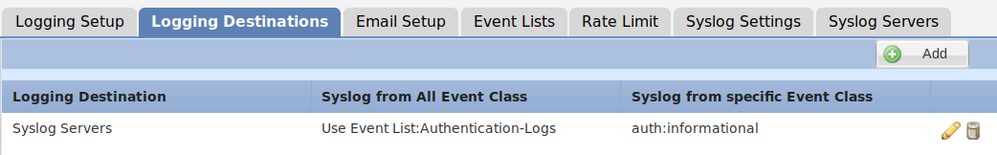
If so, when you create platform settings configuration, into syslog menu:
- you can create an event list for auth with informational level on event lists tab.
- then under logging destination tab, you can tell that the previous created event list should be redirected to syslog.
This should do the trick. Have you tried it?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2019 03:42 AM - edited 05-31-2019 03:43 AM
Thanks for the feedback, Francesco. Yes, the FTDs are managed by FMC. I did create an event list and syslog destinations in the syslog settings for auth but nothing. I see other logs from the system but not those. Involved Cisco TAC and two of them couldn’t figure something it out either. Cisco documentation shows that this type of logging is available to be configured as there are configuration options to configure it just like you mention but I fail to see those logs which baffles me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2019 09:54 PM
I'll try on my 6.4.0 version and let you know.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2019 12:43 PM
I tried on my FTD 6.4.0 version and it works.
I've a quick and dirty rules to show you an example.
Syslog message ID that is responsible for login and logout is: 199018
On FMC:
On splunk:
Let me know if that works for you as well
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2019 02:49 PM
Thanks for that feedback. Below is my setup to mimick what you sent for testing. I have confirmed in the two external logging destinations that they are only seeing SYS LOG IDs of 199017, 430002 and 430003. There has to be something I am missing. My version of FMC is 6.3.0.77
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2019 02:50 PM
Thanks for that feedback. Below is my setup to mimick what you sent for testing. I have confirmed in the two external logging destinations that they are only seeing SYS LOG IDs of 199017, 430002 and 430003. There has to be something I am missing. My version of FMC is 6.3.0.77
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2019 09:46 PM
Can you upgrade to 6.4 train and test again?
Otherwise no other choice to wait tac feedback to see why you're not getting logs like me in your running version.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2019 01:33 PM
I upgrade both FMC and the FTD 2130 and I still dont see the appropriate message Sys ID I need. Quite odd. I now have the same setup as you do above and I am still missing those logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2019 01:34 PM
I upgrade both FMC and the FTD 2130 and I still dont see the appropriate message Sys ID I need. Quite odd. I now have the same setup as you do above and I am still missing those logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2019 04:12 PM
Sorry for the confusion here. I actually did away with the plenty of logs that were coming through to the device and used the range 101001-199021 to see if anything would go through. I got the syslog ID for 199018 for successful authentication. However, for the unsuccessful authentication. I dont get that. Anyone know what that would be. I am going to try the whole range and see if anything comes through.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2019 08:22 PM
There's a link on Cisco if you search for Cisco ftd syslog message id and you'll be able to confirm and test it.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2019 05:54 PM
After working with several TAC engineers, there appears to be no resolution at the moment. While we can get a log message for successful authentication to the FTD 2130s and ISA 3000s, we can not get a log message for invalid or failed authentication attempts. I tested with a brute force attack via SSH more that 1K times and not a single message was logged on the asset that someone was attempting to log in and trying to do so with bad credentials. Eventually a bug was provided and it was updated today to include the 2100s. Waiting to see if the ISA 3000s will be added and wait for the resolution.
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvm16200/?rfs=iqvred
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2019 08:06 PM
Thanks for letting us know the TAC's findings.
I notice they filed that as an enhancement request. I'd argue it should be a defect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2019 04:53 AM
Still working on the issue with our entity's Cisco SE. I have tested this multiple attempts to no avail. Issue was raised to Cisco's BU. The BU thinks that the functionality to log failed log attempts was added in 6.4 code. I have done extensive testing on 6.4 code including the 6.4.0.1 patched code. No dice. Will see if the issue can be raised further as a bug for a fix.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide