- Cisco Community
- Technology and Support
- Security
- VPN
- Automatic timeout for AnyConnect logins
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Automatic timeout for AnyConnect logins
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2023 06:50 AM
We are running version 7.0.5 on our FMC and 7.0.4 on our FTDs. We use a local database for VPN authentication. Is there an accepted or best practice when it comes to automatically logging off VPN users who have left themselves logged in? Up until this point we have just left people logged in as long as they wanted but our thought process is this is starting to become a security concern. For my part I have always wanted to enforce a logoff but was always stopped from doing this.
Thoughts on strategies?
Thanks
- Labels:
-
AnyConnect
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2023 09:34 AM - edited 04-12-2023 09:35 AM
https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect410/administration/guide/b-anyconnect-admin-guide-4-10/configure_vpn.html
Terminating an AnyConnect VPN Connection
Terminating an AnyConnect VPN connection requires users to re-authenticate their endpoint to the secure gateway and create a new VPN connection.
The following connection parameters terminate the VPN session based on timeouts:
-
Maximum Connect Time—Sets the maximum user connection time in minutes. At the end of this time, the system terminates the connection. You can also allow unlimited connection time(default).
-
VPN Idle Timeout—Terminates any user’s session when the session is inactive for the specified time. If the VPN idle timeout is not configured, then the default idle timeout is used.
-
Default Idle Timeout—Terminates any user’s session when the session is inactive for the specified time. The default value is 30 minutes (or 1800 seconds).
If your sessions are not truly idle and still send some traffic even when users are not in front of the computer then the timeout will never be triggered. If you want to log off all users at a specific time then you could use an EEM script like the following (Since you are using FTD you will need to configure it through flexconfig)
https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/118087-technote-asa-00.html#anc7
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2023 04:02 PM
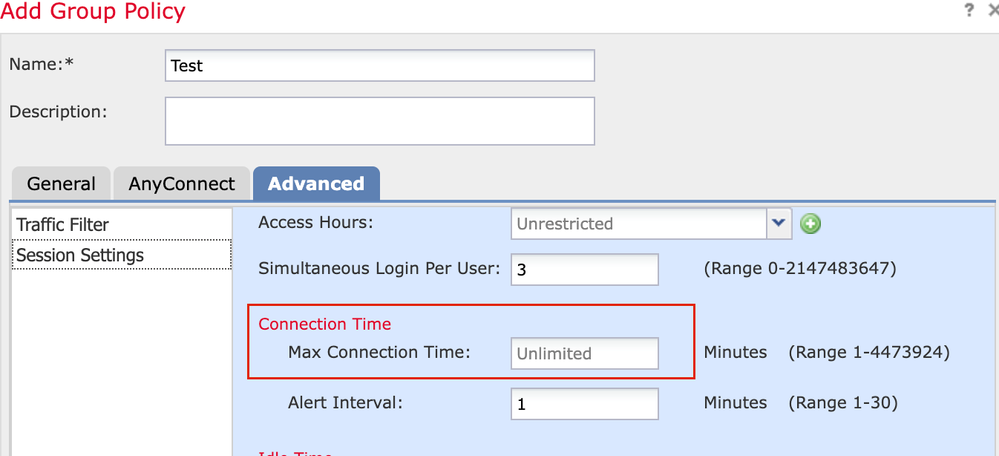
When a Remote User connects to FTD Headend , by default " Maximum connection timeout " is set to unlimited . To avoid Users logged in as long as they wanted , you can configure " Maximum connection timeout " to a certain value and when max connect timeout threshold reaches post vpn connection , the session will be disconnected and user will have to reauthenticate . This setting can be configured/modified on FMC under the " group-policy " that is being used with the connection profile . You can also configure Alert-time interval ( that will alert user , x min time before the max connection timeout ) that could potentially help user wind up or save his work before VPN gets disconnected .
Sharing Screenshot for your reference ( Below )
If you find this information helpful , feel free to like this REPLY
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2023 07:18 PM
The Maximum Connect Time was explained on my previous reply, this is not usually deployed by CU's as the only timeout on a daily basis because end users complain that they could be in the middle of something when the the timeout triggers disrupting their work. Many find more acceptable to rely on idle timeout but ANY traffic will cause this timeout NOT to trigger. There are companies that have fixed schedules and based on their security policy prefer to logoff ALL users at certain time forcing them to authenticate once a day hence deploy the EEM option.
What is usually deployed by many of my customers keeping in mind the user experience is an idle timeout of 8 hours or similar (again, ANY traffic over the tunnel during that period is sufficient to keep the connection alive, however, if users put their machine to sleep it’s very possible they exceed this timeout and are disconnected) and then a session timeout set to something like 7 days, so if they don’t hit the idle timeout or manually disconnect (or reboot, etc.) they should only have to reconnect once a week.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2023 05:36 AM
Gustavo, ( and everyone else)
Thanks for the great information. Just curious, if I set a value in the Maximum Connect time is there a way to display a banner say about about 15 minutes before they are disconnected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2023 05:38 AM
Sorry just saw the answer to this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2023 05:58 AM
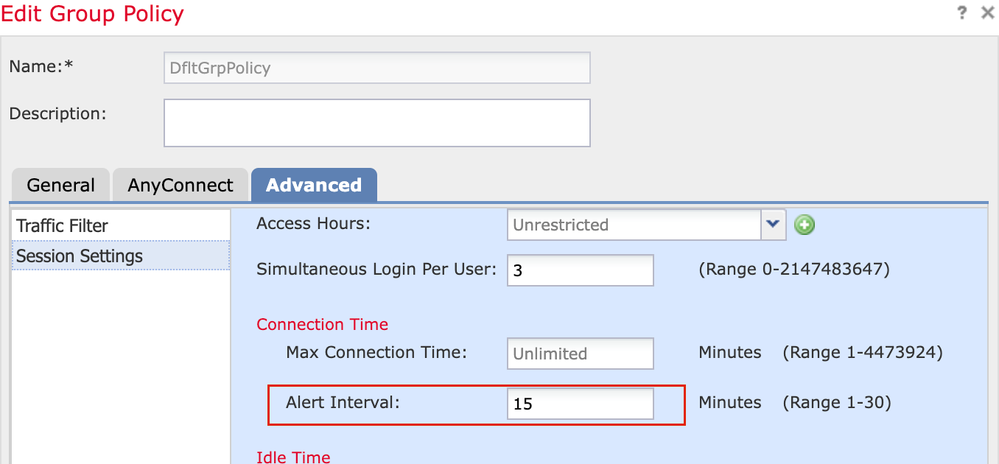
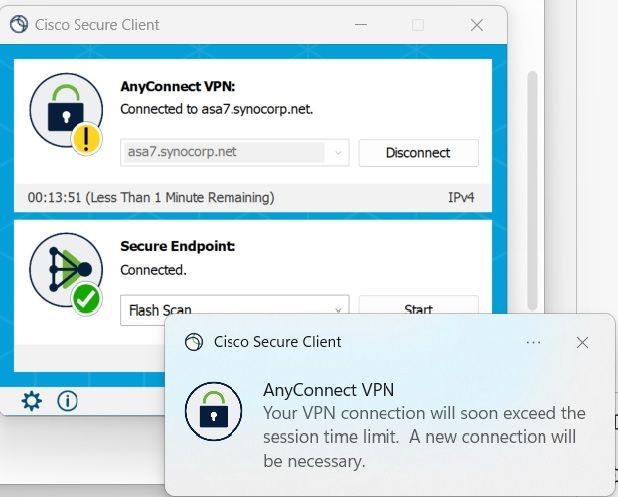
@ethutchinson yes you can do that . You can configure Alert Interval in Group-Policy ( see below SS ) to 15 minutes ( max is 30 min ) that will alert user about vpn session time expiring before they are disconnected . It would not be presented as a banner but a toast notification to the user . This toast notification is not seen in Anyconnect 4.10.x but Cisco Secure Client ( formerly Anyconnect ) 5.0.x onwards .
This is how a toast notification / pop will look like
--> If you find this information helpful , feel free to like
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2023 06:18 AM
So after some consideration with my staff we are thinking about clearing the decks (VPN connection wise) at say 3:00 am. I am thinking there is a way to do a session expiration (for all) at a specified time. They can connect after that obviously.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2023 10:52 AM
@ethutchinson In that case as @Gustavo Medina said , this could be done with EEM . He has created this article long time back and you can use it for your reference https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/118087-technote-asa-00.html#anc7 . On FTD you need to push such EEM via Flexconfig .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2023 08:29 AM
Salman,
Have you ever worked with the "Access Hours" setting under advanced in Edit Group Policy? Could that be used to kick everyone off at say 2:00 in the morning every Sunday? Then everybody could reauthenticate later.
Your thoughts?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2023 10:01 AM
Access Hours defines a time range Users are allowed to connect . It can't be used to achieve the above goal . Also as informed earlier Maximum Connection timeout / Session timeout settings dictates how long a user can stay connected to VPN .
Your ask is " A Scheduled Logoff say 2:00 in the morning every Sunday " which looks achievable with EEM option. I Have not done this in past but i can test this on my end if that's what you are looking for .
Thumbs Up if you find this helpful
Regards
Salman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2023 10:32 AM
@ethutchinson Just tried below EEM on ASA and it worked .
Here i defined a timer event and when event manager applet is triggered, the action on the event manager applet is performed . i-e logoff remote users at a specific time ( as mentioned )
event manager applet Logoff
description Logoff every night
event timer absolute time 17:20:00
action 1 cli command "vpn-sessiondb logoff anyconnect noconfirm"
output none
FYI:- If you are looking to configure it on FTD , you will have to push this EEM via Flexconfig
Thumbs Up if you find this helpful
Regards
Salman
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide