- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Can I have two tunneles IPSec with differents security parameters on the same link?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Can I have two tunneles IPSec with differents security parameters on the same link?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2019 10:09 PM
Hi there!
Currently I have a tunnel IPSec between Router 899/887 and ASA 5545, it's works, but I need create a second tunnel on the same link with different traffic, and differents security parameters.
Can I have two crypto maps in the same outside ASA interface?
- Labels:
-
Other VPN Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2019 10:41 PM
Yes each tunnel can have its on encruption and authentication parameters even if its on the same outside interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 08:33 AM - edited 05-09-2019 08:42 AM
How can do that?
Because I have this configuration on the ASA:
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ipsec ikev1 transform-set myset esp-3des esp-sha-hmac
tunnel-group DefaultL2LGroup ipsec-attributes
ikev1 pre-shared-key *****
crypto dynamic-map mymap 1 set ikev1 transform-set myset
crypto dynamic-map mymap 1 set reverse-route
crypto map dyn-map 5 match address outside_cryptomap
crypto map dyn-map 10 ipsec-isakmp dynamic mymapcrypto map dyn-map interface outside
crypto ikev1 enable outside
My doubt is, I must create two crypto dynamic or two crypto map on the outside interface? I mean,for create other policy and others encryption parameters.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 11:38 AM
Hi,
You would use sequence numbers on the crypto map to distinguish between the different peers, you can then reference the different Transform Set. E.g:-
crypto map CRYPTO-MAP 1 match address R1_VPN
crypto map CRYPTO-MAP 1 set peer 1.1.1.1
crypto map CRYPTO-MAP 1 set ikev1 transform-set VPN-TRANSFORM-1
crypto map CRYPTO-MAP 2 match address R2_VPN
crypto map CRYPTO-MAP 2 set peer 2.2.2.1
crypto map CRYPTO-MAP 2 set ikev1 transform-set VPN-TRANSFORM-2
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 03:22 PM
But my crypto map must be dynamic, because my other side has with many devices, I mean, my crypto map must done the tunnel only with the key. Can I do one crypto map dynamic with secuencial ID?
I mean, Can I do this? on the same link and the same outside asa interface?
This for the first condition.---------
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ipsec ikev1 transform-set myset1 esp-3des esp-sha-hmac
tunnel-group DefaultL2LGroup ipsec-attributes
ikev1 pre-shared-key password1
crypto dynamic-map mymap 1 set ikev1 transform-set myset1
crypto dynamic-map mymap 1 set reverse-route
crypto map dyn-map 1 match address outside_acl1
crypto map dyn-map 1 ipsec-isakmp dynamic mymap
crypto map dyn-map interface outside
This for the second condition.---------
crypto ikev1 policy 20
authentication pre-share
encryption des
hash sha
group 2
lifetime 1400
crypto ipsec ikev1 transform-set myset2 esp-des esp-sha-hmac
tunnel-group DefaultL2LGroup ipsec-attributes
ikev1 pre-shared-key password2
crypto dynamic-map mymap 2 set ikev1 transform-set myset2
crypto dynamic-map mymap 2 set reverse-route
crypto map dyn-map 2 match address outside_acl2
crypto map dyn-map 2 ipsec-isakmp dynamic mymap
crypto map dyn-map interface outside
Regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2019 12:00 PM
Hi,
You can define multiple transform sets under a crypto map, the remote peer intiating the VPN tunnel will negotiate.
crypto ipsec ikev1 transform-set myset1 esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set myset2 esp-des esp-sha-hmac
crypto dynamic-map mymap 1 set ikev1 transform-set myset1 myset2
Define a tunnel-group for each peer IP address
tunnel-group 1.1.1.1 ipsec-attributes
ikev1 pre-shared-key password1
tunnel-group 2.2.2.2 ipsec-attributes
ikev1 pre-shared-key password2
You can only have one crypto map attached to an interface.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2019 12:47 PM
Hi RJI,
But in my case I have 598 peers, I mean, 598 Routers connect to outside ASA interface, So, isn't there way to create a crypto dynamic-map in ASA for connect to my many peers? I mean, for not l put 598 times the router peers.
Regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2019 01:04 PM
The only other real option is certificate authentication, which adds a lot of work to deploy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2019 04:57 PM
Currently I have this configuration :
tunnel-group DefaultL2LGroup ipsec-attributes
ikev1 pre-shared-key *****
With this configuration Can I have success?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 01:07 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 09:50 AM
For your example:
tunnel-group 1.1.1.1 ipsec-attributes
ikev1 pre-shared-key password1
tunnel-group 2.2.2.2 ipsec-attributes
ikev1 pre-shared-key password2
tunnel-group 1.1.1.1 ipsec-attributes
ikev1 pre-shared-key password1
tunnel-group 2.2.2.2 ipsec-attributes
ikev1 pre-shared-key password2
How can difference my keys if I don't set my peers because I will put DefaultL2LGroup on my configuration for the reason that I have dynamic peers?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 10:23 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 11:04 AM
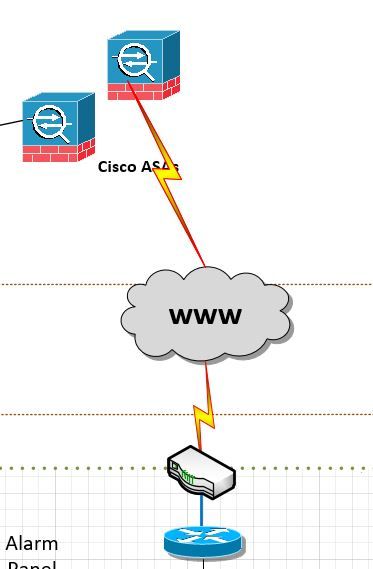
This is my topology.
In my topology 598 routers comunicating with the same ASA, and I have "DefaultL2LGroup" on the ASA for two reasons.
1.- Because I have many peers.
2.- Because the IP isn't static.
(This tunnel IPSec already works). So, in the LAN of the all routers only exist one VLAN, I mean all traffic belong to one VLAN (VLAN2), now I try to divide this traffic in two VLANs (VLAN2) and (VLAN3), but I need to create one tunnel for each vlan, I mean create others security parameters for the "new tunnel" for the VLAN3.
But it must has conditions:
1.-I must use the same link
2.-I must use the same interfaces (Router and ASA).
Now, How can to that? for each tunnel create different security parameters and different keys?
Regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 11:25 AM
Anyway why would you need to do that?...it would make the configuration far too complex.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 11:56 AM
Because for company standard, new traffic it must be in other tunnel ipsec, but they want use the same link and the same interfaces, so it's impossible do that?
I was thinking if I create new statement in the same ACL for this new VLAN also it could works?
When I'll check the configuration with this command I'll see two local-remote for each vlan?
Router#show crypto ipsec sa peer 172.16.1.1
interface: GigabitEthernet0/0
Crypto map tag: outside_map, local addr 172.17.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.20.10.0/255.255.255.0/0/0)---------------VLAN 2
remote ident (addr/mask/prot/port): (10.10.10.0/255.255.255.0/0/0)---------------VLAN 2
current_peer 172.16.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 2024, #pkts encrypt: 2024, #pkts digest: 2024
#pkts decaps: 2015, #pkts decrypt: 2015, #pkts verify: 2015
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 26, #recv errors 0
In conclusion I cannot create two security parameters for my case? Because ASA not support it? If I would want to do that I need use new interfaces on the ASA and Router?
Regards!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide