- Cisco Community
- Technology and Support
- Security
- VPN
- Backup VPN IPsec
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2012 02:47 PM - edited 02-21-2020 06:33 PM
Hi
I´m having some problems in creating a VPN Backup tunnel.
I have the HQ with a router with a primary circuit on F0/0 and a backup circuit on F0/1
Then i have a branch office with a connection to the HQ with a VPN IPSec tunnel.
The problem is that the tunnel goes up and everyting is fine when working with the primary circuit, but when it goes down the backup tunnel doesnt come up, so the ping between the HQ LAN and Branch LAN stop.
Can anyone help me and give me a light??
Thanks in advance
CONFIG HQ
hostname CLIENTA
!
interface FastEthernet0/0
ip address 210.50.50.1 255.255.255.0
ip nat outside
!
interface FastEthernet0/1
ip address 213.50.50.1 255.255.255.0
ip nat outside
!
interface GigabitEthernet1/0
ip address 192.168.1.254 255.255.255.0
ip nat inside
ip virtual-reassembly
negotiation auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0
ip route 0.0.0.0 0.0.0.0 FastEthernet0/1 100
!
ip nat inside source route-map ISP1 interface FastEthernet0/0 overload
ip nat inside source route-map ISP2 interface FastEthernet0/1 overload
!
ip access-list extended NAT
deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
permit ip 192.168.1.0 0.0.0.255 any
!
route-map ISP2 permit 10
match ip address NAT
match interface FastEthernet0/1
!
route-map ISP1 permit 10
match ip address NAT
match interface FastEthernet0/0
!
CONFIG BRANCH
hostname CLIENTB
crypto isakmp policy 100
authentication pre-share
crypto isakmp key cisco1234 address 210.50.50.1
crypto isakmp key cisco1234 address 213.50.50.1
!
crypto ipsec transform-set MYSET esp-des
crypto map MYMAP 100 ipsec-isakmp
set peer 210.50.50.1
set transform-set MYSET
match address VPN
crypto map MYMAP 200 ipsec-isakmp
set peer 213.50.50.1
set transform-set MYSET
match address VPN
!
interface FastEthernet0/0
ip address 200.40.40.1 255.255.255.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map MYMAP
!
interface FastEthernet0/1
ip address 192.168.2.254 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0
!
ip nat inside source list NAT interface FastEthernet0/0 overload
!
ip access-list extended NAT
deny ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
permit ip 192.168.2.0 0.0.0.255 any
ip access-list extended VPN
permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
!
The Scenário
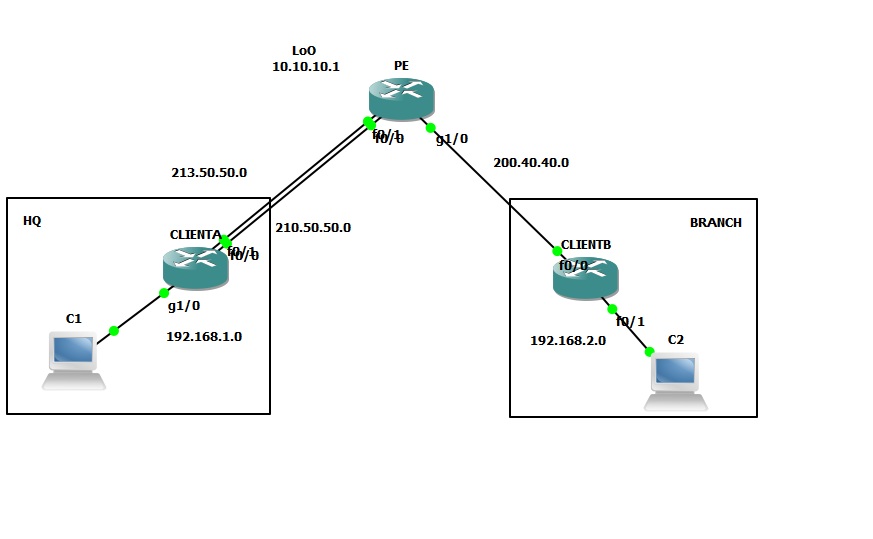
Solved! Go to Solution.
- Labels:
-
IPSEC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2012 03:05 PM
very simple solution.
1- create a loopback interface lo0 on clientA with a public IP address and make sure that this loopback IP address is reachable over the Internet by clientB
2- create an IPSec between clientA and ClientB using clientA loopback0 as the crypto map source "crypto map source loopback0" or something like that on clientA,
3- On clientB, only use clientA loopback0 address and the VPN peer.
That way, the IPSec will operate "independently" whethere ISP1 or ISP2 is available, assuming loopback is reachable via both ISP1 and/or ISP2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2012 04:36 PM
here is what you need to verify:
1- when you shutdown the primary interface, make sure it is "down",
2- after the primary interface is down, perform a ping from clientA sourcing from clientA loopack0 interface to clientB ip address 200.40.40.1 and make sure the VPN Peers can ping each other. I suspect that is the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2012 03:05 PM
very simple solution.
1- create a loopback interface lo0 on clientA with a public IP address and make sure that this loopback IP address is reachable over the Internet by clientB
2- create an IPSec between clientA and ClientB using clientA loopback0 as the crypto map source "crypto map source loopback0" or something like that on clientA,
3- On clientB, only use clientA loopback0 address and the VPN peer.
That way, the IPSec will operate "independently" whethere ISP1 or ISP2 is available, assuming loopback is reachable via both ISP1 and/or ISP2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2012 04:28 PM
Hi David
Thanks for the info, but still not working
I created the LoO on the HQ router and could creat the IP Sec tunnel between HQ and Branch.
When i shut down the primary interface the tunnel goes down on doesnt install through the secondary link......i cant understand the problem because when i shutdown the primary link i can still ping the HQ Lo0 from the Branch but not establish the tunnel.
Thanks for your help!!
The configs:
HQ Router
hostname CLIENTA
crypto isakmp policy 100
authentication pre-share
crypto isakmp key cisco1234 address 200.40.40.1
!
crypto ipsec transform-set MYSET esp-des
!
crypto map MYMAP local-address Loopback0
crypto map MYMAP 100 ipsec-isakmp
set peer 200.40.40.1
set transform-set MYSET
match address VPN
interface Loopback0
ip address 5.5.5.5 255.255.255.0
!
interface FastEthernet0/0
ip address 210.50.50.1 255.255.255.0
ip nat outside
ip virtual-reassembly
shutdown
duplex auto
speed auto
crypto map MYMAP
!
interface FastEthernet0/1
ip address 213.50.50.1 255.255.255.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map MYMAP
!
interface GigabitEthernet1/0
ip address 192.168.1.254 255.255.255.0
ip nat inside
ip virtual-reassembly
negotiation auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0
ip route 0.0.0.0 0.0.0.0 FastEthernet0/1 10
!
no ip http server
no ip http secure-server
!
ip nat inside source route-map ISP1 interface FastEthernet0/0 overload
ip nat inside source route-map ISP2 interface FastEthernet0/1 overload
!
ip access-list extended NAT
deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
permit ip 192.168.1.0 0.0.0.255 any
ip access-list extended VPN
permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
!
route-map ISP2 permit 10
match ip address NAT
match interface FastEthernet0/1
!
route-map ISP1 permit 10
match ip address NAT
match interface FastEthernet0/0
BRANCH Router
hostname CLIENTB
!
crypto isakmp policy 100
authentication pre-share
crypto isakmp key cisco1234 address 5.5.5.5
!
crypto ipsec transform-set MYSET esp-des
!
crypto map MYMAP 100 ipsec-isakmp
set peer 5.5.5.5
set transform-set MYSET
match address VPN
!
interface FastEthernet0/0
ip address 200.40.40.1 255.255.255.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map MYMAP
!
interface FastEthernet0/1
ip address 192.168.2.254 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0
!
no ip http server
no ip http secure-server
!
ip nat inside source list NAT interface FastEthernet0/0 overload
!
ip access-list extended NAT
deny ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
permit ip 192.168.2.0 0.0.0.255 any
ip access-list extended VPN
permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
ISP Router
hostname PE
interface Loopback0
ip address 10.10.10.1 255.255.255.0
!
interface FastEthernet0/0
ip address 210.50.50.2 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 213.50.50.2 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet1/0
ip address 200.40.40.2 255.255.255.0
negotiation auto
!
ip forward-protocol nd
ip route 5.5.5.0 255.255.255.0 FastEthernet0/0
ip route 5.5.5.0 255.255.255.0 FastEthernet0/1 10
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2012 04:36 PM
here is what you need to verify:
1- when you shutdown the primary interface, make sure it is "down",
2- after the primary interface is down, perform a ping from clientA sourcing from clientA loopack0 interface to clientB ip address 200.40.40.1 and make sure the VPN Peers can ping each other. I suspect that is the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2012 03:11 AM
Hi David
Thanks for the answer, it was an ACL and routing problem.
After fixing it all started to work.
Thanks a lot for your help!!!!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide