- Cisco Community
- Technology and Support
- Security
- VPN
- Re: brute force attack from VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2024 02:29 AM - edited 03-11-2024 02:38 AM
Hi all,
I have been experiencing brute force attacks from outside VPN access. Luckily, I have enabled Duo MFA authentication and disabled web portal access
.
However, I found out that people using Cisco secure clients keep accessing the VPN. May I know of any way to limit people's access to the VPN if the password is entered incorrectly more than 3 times and wait 5 to 10 mins?
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2024 03:19 AM
@chocolate2395777 I understand, but you don't have many options here. As already mentioned you could use the control-plane ACL, when you know the IP address of the attack, its not automated but it is an option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2024 02:46 AM
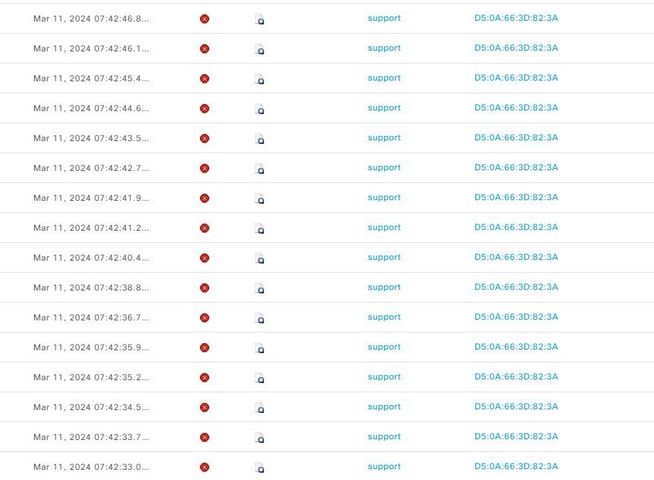
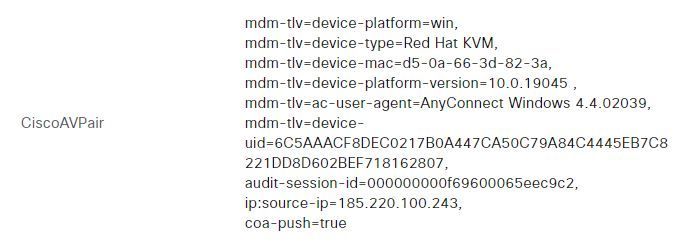
@chocolate2395777 that output looks to be from ISE, you can configure limit the number of consecutive failed login attempts per user in the external user database - Administration > Identity Management > Settings > User Authentication Settings > Lock/Suspend Account with Incorrect Login Attempts.
You could also use a control-plane ACL to restrict traffic from known malicous IP addresses and block them. https://integratingit.wordpress.com/2021/06/26/ftd-control-plane-acl/
You may wish to setup SYSLOG for message - 113015 https://www.cisco.com/c/en/us/td/docs/security/firepower/Syslogs/b_fptd_syslog_guide/syslogs1.html#con_4769508
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2024 02:48 AM
Thanks for your reply.
The FTD is managed by FMC. I couldn't find any option to limit access for users with incorrect passwords,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2024 03:01 AM
@chocolate2395777 is the FMC the authentication source (local database)? You can restrict users when authenticating against external authentication sources. I don't believe there is anything on the FMC that can determine X number of incorrect logins and block.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2024 03:12 AM
@Rob Ingram I am using external authentication sources (AD). I have set it to lock the user after three incorrect password attempts to login. However, I am worried If the attacker continues attempting brute force attacks, it may lead to the consumption of hardware resources.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2024 03:19 AM
@chocolate2395777 I understand, but you don't have many options here. As already mentioned you could use the control-plane ACL, when you know the IP address of the attack, its not automated but it is an option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2024 04:59 AM
When it comes to resources consumption, simple DoS to TCP/443 is much more dangerous than a slow password-guessing attack, although you're right that we don't really know how well DUO works under pressure.
Blocking users after 3 unsuccessful login attempts is not a good idea anyway. Cert+OTP authentication can help block attackers before login prompt and TLS/JA3 filtering on an external device can help block connects from scripts and allow them only from AnyConnect client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2024 09:39 AM
I am seeing a similar issue and wanted to know more of what you meant by blocking TLS/JA3. Do you mean just restricting access to specific ports?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2024 11:00 AM
Google "TLS/JA3" and it will give you all you need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2024 06:22 AM
Actually, it doesn't. I'm not asking to learn about JA3, I'm asking how would one block those protocols on a FTD, but still allow AnyConnect through. And never answer a post with, "Just google it." Have the decency to assume the person has already done research and are coming here for further assistance. Googling it is what got me to this forum post in the first place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2024 07:09 AM
From my post: Cert+OTP authentication can help block attackers before login prompt and TLS/JA3 filtering on an external device can help block connects from scripts and allow them only from AnyConnect client.
You need another device in front of ASA/FTD which is capable of TLS/JA3 filtering.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2024 10:26 PM
Will Administration > Identity Management > Settings > User Authentication Settings > Lock/Suspend Account with Incorrect Login Attempts really limit the login for accounts in external databases (AD) ? My undestanding was upt o now it will limit logins for users created in ISE local database.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2024 07:54 AM
Since the implementation of certificate-based authentication and DUO, no instances of brute-force attacks have been recorded.
As I know for the FTD, using certificate + DUO authentication is the only way to stop brute-force attacks in my situation.
I believe IDP/IPS and threat intelligence can use JA3 to identify attacks for the FTD, but I haven't explored this myself.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2024 01:00 AM
@chocolate2395777, I don't want to upset you, but it was reported on this forum that it is possible to establish TLS connection to ASA/FTD having certificate without private key: https://community.cisco.com/t5/vpn/certificate-auth-not-validating-client-has-private-key/m-p/5123520#M295751
This basically means that certificates is not a panacea too, when it comes to password spray attacks. Fortunately, this "feature" has not been exploited yet, so far as I know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2024 02:26 AM
Thanks for the advice,
I am using an ISE user profiling and DUO will hopefully be able to block password spray attacks.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide