- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Azure network and vFTD and Cisco Anyconnect (Secure Client) issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2023 02:07 AM
Hi!
Please, I need help with the Cisco Anyconnect (Cisco Secure Client) and Azure vFTD. I've tried a bunch of options and feel like I'm missing something. May be some one made the same things.
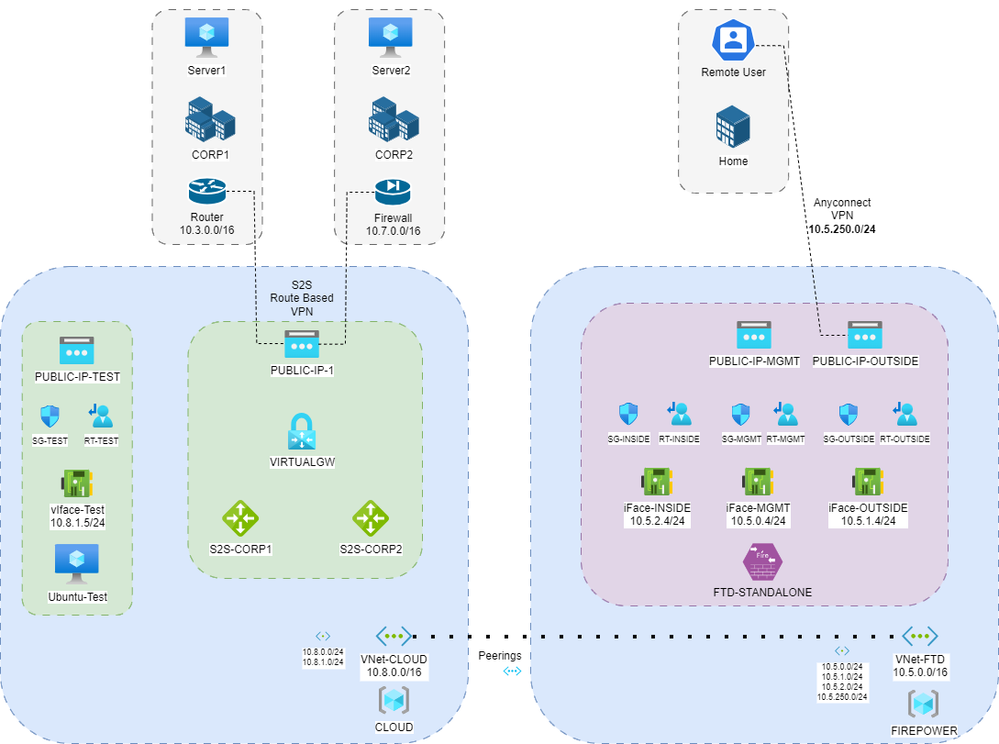
I attached a schema of my test connection lab. The root of idea is unite few networks in one: two on-prem offices, cloud resources and FTD (for Anyconnect only). I managed to implement everything except the connectivity of Anyconnect. All branches can ping each other and also can work cloud resources (linux vm and FTD INSIDE iFace) and vice versa. However, when someone connect to vFTD by Cisco Secure Client all resources are unreachable.
- I created NAT exemption rules on FTD for SSLVPN traffic.
- All Security Groups have ICMP any any allow rule for a test.
- I tested ping to a cloud linux VM and to one branch server (started tcpdump on these VMs) from sslvpn client and saw that VMs got ICMP request and sent replies! But these replies never reached the remote sslvpn enpoint.
- FTD capture-traffic feature doesn't see sslvpn traffic. TShoot tracer shows ALLOWED/NO NAT points.
- Added SSLVPN subnet to VNet of FTD.
I believe that I missed cloud routing or something like this.
Thank you and Happy New Year!
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Remote Access
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2024 06:53 AM
Without diving too deep on your Azure configuration could be a bit complicated to point the problem but as you said sounds like a routing issue in your Azure (UDR), i will say is probably better to get in touch with Azure so they can help you with their environment, but i also found the following documentation that could help since the design is a bit similar to yours:
-JP-
Hope this helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2024 11:47 PM
Hi again,
I won that round!
If you have a virtual net in Azure I mean some net inside VM (linux, windows, fw, etc.) the global Azure system does not know about it. You MUST add route to this net to any object that interacts with that network. In my case it was RouteTables on FTD interfaces for this Anyconnect network: AC net -> GW (INSIDE FTD iface) + on linux VM machine RouteTable AND Virtual Gateway subnet (GatewaySubnet) - made the same RouteTable and attached it to GatewaySubnet with the same route.
First tables help Azure Cloud objects to understand where the net lives.
Second table (GW) helps packets from on-prem devices find this net inside cloud.
RouteTable looks like: Destination Type: IP Address -> Destination IP Addresses -> AC net -> Next hop type: Virtual Appliance -> Next hop address: FTD Inside IP address.
Hope it helps someone.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2024 06:53 AM
Without diving too deep on your Azure configuration could be a bit complicated to point the problem but as you said sounds like a routing issue in your Azure (UDR), i will say is probably better to get in touch with Azure so they can help you with their environment, but i also found the following documentation that could help since the design is a bit similar to yours:
-JP-
Hope this helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2024 12:54 AM
Hi @JP Miranda Z !
Sorry for the late reply, I wanted to make sure that my question was fully answered. Thank you for your awesome answer! Yes, it was UDR! I injected a new route to 10.5.250.0/24 net to all user route tables. Like: 10.5.250.0/24 -> 10.5.2.4 (INSIDE FTD iface). Anyconnect users started seeing cloud resources. But the on-prem resources still not be able to be reached.
I got the dumps from on-prem server and Azure Vitrual GW for IN/OUT packets: pings from AC client to the server. I saw that ICMP requests flowed through VNet peering to Virtual Gateway, then dived to S2S tunnel (ICMP request on Virtual GW was captured), then I saw it on server in traffic dump. Then server generated ICMP response back (I saw this reply in server and then in Virtual GW traffic dump) but then something happened, and packet never reached the FTD/AC client. I could not be able to find Virtual GW route table but I believe that the situation is like with the UDR.
I also asked the question on MS forums but there is not luck. I wanted to publish the full aswer for people who also want to do the same connectivity. This is why I still have not closed the case. I asked my service provider to open a case for MS support and probably I would have the answer soon. I created nginx tcp stream proxy in cloud for AC and on-prem resources connectivity as a point which is visible for all schema members. However, I hope this is the temporary solution.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2024 11:47 PM
Hi again,
I won that round!
If you have a virtual net in Azure I mean some net inside VM (linux, windows, fw, etc.) the global Azure system does not know about it. You MUST add route to this net to any object that interacts with that network. In my case it was RouteTables on FTD interfaces for this Anyconnect network: AC net -> GW (INSIDE FTD iface) + on linux VM machine RouteTable AND Virtual Gateway subnet (GatewaySubnet) - made the same RouteTable and attached it to GatewaySubnet with the same route.
First tables help Azure Cloud objects to understand where the net lives.
Second table (GW) helps packets from on-prem devices find this net inside cloud.
RouteTable looks like: Destination Type: IP Address -> Destination IP Addresses -> AC net -> Next hop type: Virtual Appliance -> Next hop address: FTD Inside IP address.
Hope it helps someone.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide