- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Cisco ASA5505 can't ping internal interface ASA and LAN host
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco ASA5505 can't ping internal interface ASA and LAN hosts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2014 09:58 AM
Hello Guys,
I'm writting to you because I have a problem with VPN. I create VPN Remote Access tunnel on Cisco ASA 5505. I connect to it (cisco asa) via Cisco VPN Client (Windows) and connecting is establishing. I have right IP address (192.168.195.1) from Cisco ASA, i have route to LAN network(192.168.48.0) but i can't ping anything (internal interface Cisco ASA and any hosts in LAN segment). When I use show crypto isakmp sa i see that state is MM_ACTIVE, when i use show crypto ipsec sa i see that packet incoming are encapsulate but count of is 0 -
#pkts encaps: 0, #pkts encrypt:0, #pkts digest: 0
sysopt permit-vpn is enable
I create split and nat_exempt
When i disable sysopt permit-vpn and create outside ACL to allow this communication sill don't work
I don't use NAT-T because ASA is only one network device and it is "router". Behind ASA I have LAN network.
Here you are my config ( I change the IP Adresses )
ciscoasa(config)# sh run
: Saved
:
ASA Version 7.2(2)
!
hostname ciscoasa
domain-name default.domain.invalid
names
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.48.1 255.255.255.0
ospf cost 10
!
interface Vlan2
nameif outside
security-level 0
ip address 6.x.x.x 255.255.255.240
ospf cost 10
!
interface Ethernet0/0
switchport access vlan 2
speed 100
duplex full
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
ftp mode passive
clock timezone CEST 1
clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00
dns server-group DefaultDNS
domain-name default.domain.invalid
access-list inside_nat0_outbound extended permit ip 192.168.48.0 255.255.255.0 192.168.0.0 255.255.0.0
access-list inside_nat0_outbound extended permit ip 192.168.48.0 255.255.255.0 172.25.26.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip 192.168.48.0 255.255.255.0 192.168.195.0 255.255.255.240
access-list outside_access_out remark infopraca deny
access-list outside_access_out extended deny ip any host 194.116.240.115
access-list outside_access_out remark youtube
access-list outside_access_out extended deny ip any host 208.117.236.74
access-list outside_access_out remark youtube
access-list outside_access_out extended deny ip any host 208.117.236.76
access-list outside_access_out remark youtube
access-list outside_access_out extended deny ip any host 208.65.153.253
access-list outside_access_out remark photobucket
access-list outside_access_out extended deny ip any host 209.17.65.10
access-list outside_access_out remark yahoo
access-list outside_access_out extended deny ip any host 209.191.68.218
access-list outside_access_out remark yahoo
access-list outside_access_out extended deny ip any host 209.191.93.51
access-list outside_access_out remark plus.pl
access-list outside_access_out extended deny ip any host 212.2.119.234
access-list outside_access_out remark plus.pl
access-list outside_access_out extended deny ip any host 212.2.96.49
access-list outside_access_out remark onetlajt
access-list outside_access_out extended deny ip any host 212.244.48.59
access-list outside_access_out remark Yahoo
access-list outside_access_out extended deny ip any host 66.90.104.203
access-list outside_access_out remark Yahoo
access-list outside_access_out extended deny ip any host 68.142.200.12
access-list outside_access_out remark Yahoo
access-list outside_access_out extended deny ip any host 68.142.207.34
access-list outside_access_out remark Yahoo
access-list outside_access_out extended deny ip any host 68.142.228.136
access-list outside_access_out remark Yahoo
access-list outside_access_out extended deny ip any host 76.13.6.132
access-list outside_access_out remark Facebook
access-list outside_access_out extended deny ip any 69.63.0.0 255.255.0.0
access-list outside_access_out remark Facebook
access-list outside_access_out extended deny ip any 66.220.0.0 255.255.0.0
access-list outside_access_out extended permit ip any any
access-list outside_access_in extended permit icmp any any echo-reply
access-list outside_access_in extended permit ip 192.168.0.0 255.255.0.0 any
access-list outside_access_in extended permit ip 192.168.195.0 255.255.255.240 any
access-list outside_access_in extended permit tcp any host 192.168.48.244 eq 3389
access-list outside_access_in extended permit tcp any host 6.x.x.x.x eq 3389
access-list outside_40_cryptomap extended permit ip 192.168.48.0 255.255.255.0 192.168.0.0 255.255.0.0
access-list outside_60_cryptomap extended permit ip 192.168.48.0 255.255.255.0 172.25.26.0 255.255.255.0
access-list ra-split-other-company extended permit ip 192.168.48.0 255.255.255.0 any
pager lines 24
logging enable
logging timestamp
logging buffer-size 65536
logging buffered warnings
logging trap critical
logging history notifications
logging asdm informational
logging facility 16
logging device-id hostname
logging host inside 192.168.0.228
logging ftp-server 192.168.1.149 /joannap/ joannap ****
logging permit-hostdown
mtu inside 1500
mtu outside 1500
ip local pool ra-ip-pool-other-company 192.168.195.1-192.168.195.14 mask 255.255.255.240
icmp unreachable rate-limit 1 burst-size 1
icmp permit any inside
icmp permit any outside
asdm image disk0:/asdm-522.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) tcp 6.x.x.x 3389 192.168.48.244 3389 netmask 255.255.255.255
access-group outside_access_in in interface outside
access-group outside_access_out out interface outside
route outside 0.0.0.0 0.0.0.0 6.x.x.x 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
group-policy ra-gp-other-company internal
group-policy ra-gp-other-company attributes
banner value xxxxxxxxxxxxxxxxxxxxx
vpn-tunnel-protocol IPSec
ipsec-udp enable
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ra-split-other-company
username tescik password fdgdfgdfgdgdgd encrypted privilege 0
username tescik attributes
vpn-group-policy ra-gp-other-company
aaa authentication telnet console LOCAL
aaa authentication ssh console LOCAL
http server enable
http xxxxxxxx 255.255.255.255 outside
http xxxxxxxxxxxx 255.255.255.255 outside
http xxxxxxxxxxxxx 255.255.255.255 outside
http xxxxxxxxxxxxx 255.255.255.255 outside
http xxxxxxxxxxxxxxxxxx 255.255.255.0 outside
http xxxxxxxxxxxxxx 255.255.255.0 inside
http xxxxxxxxxxxxxxxx 255.255.255.0 inside
http xxxxxxxxxxxxxxxxx 255.255.255.0 inside
http xxxxxxxxxxxx 255.255.255.0 inside
http xxxxxxxxxx 255.255.255.0 inside
http xxxxxxxxxxxx 255.255.255.255 inside
http xxxxxxxxxxxx 255.255.255.0 inside
http xxxxxxxxxxx 255.255.255.255 inside
snmp-server host inside xxxxxxxx community public
snmp-server host inside xxxxxxxxxxxxxx community public
snmp-server host inside xxxxxxxxx community public
snmp-server location Warsaw
snmp-server contact CSI
snmp-server community public
snmp-server enable traps snmp authentication linkup linkdown coldstart
snmp-server enable traps syslog
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto dynamic-map outside_dyn_map 65535 set transform-set ESP-3DES-SHA
crypto map outside_map 40 match address outside_40_cryptomap
crypto map outside_map 40 set pfs group5
crypto map outside_map 40 set peer xxxxxxxxxxx
crypto map outside_map 40 set transform-set ESP-AES-256-SHA
crypto map outside_map 60 match address outside_60_cryptomap
crypto map outside_map 60 set pfs
crypto map outside_map 60 set peer xxxxxxxxxxx
crypto map outside_map 60 set transform-set ESP-AES-128-SHA
crypto map outside_map 65535 ipsec-isakmp dynamic outside_dyn_map
crypto map outside_map interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
crypto isakmp policy 30
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 50
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
tunnel-group xxxxxxxxx type ipsec-l2l
tunnel-group xxxxxxxxx ipsec-attributes
pre-shared-key *
tunnel-group xxxxxxxxx type ipsec-l2l
tunnel-group xxxxxxxxx ipsec-attributes
pre-shared-key *
tunnel-group TEST type ipsec-ra
tunnel-group TEST general-attributes
address-pool ra-ip-pool-other-company
default-group-policy ra-gp-other-company
tunnel-group TEST ipsec-attributes
pre-shared-key *
telnet xxxxxxx 255.255.255.0 inside
telnet xxxxxxx 255.255.255.0 inside
telnet x 255.255.255.0 inside
telnet x 255.255.255.0 inside
telnet timeout 5
ssh xxxxxx 255.255.255.0 inside
ssh xxxxxx 255.255.255.0 inside
ssh xxxxx 255.255.255.0 inside
ssh xxxx 255.255.255.255 outside
ssh xxxxx 255.255.255.255 outside
ssh xxxxx 255.255.255.255 outside
ssh xxxxxxxxx 255.255.255.255 outside
ssh timeout 60
ssh version 2
console timeout 0
management-access inside
dhcpd auto_config outside
!
dhcpd address 192.168.48.2-192.168.48.225 inside
dhcpd dns 192.168.48.241 192.168.0.162 interface inside
!
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect icmp
!
service-policy global_policy global
ntp server 192.168.1.100 source inside prefer
prompt hostname context
Anyone help me ? Plase describe step by step how can i resolve the problem or debug.... Thanks !!
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2014 11:59 AM
Hi Bartlomiej,
I have some couple of questions for you.
- I don't see a route to your inside from your ASA, how is it connected?
- Do you have a switch behind the ASA that is doing routing between you vlans?
If yes you need to configure routing between both devices to talk to each other. See attached a drawing that would help 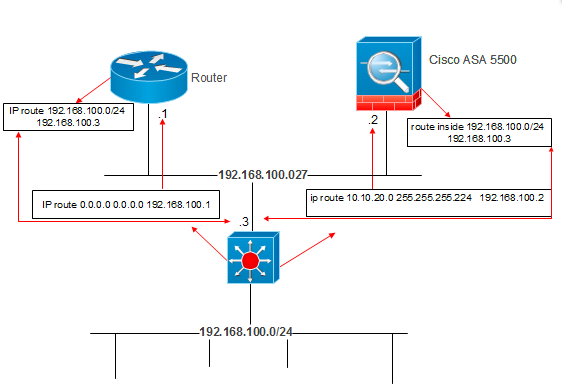
Pay attention to the Firewall and the switch, which i suppose that's how your network would look like.
I hope this helps.
Thanks
Teddy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2014 01:42 PM
That you can not ping the inside interface while having management-interface inside, and nat 0 configured almost screams a bug.
Try restarting the ASA first if that doesn't help then I suggest upgrading to a newer version.
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2014 04:25 AM
Hello Teddy && Marius
Few days ago ASA work properly and users which connected to ASA avia Cisco VPN Client have access to the LAN resources, but 2 days ago someone who have access to the ASA change my config... and he don't remember what he changed... I forgot save a config and copy to my hard drive
@Teddy: The answer on your questions is: My LAN network is directly connected via very very simple switch (it responsible only forward packet to the destination and it don't have any vlans - 2 layer), so behind the ASA is only switch which I describe you
@Marius: I remove "management-interface inside" but problem still exist. What do you mean that "nat 0 configured almost screams a bug" ? Nat configuration by my is incorrect ?
I tryed restarting the ASA but problem still exist....
I connected to ASA via CISCO VPN and tryed telnet to 3389 port to lan host - below is a result:
I also below attachment caputre and show crypto isakmp sa and show crypto ipsec sa - it looks that host from lan receive a packet and send back to asa but asa don't send to destination
#########ACL for capture ############
ciscoasa# show access-list | i cap
access-list cap-inside; 2 elements
access-list cap-inside line 1 extended permit ip host 192.168.120.1 192.168.48.0 255.255.255.0 (hitcnt=39) 0xb5705256
access-list cap-inside line 2 extended permit ip 192.168.48.0 255.255.255.0 host 192.168.120.1 (hitcnt=39) 0x42c6f92a
access-list cap-outside; 2 elements
access-list cap-outside line 1 extended permit ip host 212.91.x.x host 5.226.x.x (hitcnt=707) 0x383352c8
access-list cap-outside line 2 extended permit ip host 5.226.x.x host 212.91.x.x (hitcnt=271) 0x4ee286b0
ciscoasa# show capture
capture capout type raw-data access-list cap-outside interface outside circular-buffer [Capturing - 1231 bytes]
capture capin type raw-data access-list cap-inside interface inside circular-buffer [Capturing - 492 bytes]
ciscoasa# show capture capout
13 packets captured
1: 12:56:53.681895 802.1Q vlan#2 P0 212.91.x.x.10000 > 5.226.x.x.10000: udp 1
2: 12:56:55.742652 802.1Q vlan#2 P0 212.91.x.x.10000 > 5.226.x.x.10000: udp 84
3: 12:56:57.181142 802.1Q vlan#2 P0 212.91.x.x.4618 > 5.226.x.x.500: udp 84
4: 12:56:57.181966 802.1Q vlan#2 P0 5.226.x.x.500 > 212.91.x.x.4618: udp 84
5: 12:56:58.632505 802.1Q vlan#2 P0 212.91.x.x.10000 > 5.226.x.x.10000: udp 84
6: 12:57:03.682841 802.1Q vlan#2 P0 212.91.x.x.4618 > 5.226.x.x.500: udp 84
7: 12:57:04.647686 802.1Q vlan#2 P0 212.91.x.x.10000 > 5.226.x.x.10000: udp 84
8: 12:57:07.180364 802.1Q vlan#2 P0 212.91.x.x.4618 > 5.226.x.x.500: udp 84
9: 12:57:07.181142 802.1Q vlan#2 P0 5.226.x.x.500 > 212.91.x.x.4618: udp 84
10: 12:57:17.680461 802.1Q vlan#2 P0 212.91.x.x.4618 > 5.226.x.x.500: udp 84
11: 12:57:17.681391 802.1Q vlan#2 P0 5.226.x.x.500 > 212.91.x.x.4618: udp 84
12: 12:57:23.680644 802.1Q vlan#2 P0 212.91.x.x.4618 > 5.226.x.x.500: udp 84
13: 12:57:23.683131 802.1Q vlan#2 P0 212.91.x.x.10000 > 5.226.x.x.10000: udp 1
13 packets shown
ciscoasa# show capture capin
6 packets captured
1: 12:56:55.742973 802.1Q vlan#1 P0 192.168.120.1.4628 > 192.168.48.244.3389: S 3859705726:3859705726(0) win 65535
2: 12:56:55.743415 802.1Q vlan#1 P0 192.168.48.244.3389 > 192.168.120.1.4628: S 3741038123:3741038123(0) ack 3859705727 win 8192
3: 12:56:58.632581 802.1Q vlan#1 P0 192.168.120.1.4628 > 192.168.48.244.3389: S 3859705726:3859705726(0) win 65535
4: 12:56:58.750525 802.1Q vlan#1 P0 192.168.48.244.3389 > 192.168.120.1.4628: S 3741038123:3741038123(0) ack 3859705727 win 8192
5: 12:57:04.647763 802.1Q vlan#1 P0 192.168.120.1.4628 > 192.168.48.244.3389: S 3859705726:3859705726(0) win 65535
6: 12:57:04.756278 802.1Q vlan#1 P0 192.168.48.244.3389 > 192.168.120.1.4628: S 3741038123:3741038123(0) ack 3859705727 win 8192
6 packets shown
ciscoasa(config)# show route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 5.226.x.x to network 0.0.0.0
S 192.168.120.1 255.255.255.255 [1/0] via 5.226.x.x, outside
C 5.226.x.x 255.255.255.240 is directly connected, outside
C 127.1.0.0 255.255.0.0 is directly connected, _internal_loopback
C 192.168.48.0 255.255.255.0 is directly connected, inside
S* 0.0.0.0 0.0.0.0 [1/0] via 5.226.x.x, outside
ciscoasa(config)# show isakmp sa
Active SA: 2
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 2
1 IKE Peer: xxxxxxxxxx
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
2 IKE Peer: 212.91.x.x
Type : user Role : responder
Rekey : no State : AM_ACTIVE
Crypto map tag: outside_dyn_map, seq num: 65535, local addr: 5.226.x.x
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (192.168.120.1/255.255.255.255/0/0)
current_peer: 212.91.x.x, username: test
dynamic allocated peer ip: 192.168.120.1
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 6, #pkts decrypt: 6, #pkts verify: 6
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 5.226.x.x/10000, remote crypto endpt.: 212.91.x.x/10000
path mtu 1500, ipsec overhead 66, media mtu 1500
current outbound spi: 2DADBED0
inbound esp sas:
spi: 0x0F6EE710 (258926352)
transform: esp-3des esp-sha-hmac none
in use settings ={RA, Tunnel, UDP-Encaps, }
slot: 0, conn_id: 35, crypto-map: outside_dyn_map
sa timing: remaining key lifetime (sec): 27484
IV size: 8 bytes
replay detection support: Y
outbound esp sas:
spi: 0x2DADBED0 (766361296)
transform: esp-3des esp-sha-hmac none
in use settings ={RA, Tunnel, UDP-Encaps, }
slot: 0, conn_id: 35, crypto-map: outside_dyn_map
sa timing: remaining key lifetime (sec): 27484
IV size: 8 bytes
replay detection support: Y
And what's does mean:
Thanks for help !!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2014 08:28 AM
HI Bart,
I was just going via your configuration I need to understand why you have this ACL
access-list outside_access_in extended permit ip 192.168.0.0 255.255.0.0 any
access-list inside_nat0_outbound extended permit ip 192.168.48.0 255.255.255.0 192.168.0.0 255.255.0.0
How many users do you have in your network? Pretty sure it's not above 254 users.The 192.168.0.0 255.255.0.0 is a /16, which gives you about 65,534 hosts & 65,536 address and about 256 subnets. That's an overkill for a mid size network you are handling. If you really don't have much of need for the /16 ip address range! take it off and do your access list to specifics in your network. Basically you are sumarising and your ASA will have to go from 0 - 256 subnets to try find a match, which means your 192.168.48.0/24 & 192.168.195.0/28 in included! Hence more processing time and power for your ASA being used.
You already have specific ACLs
access-list inside_nat0_outbound extended permit 192.168.48.0 255.255.255.0 192.168.195.0 255.255.255.240
access-list inside_nat0_outbound extended permit 192.168.48.0 255.255.255.0 172.25.26.0 255.255.255.0
I will take off the below.
access-list inside_nat0_outbound extended permit ip 192.168.48.0 255.255.255.0 192.168.0.0 255.255.0.0
In my opinion that's opening a lot more than you can chew!
Can you share your "show access-list" lets see if you get hits whenever you connect and try getting access to your LAN.
Also from your discription above you probably would be using a generic switch that is not configurable am i right?
Thanks
Teddy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2014 11:22 AM
You must have managment-access inside configured to be able to ping the inside interface through a VPN tunnel.
What is this IP 192.168.120.1? You VPN pool is 192.168.195.x. It looks like your PC does not send using the correct IP. In any case had your PC sent using the correct IP you will never see those packets leave the outside interface since they are encrypted. So you can only rely on what you see coming in and out of the inside interface.
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2014 12:26 AM
Hi Teddy && Marius,
First of all I thank you very much for your interest,
Teddy:
access-list outside_access_in extended permit ip 192.168.0.0 255.255.0.0 any
access-list inside_nat0_outbound extended permit ip 192.168.48.0 255.255.255.0 192.168.0.0 255.255.0.0
This access-list responsible for a VPN Tunnel Site-to-site with Sweden..
access-list "outside_access_in" don't work for VPN because sysopt connection permit-vpn is enable
I agree with you that my Lan network have below 254 users and subnet 192.168.48.0/24 is my, but subnet 192.168.0.0/16 is subnet in Sweden and Technical from there want use this crypto domain.. I have no influence on it
Here you go my show access-list:ciscoasa(config)# show access-list
access-list cached ACL log flows: total 0, denied 0 (deny-flow-max 4096)
alert-interval 300
access-list inside_nat0_outbound; 4 elements
access-list inside_nat0_outbound line 1 extended permit ip 192.168.48.0 255.255.255.0 192.168.0.0 255.255.0.0 (hitcnt=0) 0x2ea627e1
access-list inside_nat0_outbound line 2 extended permit ip 192.168.48.0 255.255.255.0 172.25.26.0 255.255.255.0 (hitcnt=0) 0x3d0d3eb3
access-list inside_nat0_outbound line 3 extended permit ip 192.168.48.0 255.255.255.0 192.168.195.0 255.255.255.240 (hitcnt=0) 0xcb85cfcb
access-list inside_nat0_outbound line 4 extended permit ip 192.168.48.0 255.255.255.0 192.168.120.0 255.255.255.0 (hitcnt=0) 0xdd7efa20
access-list outside_access_in; 8 elements
access-list outside_access_in line 1 extended permit icmp any any echo-reply (hitcnt=29) 0x54b872f3
access-list outside_access_in line 2 extended permit ip 192.168.0.0 255.255.0.0 any (hitcnt=475613) 0x2db94844
access-list outside_access_in line 3 extended permit ip 172.25.26.0 255.255.255.0 any (hitcnt=18) 0x1f223ef3
access-list outside_access_in line 4 extended permit ip 192.168.195.0 255.255.255.240 any (hitcnt=0) 0xf90ebb53
access-list outside_access_in line 5 extended permit ip 192.168.120.0 255.255.255.0 any (hitcnt=0) 0xcbf5018
access-list outside_access_in line 6 extended permit ip host 212.91.x.x any (hitcnt=2) 0x797e7f5f
access-list outside_access_in line 7 extended permit tcp x host 192.168.48.244 eq 3389 (hitcnt=0) 0x6ffb62db
access-list outside_access_in line 8 extended permit tcp x host 5.226.x.x eq 3389 (hitcnt=6910) 0x76c1bfa1
access-list outside_40_cryptomap; 1 elements
access-list outside_40_cryptomap line 1 extended permit ip 192.168.48.0 255.255.255.0 192.168.0.0 255.255.0.0 (hitcnt=1484) 0x9d9b9a80
access-list outside_60_cryptomap; 1 elements
access-list outside_60_cryptomap line 1 extended permit ip 192.168.48.0 255.255.255.0 172.25.26.0 255.255.255.0 (hitcnt=29) 0x6e5c929f
access-list cap-inside; 2 elements
access-list cap-inside line 1 extended permit ip host 192.168.120.1 192.168.48.0 255.255.255.0 (hitcnt=42) 0xb5705256
access-list cap-inside line 2 extended permit ip 192.168.48.0 255.255.255.0 host 192.168.120.1 (hitcnt=42) 0x42c6f92a
access-list ra-split-other-company; 1 elements
access-list ra-split-other-company line 1 extended permit ip 192.168.48.0 255.255.255.0 any (hitcnt=0) 0x7e7ca319
access-list cap-outside; 2 elements
access-list cap-outside line 1 extended permit ip host 212.91.11.154 host 5.226.67.3 (hitcnt=1097) 0x383352c8
access-list cap-outside line 2 extended permit ip host 5.226.67.3 host 212.91.11.154 (hitcnt=419) 0x4ee286b0
Yes you are right I using a generic switch that is not configurable
@Marius
Ok, I add a management-access inside
192.168.120.1 is a IP address host which connect to ASA via Cisco VPN client, address 192.168.195.x. is a second adress VPN pool for other VPN Remote Access - sorry I explained it wrong
Correct is: 192.168.120.1 IP host which connect to ASA via Cisco VPN Client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2014 12:30 AM
192.168.120.1 IP host which connect to ASA via Cisco VPN Client
You do not have an address pool configured for this IP. Or is this part of a site to site VPN?
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2014 12:36 AM
The reason I ask is that when you say Cisco VPN Client that would refer to an IPsec remote access VPN
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2014 12:37 AM
ciscoasa# sh run | i local
ip local pool VPN_access 192.168.48.80-192.168.48.99 mask 255.255.255.0
ip local pool ra-ip-pool-other-company 192.168.195.1-192.168.195.14 mask 255.255.255.240
ip local pool ra-ip-pool-alan 192.168.120.1-192.168.120.254 mask 255.255.255.0
I have above ip pool for VPN Cisco Client, when I first add my config I omitted entries - sorrry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2014 12:39 AM
That is not shown in your original config post Only the ra-ip-pool-other-company is shown. could you post another full sanitised configuration please.
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2014 12:51 AM
ciscoasa(config)# ciscoasa(config)# ciscoasa(config)# ciscoasa(config)# sh run : Saved : ASA Version 7.2(2) ! hostname ciscoasa domain-name default.domain.invalid enable password xxxxxxxxxxxxxxxxx names ! interface Vlan1 nameif inside security-level 100 ip address 192.168.48.1 255.255.255.0 ospf cost 10 ! interface Vlan2 nameif outside security-level 0 ip address 5.226.x.x 255.255.255.240 ospf cost 10 ! interface Ethernet0/0 switchport access vlan 2 speed 100 duplex full ! interface Ethernet0/1 ! interface Ethernet0/2 ! interface Ethernet0/3 ! interface Ethernet0/4 ! interface Ethernet0/5 ! interface Ethernet0/6 ! interface Ethernet0/7 ! passwd 2KFQnbNIdI.2KYOU encrypted ftp mode passive clock timezone CEST 1 clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00 dns server-group DefaultDNS domain-name default.domain.invalid access-list inside_nat0_outbound extended permit ip 192.168.48.0 255.255.255.0 192.168.0.0 255.255.0.0 access-list inside_nat0_outbound extended permit ip 192.168.48.0 255.255.255.0 172.25.26.0 255.255.255.0 access-list inside_nat0_outbound extended permit ip 192.168.48.0 255.255.255.0 192.168.195.0 255.255.255.240 access-list inside_nat0_outbound extended permit ip 192.168.48.0 255.255.255.0 192.168.120.0 255.255.255.0 access-list outside_access_out remark infopraca deny access-list outside_access_out extended deny ip any host 194.116.240.115 access-list outside_access_out remark quantcast access-list outside_access_out extended deny ip any host 4.71.209.6 access-list outside_access_out remark imageshack access-list outside_access_out extended deny ip any host 38.99.77.81 access-list outside_access_out remark medforum access-list outside_access_out extended deny ip any host 62.75.153.150 access-list outside_access_out remark nokaut.pl access-list outside_access_out extended permit ip any host 62.129.241.235 access-list outside_access_out remark polska agencja rozwoju access-list outside_access_out extended deny ip any host 62.111.156.149 access-list outside_access_out remark ebay.pl access-list outside_access_out extended deny ip any host 66.135.200.23 access-list outside_access_out remark ebay access-list outside_access_out extended deny ip any host 66.135.200.27 access-list outside_access_out remark ebay2 access-list outside_access_out extended deny ip any host 66.135.205.13 access-list outside_access_out remark ebay access-list outside_access_out extended deny ip any host 66.135.205.14 access-list outside_access_out remark ebay access-list outside_access_out extended deny ip any host 66.135.221.10 access-list outside_access_out remark ebay access-list outside_access_out extended deny ip any host 66.135.221.11 access-list outside_access_out remark ebay access-list outside_access_out extended deny ip any host 66.135.221.12 access-list outside_access_out remark ebay access-list outside_access_out extended deny ip any host 66.211.160.87 access-list outside_access_out remark ebay access-list outside_access_out extended deny ip any host 66.211.160.88 access-list outside_access_out remark facebook.pl access-list outside_access_out extended deny ip any host 69.63.184.11 access-list outside_access_out remark Facebook access-list outside_access_out extended deny ip any host 69.63.186.12 access-list outside_access_out remark google video access-list outside_access_out extended deny ip any host 74.125.79.100 access-list outside_access_out remark google video access-list outside_access_out extended deny ip any host 74.125.79.113 access-list outside_access_out remark Ceneo access-list outside_access_out extended deny ip any host 81.201.117.40 access-list outside_access_out extended permit ip host 192.168.48.116 host 193.23.48.134 access-list outside_access_out remark Allegro access-list outside_access_out extended permit ip any host 193.23.48.134 access-list outside_access_out remark nasza-klasa access-list outside_access_out extended deny ip any 195.93.178.0 255.255.255.0 access-list outside_access_out remark nasza-klasa access-list outside_access_out extended deny ip any host 195.93.178.5 access-list outside_access_out remark Skapiec access-list outside_access_out extended deny ip any host 195.242.117.112 access-list outside_access_out remark youtoobe access-list outside_access_out extended deny ip any host 208.65.153.238 access-list outside_access_out remark youtube access-list outside_access_out extended deny ip any host 208.117.236.75 access-list outside_access_out remark pudelek.pl access-list outside_access_out extended deny ip any host 193.17.41.101 access-list outside_access_out remark poczta o2 access-list outside_access_out extended deny ip any host 193.17.41.103 access-list outside_access_out remark o2 poczta access-list outside_access_out extended deny ip any host 193.17.41.90 access-list outside_access_out remark wrzuta.pl access-list outside_access_out extended deny ip any host 193.17.41.95 access-list outside_access_out remark filmweb.pl access-list outside_access_out extended deny ip any host 193.200.227.13 access-list outside_access_out remark Page could not be checked access-list outside_access_out extended deny ip any host 216.8.177.26 access-list outside_access_out remark jobpilot.pl access-list outside_access_out extended deny ip any host 193.37.158.16 access-list outside_access_out remark iis access-list outside_access_out extended deny ip any host 194.0.171.80 access-list outside_access_out remark contium.pl access-list outside_access_out extended deny ip any host 194.0.211.130 access-list outside_access_out remark kulturystyka access-list outside_access_out extended deny ip any host 194.181.2.123 access-list outside_access_out remark orange.pl access-list outside_access_out extended deny ip any host 194.9.223.6 access-list outside_access_out remark polfa access-list outside_access_out extended deny ip any host 195.205.81.4 access-list outside_access_out remark lastfm access-list outside_access_out extended deny ip any host 195.24.233.55 access-list outside_access_out remark bbelements.com access-list outside_access_out extended deny ip any host 195.42.113.195 access-list outside_access_out remark msn.com access-list outside_access_out extended deny ip any host 207.46.216.54 access-list outside_access_out remark msn.com access-list outside_access_out extended deny ip any host 207.68.179.201 access-list outside_access_out remark youtube access-list outside_access_out extended deny ip any host 208.117.236.69 access-list outside_access_out remark youtube access-list outside_access_out extended deny ip any host 208.117.236.70 access-list outside_access_out remark youtube access-list outside_access_out extended deny ip any host 208.117.236.73 access-list outside_access_out remark youtube access-list outside_access_out extended deny ip any host 208.117.236.74 access-list outside_access_out remark youtube access-list outside_access_out extended deny ip any host 208.117.236.76 access-list outside_access_out remark youtube access-list outside_access_out extended deny ip any host 208.65.153.253 access-list outside_access_out remark photobucket access-list outside_access_out extended deny ip any host 209.17.65.10 access-list outside_access_out remark yahoo access-list outside_access_out extended deny ip any host 209.191.68.218 access-list outside_access_out remark yahoo access-list outside_access_out extended deny ip any host 209.191.93.51 access-list outside_access_out remark plus.pl access-list outside_access_out extended deny ip any host 212.2.119.234 access-list outside_access_out remark plus.pl access-list outside_access_out extended deny ip any host 212.2.96.49 access-list outside_access_out remark onetlajt access-list outside_access_out extended deny ip any host 212.244.48.59 access-list outside_access_out remark sedlak&sedlak access-list outside_access_out extended deny ip any host 212.85.121.191 access-list outside_access_out remark onet poczta access-list outside_access_out extended deny ip any host 213.180.138.16 access-list outside_access_out remark yahoo access-list outside_access_out extended deny ip any host 217.12.4.78 access-list outside_access_out remark yahoo access-list outside_access_out extended deny ip any host 217.12.8.76 access-list outside_access_out remark yahoo access-list outside_access_out extended deny ip any host 217.146.187.123 access-list outside_access_out remark yahoo access-list outside_access_out extended deny ip any host 217.146.187.164 access-list outside_access_out remark k2mail access-list outside_access_out extended deny ip any host 217.17.42.36 access-list outside_access_out remark tp access-list outside_access_out extended deny ip any host 217.97.216.17 access-list outside_access_out remark jobs.pl access-list outside_access_out extended deny ip any host 62.181.2.222 access-list outside_access_out remark AA pilots access-list outside_access_out extended deny ip any host 67.210.120.45 access-list outside_access_out remark yahoo access-list outside_access_out extended deny ip any host 68.142.230.52 access-list outside_access_out remark yahoo access-list outside_access_out extended deny ip any host 72.30.187.88 access-list outside_access_out remark gazeta.pl access-list outside_access_out extended deny ip any host 80.252.0.132 access-list outside_access_out remark szkola z klasa access-list outside_access_out extended deny ip any host 80.252.0.150 access-list outside_access_out remark gazeta.pl access-list outside_access_out extended deny ip any host 80.252.0.157 access-list outside_access_out remark aaaby.pl access-list outside_access_out extended deny ip any host 80.252.0.161 access-list outside_access_out remark wspolna access-list outside_access_out extended deny ip any host 80.55.34.50 access-list outside_access_out remark goldenline access-list outside_access_out extended deny ip any host 85.232.237.227 access-list outside_access_out remark goldenline access-list outside_access_out extended deny ip any host 85.232.237.228 access-list outside_access_out remark yahoo access-list outside_access_out extended deny ip any host 87.248.109.251 access-list outside_access_out remark yahoo access-list outside_access_out extended deny ip any host 87.248.113.14 access-list outside_access_out remark gwiazdor access-list outside_access_out extended deny ip any host 87.98.237.51 access-list outside_access_out remark lekolandia access-list outside_access_out extended deny ip any host 89.161.131.47 access-list outside_access_out remark szkolenia access-list outside_access_out extended deny ip any host 89.161.140.212 access-list outside_access_out remark ankietka.pl access-list outside_access_out extended deny ip any host 91.121.178.29 access-list outside_access_out remark Pracuj.pl access-list outside_access_out extended permit ip any host 193.200.67.10 access-list outside_access_out remark esklepy.pl access-list outside_access_out extended deny ip any host 91.121.22.204 access-list outside_access_out remark stylio.pl access-list outside_access_out extended deny ip any host 91.191.130.20 access-list outside_access_out remark mango.pl access-list outside_access_out extended deny ip any host 91.194.122.52 access-list outside_access_out remark businessclick access-list outside_access_out extended deny ip any host 92.43.114.125 access-list outside_access_out remark pracuj.pl access-list outside_access_out extended permit ip any host 193.200.66.201 access-list outside_access_out remark Cafe news access-list outside_access_out extended deny ip any host 91.102.117.236 access-list outside_access_out remark Amazon.com access-list outside_access_out extended deny ip any host 72.21.210.250 access-list outside_access_out remark Careersma access-list outside_access_out extended deny ip any host 12.216.63.108 access-list outside_access_out remark Carrefour Polmaraton access-list outside_access_out extended deny ip any host 77.55.35.128 access-list outside_access_out remark Commission Junction access-list outside_access_out extended deny ip any host 63.215.202.74 access-list outside_access_out remark Compendium access-list outside_access_out extended deny ip any host 212.160.237.14 access-list outside_access_out remark Daemon search access-list outside_access_out extended deny ip any host 219.254.32.133 access-list outside_access_out remark Daemon search access-list outside_access_out extended deny ip any host 78.129.142.67 access-list outside_access_out remark DIGI designs access-list outside_access_out extended deny ip any host 159.148.204.172 access-list outside_access_out remark DNE List access-list outside_access_out extended deny ip any host 207.250.205.34 access-list outside_access_out remark Dom zdrowia access-list outside_access_out extended deny ip any host 62.121.130.8 access-list outside_access_out remark Empik School access-list outside_access_out extended deny ip any host 217.153.177.165 access-list outside_access_out remark eTools access-list outside_access_out extended deny ip any host 194.150.96.11 access-list outside_access_out remark Faust multimedia access-list outside_access_out extended deny ip any host 213.198.89.191 access-list outside_access_out remark Fennema access-list outside_access_out extended deny ip any host 98.207.54.157 access-list outside_access_out remark Favore.pl access-list outside_access_out extended deny ip any host 90.156.61.8 access-list outside_access_out remark Cafe news access-list outside_access_out extended deny ip any host 91.197.14.140 access-list outside_access_out remark Go2.pl access-list outside_access_out extended deny ip any host 94.152.130.193 access-list outside_access_out remark Megatotal access-list outside_access_out extended deny ip any host 94.23.21.70 access-list outside_access_out extended deny ip any host 213.6.68.2 access-list outside_access_out remark TradeDoubler access-list outside_access_out extended deny ip any host 217.212.240.172 access-list outside_access_out remark Trade doubler access-list outside_access_out extended deny ip any host 217.212.244.231 access-list outside_access_out remark Facebook access-list outside_access_out extended deny ip any 69.63.0.0 255.255.0.0 access-list outside_access_out remark Facebook access-list outside_access_out extended deny ip any 66.220.0.0 255.255.0.0 access-list outside_access_out extended permit ip any any
access-list outside_access_in; 8 elements
access-list outside_access_in line 1 extended permit icmp any any echo-reply (hitcnt=29) 0x54b872f3
access-list outside_access_in line 2 extended permit ip 192.168.0.0 255.255.0.0 any (hitcnt=477891) 0x2db94844
access-list outside_access_in line 3 extended permit ip 172.25.26.0 255.255.255.0 any (hitcnt=18) 0x1f223ef3
access-list outside_access_in line 4 extended permit ip 192.168.195.0 255.255.255.240 any (hitcnt=0) 0xf90ebb53
access-list outside_access_in line 5 extended permit ip 192.168.120.0 255.255.255.0 any (hitcnt=0) 0xcbf5018
access-list outside_access_in line 6 extended permit ip host 212.91.x.x any (hitcnt=2) 0x797e7f5f
access-list outside_access_in line 7 extended permit tcp any host 192.168.48.244 eq 3389 (hitcnt=0) 0x6ffb62db
access-list outside_access_in line 8 extended permit tcp any host 5.226.x.x eq 3389 (hitcnt=6910) 0x76c1bfa1
access-list outside_40_cryptomap; 1 elements
access-list outside_40_cryptomap line 1 extended permit ip 192.168.48.0 255.255.255.0 192.168.0.0 255.255.0.0 (hitcnt=1484) 0x9d9b9a80
access-list WAR_remote_client_access_splitTunnelAcl; 1 elements
access-list WAR_remote_client_access_splitTunnelAcl line 1 standard permit any (hitcnt=0) 0x29952e7c
access-list outside_60_cryptomap; 1 elements
access-list outside_60_cryptomap line 1 extended permit ip 192.168.48.0 255.255.255.0 172.25.26.0 255.255.255.0 (hitcnt=29) 0x6e5c929f
access-list cap-inside; 2 elements
access-list cap-inside line 1 extended permit ip host 192.168.120.1 192.168.48.0 255.255.255.0 (hitcnt=42) 0xb5705256
access-list cap-inside line 2 extended permit ip 192.168.48.0 255.255.255.0 host 192.168.120.1 (hitcnt=42) 0x42c6f92a
access-list ra-split-other-company; 1 elements
access-list ra-split-other-company line 1 extended permit ip 192.168.48.0 255.255.255.0 any (hitcnt=0) 0x7e7ca319
access-list split-alan; 1 elements
access-list split-alan line 1 extended permit ip 192.168.48.0 255.255.255.0 any (hitcnt=0) 0xfce618f1
access-list cap-outside; 2 elements
access-list cap-outside line 1 extended permit ip host 212.91.11.154 host 5.226.67.3 (hitcnt=1097) 0x383352c8
access-list cap-outside line 2 extended permit ip host 5.226.67.3 host 212.91.11.154 (hitcnt=419) 0x4ee286b0
pager lines 24 logging enable logging timestamp logging buffer-size 65536 logging buffered warnings logging trap critical logging history notifications logging asdm informational logging facility 16 logging device-id hostname logging host inside 192.168.0.228 logging ftp-server 192.168.1.149 /joannap/ joannap **** logging permit-hostdown mtu inside 1500 mtu outside 1500 ip local pool VPN_access 192.168.48.80-192.168.48.99 mask 255.255.255.0 ip local pool ra-ip-pool-other-company 192.168.195.1-192.168.195.14 mask 255.255.255.240 ip local pool ra-ip-pool-alan 192.168.120.1-192.168.120.254 mask 255.255.255.0 icmp unreachable rate-limit 1 burst-size 1 icmp permit any inside icmp permit any outside asdm image disk0:/asdm-522.bin no asdm history enable arp timeout 14400 global (outside) 1 interface nat (inside) 0 access-list inside_nat0_outbound nat (inside) 1 0.0.0.0 0.0.0.0 static (inside,outside) tcp 5.226.x.x 3389 192.168.48.244 3389 netmask 255.255.255.255 access-group outside_access_in in interface outside access-group outside_access_out out interface outside route outside 0.0.0.0 0.0.0.0 5.226.x.x 1 timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout uauth 0:05:00 absolute group-policy ra-gp-alan internal group-policy ra-gp-alan attributes banner value xxxxxxxxmy! vpn-tunnel-protocol IPSec ipsec-udp enable split-tunnel-policy tunnelspecified split-tunnel-network-list value split-alan group-policy ra-gp-other-company internal group-policy ra-gp-other-company attributes banner value xxxxxxxy ! vpn-tunnel-protocol IPSec ipsec-udp enable split-tunnel-policy tunnelspecified split-tunnel-network-list value ra-split-other-company group-policy WAR_remote_client_access internal group-policy WAR_remote_client_access attributes banner value xxxxxxxxxxamy! dns-server value 192.168.48.241 192.168.0.162 vpn-tunnel-protocol IPSec split-tunnel-policy tunnelspecified split-tunnel-network-list value WAR_remote_client_access_splitTunnelAcl default-domain value cbg username alansystems password xxxxxxxxxxxxxxx encrypted privilege 0 username alansystems attributes vpn-group-policy ra-gp-other-company aaa authentication telnet console LOCAL aaa authentication ssh console LOCAL http server enable http 212.91.x.x 255.255.255.255 outside http 81.x.x.x 255.255.255.255 outside http 213.115.x.x 255.255.255.255 outside http 213.115.x.x 255.255.255.255 outside http 91.192.x.x 255.255.255.0 outside http 192.168.1.0 255.255.255.0 inside http 192.168.48.0 255.255.255.0 inside http 192.168.2.0 255.255.255.0 inside http 192.168.0.0 255.255.255.0 inside http 192.168.31.0 255.255.255.0 inside http 192.168.4.31 255.255.255.255 inside http 192.168.4.0 255.255.255.0 inside http 192.168.4.33 255.255.255.255 inside snmp-server host inside 192.168.0.110 community public snmp-server host inside 192.168.4.31 community public snmp-server host inside 192.168.48.243 community public snmp-server location Warsaw snmp-server contact CSI snmp-server community public snmp-server enable traps snmp authentication linkup linkdown coldstart snmp-server enable traps syslog crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac crypto dynamic-map outside_dyn_map 65535 set transform-set ESP-3DES-SHA crypto map outside_map 40 match address outside_40_cryptomap crypto map outside_map 40 set pfs group5 crypto map outside_map 40 set peer 91.192.x.x crypto map outside_map 40 set transform-set ESP-AES-256-SHA crypto map outside_map 60 match address outside_60_cryptomap crypto map outside_map 60 set pfs crypto map outside_map 60 set peer 81.210.x.x crypto map outside_map 60 set transform-set ESP-AES-128-SHA crypto map outside_map 65535 ipsec-isakmp dynamic outside_dyn_map crypto map outside_map interface outside crypto isakmp enable outside crypto isakmp policy 10 authentication pre-share encryption aes-256 hash sha group 5 lifetime 86400 crypto isakmp policy 30 authentication pre-share encryption 3des hash sha group 2 lifetime 86400 crypto isakmp policy 50 authentication pre-share encryption aes hash sha group 2 lifetime 86400 tunnel-group 91.192.x.x type ipsec-l2l tunnel-group 91.192.x.x ipsec-attributes pre-shared-key * tunnel-group WAR_remote_client_access type ipsec-ra tunnel-group WAR_remote_client_access general-attributes address-pool VPN_access default-group-policy WAR_remote_client_access tunnel-group WAR_remote_client_access ipsec-attributes pre-shared-key * tunnel-group 81.210.x.x type ipsec-l2l tunnel-group 81.210.x.x ipsec-attributes pre-shared-key * tunnel-group CBG-OTHER-COM type ipsec-ra tunnel-group CBG-OTHER-COM general-attributes address-pool ra-ip-pool-other-company default-group-policy ra-gp-other-company tunnel-group CBG-OTHER-COM ipsec-attributes pre-shared-key * tunnel-group ALANSYSTEM type ipsec-ra tunnel-group ALANSYSTEM general-attributes address-pool ra-ip-pool-alan default-group-policy ra-gp-alan tunnel-group ALANSYSTEM ipsec-attributes pre-shared-key * telnet 192.168.48.0 255.255.255.0 inside telnet 192.168.248.0 255.255.255.0 inside telnet 192.168.3.0 255.255.255.0 inside telnet 192.168.0.0 255.255.255.0 inside telnet timeout 5 ssh 192.168.3.0 255.255.255.0 inside ssh 192.168.0.0 255.255.255.0 inside ssh 192.168.248.0 255.255.255.0 inside ssh 91.192.x.x 255.255.255.255 outside ssh 77.72.x.x 255.255.255.255 outside ssh 212.91.x.x 255.255.255.255 outside ssh 81.210.x.x 255.255.255.255 outside ssh timeout 60 ssh version 2 console timeout 0 management-access inside dhcpd auto_config outside ! dhcpd address 192.168.48.2-192.168.48.225 inside dhcpd dns 192.168.48.241 192.168.0.162 interface inside ! ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum 512 policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect rsh inspect rtsp inspect esmtp inspect sqlnet inspect skinny inspect sunrpc inspect xdmcp inspect sip inspect netbios inspect tftp inspect icmp ! service-policy global_policy global ntp server 192.168.1.100 source inside prefer tftp-server outside 192.168.48.7 /WAWA-firewall-conf prompt hostname context Cryptochecksum:7daaa802fc6c8c17529df28654542292 : end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2014 01:22 AM
Your config looks fine with the exception of your split tunnel ACL. This should be a standard ACL and only defines the destination subnet.
access-list split-alan standard permit ip 192.168.48.0 255.255.255.0
Just noticed that your user is locked to group policy ra-split-other-company. this split tunnel configuration is also incorrect.
I would not think this would affect remote access connectivity, but please fix the split tunneling and test and get back to us.
Other than that, you configuration looks correct.
You might want to try removing the group policy configuration from the user attributes and test also. I have seen some cases where locking the user to a group caused connectivity issues.
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2014 05:22 AM
@Marius
Still don't work properly... I can't ping inside interface ASA...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2014 06:27 AM
Hi Bart,
Sorry I've been busy with some project, hence I couldn't respond to your previous replys.
Ok I heard what you had to say about the ACL.
did you enable RRI, RRI basically would inject IP pool into the ASA routing table, but in this case I don't know if it would be applicable since there's no other device behind the ASA that does routing. I guess it wouldn't hurt to enable it. something like this
crypto dynamic-map outside_dyn_map 65535 set reverse-route
Secondly can you do a packet-tracer from your outside to inside using your RA-IP-pool address, then copy and paste the outcome. Please edit it before pasting.
Thanks
Teddy
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

