- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 06:36 AM
Hello!
Configured the router as L2TP + IPSEK server. The client connects normally.
When connected, the local network is not available.
The debug sees the client traffic.
But client it fails to ping or connect to local resurs.
Can you suggest what is the problem?
Thank you.
Current configuration : 10558 bytes
!
! Last configuration change at 15:00:30 CET Thu Nov 10 2022 by softlist
! NVRAM config last updated at 15:00:23 CET Thu Nov 10 2022 by softlist
!
version 17.3
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
platform hardware throughput crypto 50000
!
hostname localHome
!
boot-start-marker
boot-end-marker
!
!
enable secret 9 xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
!
aaa new-model
!
!
aaa authentication login default local
aaa authentication ppp default local
aaa authorization network default local
!
!
!
!
!
!
aaa session-id common
clock timezone CET 1 0
clock summer-time CEST recurring last Sun Mar 2:00 last Sun Oct 3:00
!
!
!
!
!
!
!
ip name-server 8.8.8.8 8.8.4.4
ip domain name localhome.local
ip dhcp excluded-address 192.168.168.42
ip dhcp excluded-address 192.168.88.240 192.168.88.255
ip dhcp excluded-address 192.168.88.1 192.168.88.30
!
ip dhcp pool lanpool
network 192.168.88.0 255.255.255.0
default-router 192.168.88.1
dns-server 192.168.88.1
domain-name localhome.local
!
!
ip dhcp pool CP4
host 192.168.88.254 255.255.255.0
hardware-address 0000.dddd.ffff
!
ip dhcp pool CP5
host 192.168.88.255 255.255.255.0
hardware-address 0000.dddd.eeee
!
!
!
!
login on-success log
!
!
!
!
!
!
!
subscriber templating
!
!
!
!
!
multilink bundle-name authenticated
vpdn enable
!
vpdn-group g-l2tp
! Default L2TP VPDN group
accept-dialin
protocol l2tp
virtual-template 1
no l2tp tunnel authentication
!
no device-tracking logging theft
!
password encryption aes
!
!
crypto pki trustpoint TP-self-signed
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate
revocation-check none
rsakeypair TP-self-signed
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
!
!
no license feature hseck9
license udi pid C1121-4PLTEP
license boot level securityk9
memory free low-watermark processor 71820
!
diagnostic bootup level minimal
!
spanning-tree extend system-id
!
username admin privilege 15 secret 9 xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
username cisco privilege 15 secret 9 xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
username user password 7 xxxxxxxxxxxxxxxxxxxxxxxxxxx
username user1 password 7 xxxxxxxxxxxxxxxxxxxxxxxxxxx
username user2 password 7 xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
!
redundancy
mode none
!
!
!
!
controller Cellular 0/2/0
!
!
vlan internal allocation policy ascending
!
!
!
!
!
!
!
crypto isakmp policy 10
encryption 3des
authentication pre-share
group 2
lifetime 3600
crypto isakmp key superPassw0rd address 0.0.0.0 no-xauth
!
!
crypto ipsec transform-set l2tptset esp-3des esp-sha-hmac
mode transport
!
!
!
crypto dynamic-map l2tpmap 10
set nat demux
set transform-set l2tptset
!
!
crypto map l2tpmap 1 ipsec-isakmp dynamic l2tpmap
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0/0
description Internet ISP
ip address XX.XX.XX.15 255.255.255.128
ip nat outside
negotiation auto
crypto map l2tpmap
!
interface GigabitEthernet0/0/1
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/1/0
!
interface GigabitEthernet0/1/1
!
interface GigabitEthernet0/1/2
!
interface GigabitEthernet0/1/3
!
interface Cellular0/2/0
ip address negotiated
ipv6 enable
!
interface Cellular0/2/1
no ip address
shutdown
!
interface Virtual-Template1
ip unnumbered GigabitEthernet0/0/0
ip nat inside
peer default ip address pool l2tp-pool
no keepalive
ppp authentication ms-chap-v2
!
interface Vlan1
ip address 192.168.88.1 255.255.255.0
ip nat inside
!
ip local pool l2tp-pool 192.168.128.1 192.168.128.254
no ip http server
ip http authentication local
ip http secure-server
no ip forward-protocol nd
ip dns server
ip nat inside source static tcp 192.168.88.80 80 XX.XX.XX.15 80 extendable
ip nat inside source static tcp 192.168.88.80 443 XX.XX.XX.15 443 extendable
ip nat inside source list 10 interface GigabitEthernet0/0/0 overload
ip route 0.0.0.0 0.0.0.0 XX.XX.XX.1
ip ssh version 2
!
!
!
ip access-list standard 10
10 remark NAT
10 permit 192.168.88.0 0.0.0.255
20 permit 192.168.128.0 0.0.0.255
ip access-list standard 99
10 remark --- Managment Addresses ---
10 permit 192.168.88.0 0.0.0.255
20 permit 192.168.128.0 0.0.0.255
!
!
!
!
!
control-plane
!
!
line con 0
stopbits 1
line vty 0 4
access-class 99 in
exec-timeout 60 0
logging synchronous
transport input ssh
!
call-home
! If contact email address in call-home is configured as sch-smart-licensing@cisco.com
! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications.
contact-email-addr sch-smart-licensing@cisco.com
profile "CiscoTAC-1"
active
destination transport-method http
ntp server 0.pool.ntp.org
!
!
!
!
!
!
end
Client stat:
localHome#sh l2tp tunnel summary
L2TP Tunnel Information Total tunnels 1 sessions 1
LocTunID RemTunID Remote Name State Remote Address Sessn L2TP Class/
Count VPDN Group
16920 15 CLIENT1.Domain.local est YY.YY.YY.35 1 g-l2tp
localHome#sh l2tp tunnel all
L2TP Tunnel Information Total tunnels 1 sessions 1
Tunnel id 16920 is up, remote id is 15, 1 active sessions
Remotely initiated tunnel
Tunnel state is established, time since change 00:44:58
Tunnel transport is UDP (17)
Remote tunnel name is CLIENT1.Domain.local
Internet Address YY.YY.YY.35, port 64916
Local tunnel name is localHome
Internet Address XX.XX.XX.15, port 1701
L2TP class for tunnel is g-l2tp
Counters, taking last clear into account:
12 packets sent, 1012 received
253 bytes sent, 91229 received
Last clearing of counters never
Counters, ignoring last clear:
12 packets sent, 1012 received
253 bytes sent, 91229 received
Control Ns 2, Nr 69
Local RWS 1024 (default), Remote RWS 8
Control channel Congestion Control is disabled
Tunnel PMTU checking disabled
Retransmission time 1, max 1 seconds
Unsent queuesize 0, max 0
Resend queuesize 0, max 1
Total resends 1, ZLB ACKs sent 72
Total out-of-order dropped pkts 0
Total out-of-order reorder pkts 0
Total peer authentication failures 0
Current no session pak queue check 0 of 5
Retransmit time distribution: 0 1 0 0 0 0 0 0 0
Control message authentication is disabled
VPDN group for tunnel is g-l2tp
Debug
.Nov 11 13:51:22.115: IP: s=192.168.128.4 (Virtual-Access2.1), d=239.255.255.250 (nil), len 202, input feature
.Nov 11 13:51:22.116: UDP src=57430, dst=1900, packet consumed, MCI Check(110), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.178: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (nil), len 52, input feature
.Nov 11 13:51:22.178: TCP src=50709, dst=443, seq=1441650006, ack=0, win=65280 SYN, Virtual Fragment Reassembly(40), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.179: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (nil), len 52, input feature
.Nov 11 13:51:22.179: TCP src=50709, dst=443, seq=1441650006, ack=0, win=65280 SYN, iEdge(99), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.179: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (nil), len 52, input feature
.Nov 11 13:51:22.179: TCP src=50709, dst=443, seq=1441650006, ack=0, win=65280 SYN, MCI Check(110), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.179: FIBipv4-packet-proc: route packet from Virtual-Access2.1 src 192.168.128.4 dst 192.168.88.220
.Nov 11 13:51:22.179: FIBfwd-proc: packet routed by adj to Vlan1 192.168.88.220
.Nov 11 13:51:22.179: FIBipv4-packet-proc: packet routing succeeded
.Nov 11 13:51:22.179: IP: tableid=0, s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (Vlan1) nexthop=192.168.88.220, routed via FIB
.Nov 11 13:51:22.179: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (Vlan1), len 52, output feature
.Nov 11 13:51:22.179: TCP src=50709, dst=443, seq=1441650006, ack=0, win=65280 SYN, feature skipped, NAT Inside(8), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.180: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (Vlan1), g=192.168.88.220, len 52, forward
.Nov 11 13:51:22.180: TCP src=50709, dst=443, seq=1441650006, ack=0, win=65280 SYN
.Nov 11 13:51:22.180: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (nil), len 52, input feature
.Nov 11 13:51:22.180: TCP src=50708, dst=443, seq=2664650116, ack=0, win=65280 SYN, Virtual Fragment Reassembly(40), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.180: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (nil), len 52, input feature
.Nov 11 13:51:22.180: TCP src=50708, dst=443, seq=2664650116, ack=0, win=65280 SYN, iEdge(99), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.180: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (nil), len 52, input feature
.Nov 11 13:51:22.180: TCP src=50708, dst=443, seq=2664650116, ack=0, win=65280 SYN, MCI Check(110), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.181: FIBipv4-packet-proc: route packet from Virtual-Access2.1 src 192.168.128.4 dst 192.168.88.220
.Nov 11 13:51:22.181: FIBfwd-proc: packet routed by adj to Vlan1 192.168.88.220
.Nov 11 13:51:22.181: FIBipv4-packet-proc: packet routing succeeded
.Nov 11 13:51:22.181: IP: tableid=0, s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (Vlan1) nexthop=192.168.88.220, routed via FIB
.Nov 11 13:51:22.181: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (Vlan1), len 52, output feature
.Nov 11 13:51:22.181: TCP src=50708, dst=443, seq=2664650116, ack=0, win=65280 SYN, feature skipped, NAT Inside(8), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.181: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (Vlan1), g=192.168.88.220, len 52, forward
.Nov 11 13:51:22.181: TCP src=50708, dst=443, seq=2664650116, ack=0, win=65280 SYN
.Nov 11 13:51:22.434: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (nil), len 52, input feature
.Nov 11 13:51:22.434: TCP src=50710, dst=443, seq=3939493254, ack=0, win=65280 SYN, Virtual Fragment Reassembly(40), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.434: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (nil), len 52, input feature
.Nov 11 13:51:22.435: TCP src=50710, dst=443, seq=3939493254, ack=0, win=65280 SYN, iEdge(99), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.435: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (nil), len 52, input feature
.Nov 11 13:51:22.435: TCP src=50710, dst=443, seq=3939493254, ack=0, win=65280 SYN, MCI Check(110), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.435: FIBipv4-packet-proc: route packet from Virtual-Access2.1 src 192.168.128.4 dst 192.168.88.220
.Nov 11 13:51:22.435: FIBfwd-proc: packet routed by adj to Vlan1 192.168.88.220
.Nov 11 13:51:22.435: FIBipv4-packet-proc: packet routing succeeded
.Nov 11 13:51:22.435: IP: tableid=0, s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (Vlan1) nexthop=192.168.88.220, routed via FIB
.Nov 11 13:51:22.435: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (Vlan1), len 52, output feature
.Nov 11 13:51:22.435: TCP src=50710, dst=443, seq=3939493254, ack=0, win=65280 SYN, feature skipped, NAT Inside(8), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.435: IP: s=192.168.128.4 (Virtual-Access2.1), d=192.168.88.220 (Vlan1), g=192.168.88.220, len 52, forward
.Nov 11 13:51:22.436: TCP src=50710, dst=443, seq=3939493254, ack=0, win=65280 SYN
.Nov 11 13:51:22.459: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (nil), len 65, input feature
.Nov 11 13:51:22.459: UDP src=51647, dst=53, Virtual Fragment Reassembly(40), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.459: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (nil), len 65, input feature
.Nov 11 13:51:22.459: UDP src=51647, dst=53, iEdge(99), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.460: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (nil), len 65, input feature
.Nov 11 13:51:22.460: UDP src=51647, dst=53, MCI Check(110), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.460: FIBipv4-packet-proc: route packet from Virtual-Access2.1 src 192.168.128.4 dst 8.8.8.8
.Nov 11 13:51:22.460: FIBfwd-proc: packet routed by adj to GigabitEthernet0/0/0 XX.XX.XX.1
.Nov 11 13:51:22.460: FIBipv4-packet-proc: packet routing succeeded
.Nov 11 13:51:22.460: IP: tableid=0, s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0) nexthop=XX.XX.XX.1, routed via FIB
.Nov 11 13:51:22.460: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:22.460: UDP src=51647, dst=53, feature skipped, Post-routing NAT Outside(26), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.460: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:22.460: UDP src=51647, dst=53, feature skipped, IPSec output classification(36), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.460: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:22.460: UDP src=51647, dst=53, feature skipped, IPSec: to crypto engine(85), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.460: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:22.460: UDP src=51647, dst=53, feature skipped, Post-encryption output features(86), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.460: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), g=XX.XX.XX.1, len 65, forward
.Nov 11 13:51:22.461: UDP src=51647, dst=53
.Nov 11 13:51:22.461: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, pre-encap feature
.Nov 11 13:51:22.461: UDP src=51647, dst=53, feature skipped, IPSec Output Encap(1), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:22.461: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, pre-encap feature
localHome#
.Nov 11 13:51:22.461: UDP src=51647, dst=53, feature skipped, Crypto Engine(3), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.114: IP: s=192.168.128.4 (Virtual-Access2.1), d=239.255.255.250 (nil), len 202, input feature
.Nov 11 13:51:23.114: UDP src=57430, dst=1900, Virtual Fragment Reassembly(40), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.114: IP: s=192.168.128.4 (Virtual-Access2.1), d=239.255.255.250 (nil), len 202, input feature
.Nov 11 13:51:23.114: UDP src=57430, dst=1900, iEdge(99), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.114: FIBipv4-packet-proc: route packet from Virtual-Access2.1 src 192.168.128.4 dst 239.255.255.250
.Nov 11 13:51:23.114: FIBfwd-proc: Default:224.0.0.0/4 multicast entry
.Nov 11 13:51:23.114: FIBipv4-packet-proc: packet routing failed
.Nov 11 13:51:23.115: IP: s=192.168.128.4 (Virtual-Access2.1), d=239.255.255.250 (nil), len 202, input feature
.Nov 11 13:51:23.115: UDP src=57430, dst=1900, packet consumed, MCI Check(110), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.460: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (nil), len 65, input feature
.Nov 11 13:51:23.460: UDP src=51647, dst=53, Virtual Fragment Reassembly(40), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.460: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (nil), len 65, input feature
.Nov 11 13:51:23.460: UDP src=51647, dst=53, iEdge(99), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.460: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (nil), len 65, input feature
.Nov 11 13:51:23.460: UDP src=51647, dst=53, MCI Check(110), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.460: FIBipv4-packet-proc: route packet from Virtual-Access2.1 src 192.168.128.4 dst 8.8.4.4
.Nov 11 13:51:23.460: FIBfwd-proc: packet routed by adj to GigabitEthernet0/0/0 XX.XX.XX.1
.Nov 11 13:51:23.460: FIBipv4-packet-proc: packet routing succeeded
.Nov 11 13:51:23.460: IP: tableid=0, s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0) nexthop=XX.XX.XX.1, routed via FIB
.Nov 11 13:51:23.460: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:23.460: UDP src=51647, dst=53, feature skipped, Post-routing NAT Outside(26), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.460: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:23.461: UDP src=51647, dst=53, feature skipped, IPSec output classification(36), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.461: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:23.461: UDP src=51647, dst=53, feature skipped, IPSec: to crypto engine(85), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.461: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:23.461: UDP src=51647, dst=53, feature skipped, Post-encryption output features(86), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.461: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), g=XX.XX.XX.1, len 65, forward
.Nov 11 13:51:23.461: UDP src=51647, dst=53
.Nov 11 13:51:23.461: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, pre-encap feature
.Nov 11 13:51:23.461: UDP src=51647, dst=53, feature skipped, IPSec Output Encap(1), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.461: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, pre-encap feature
.Nov 11 13:51:23.461: UDP src=51647, dst=53, feature skipped, Crypto Engine(3), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:23.526: IP: Pre-routing: update nexthop: topoid: 0x0 s=XX.XX.XX.15(local), d=8.8.8.8, Intf: (GigabitEthernet0/0/0), Found gw: XX.XX.XX.1
.Nov 11 13:51:23.527: IP: Pre-routing: update nexthop: topoid: 0x0 s=XX.XX.XX.15(local), d=8.8.8.8, Intf: (GigabitEthernet0/0/0), Found gw: XX.XX.XX.1
.Nov 11 13:51:23.544: IP: Pre-routing: update nexthop: topoid: 0x0 s=XX.XX.XX.15(local), d=8.8.8.8, Intf: (GigabitEthernet0/0/0), Found gw: XX.XX.XX.1
.Nov 11 13:51:23.556: IP: Pre-routing: update nexthop: topoid: 0x0 s=XX.XX.XX.15(local), d=8.8.8.8, Intf: (GigabitEthernet0/0/0), Found gw: XX.XX.XX.1
.Nov 11 13:51:23.561: IP: Pre-routing: update nexthop: topoid: 0x0 s=XX.XX.XX.15(local), d=8.8.8.8, Intf: (GigabitEthernet0/0/0), Found gw: XX.XX.XX.1
.Nov 11 13:51:23.573: IP: Pre-routing: update nexthop: topoid: 0x0 s=XX.XX.XX.15(local), d=8.8.8.8, Intf: (GigabitEthernet0/0/0), Found gw: XX.XX.XX.1
.Nov 11 13:51:23.629: IP: Pre-routing: update nexthop: topoid: 0x0 s=XX.XX.XX.15(local), d=8.8.8.8, Intf: (GigabitEthernet0/0/0), Found gw: XX.XX.XX.1
.Nov 11 13:51:23.646: IP: Pre-routing: update nexthop: topoid: 0x0 s=XX.XX.XX.15(local), d=8.8.8.8, Intf: (GigabitEthernet0/0/0), Found gw: XX.XX.XX.1
.Nov 11 13:51:23.689: IP: Pre-routing: update nexthop: topoid: 0x0 s=192.168.88.1(local), d=192.168.88.55, Intf: (Vlan1), Found gw: 0.0.0.0
.Nov 11 13:51:23.690: IP: Pre-routing: update nexthop: topoid: 0x0 s=XX.XX.XX.15(local), d=8.8.8.8, Intf: (GigabitEthernet0/0/0), Found gw: XX.XX.XX.1
.Nov 11 13:51:23.730: IP: Pre-routing: update nexthop: topoid: 0x0 s=XX.XX.XX.15(local), d=8.8.8.8, Intf: (GigabitEthernet0/0/0), Found gw: XX.XX.XX.1
localHome#
.Nov 11 13:51:23.747: IP: Pre-routing: update nexthop: topoid: 0x0 s=192.168.88.1(local), d=192.168.88.55, Intf: (Vlan1), Found gw: 0.0.0.0
.Nov 11 13:51:23.754: IP: Pre-routing: update nexthop: topoid: 0x0 s=192.168.88.1(local), d=192.168.88.55, Intf: (Vlan1), Found gw: 0.0.0.0
localHome#
.Nov 11 13:51:25.461: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (nil), len 65, input feature
.Nov 11 13:51:25.462: UDP src=51647, dst=53, Virtual Fragment Reassembly(40), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.462: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (nil), len 65, input feature
.Nov 11 13:51:25.462: UDP src=51647, dst=53, iEdge(99), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.462: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (nil), len 65, input feature
.Nov 11 13:51:25.462: UDP src=51647, dst=53, MCI Check(110), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.462: FIBipv4-packet-proc: route packet from Virtual-Access2.1 src 192.168.128.4 dst 8.8.8.8
.Nov 11 13:51:25.462: FIBfwd-proc: packet routed by adj to GigabitEthernet0/0/0 XX.XX.XX.1
.Nov 11 13:51:25.462: FIBipv4-packet-proc: packet routing succeeded
.Nov 11 13:51:25.462: IP: tableid=0, s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0) nexthop=XX.XX.XX.1, routed via FIB
.Nov 11 13:51:25.462: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:25.463: UDP src=51647, dst=53, feature skipped, Post-routing NAT Outside(26), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.463: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:25.463: UDP src=51647, dst=53, feature skipped, IPSec output classification(36), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.463: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:25.463: UDP src=51647, dst=53, feature skipped, IPSec: to crypto engine(85), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.463: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:25.463: UDP src=51647, dst=53, feature skipped, Post-encryption output features(86), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.463: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), g=XX.XX.XX.1, len 65, forward
.Nov 11 13:51:25.463: UDP src=51647, dst=53
.Nov 11 13:51:25.463: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, pre-encap feature
.Nov 11 13:51:25.463: UDP src=51647, dst=53, feature skipped, IPSec Output Encap(1), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.463: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (GigabitEthernet0/0/0), len 65, pre-encap feature
.Nov 11 13:51:25.464: UDP src=51647, dst=53, feature skipped, Crypto Engine(3), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.464: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (nil), len 65, input feature
.Nov 11 13:51:25.464: UDP src=51647, dst=53, Virtual Fragment Reassembly(40), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.464: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (nil), len 65, input feature
.Nov 11 13:51:25.464: UDP src=51647, dst=53, iEdge(99), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.464: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (nil), len 65, input feature
.Nov 11 13:51:25.464: UDP src=51647, dst=53, MCI Check(110), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.464: FIBipv4-packet-proc: route packet from Virtual-Access2.1 src 192.168.128.4 dst 8.8.4.4
.Nov 11 13:51:25.464: FIBfwd-proc: packet routed by adj to GigabitEthernet0/0/0 XX.XX.XX.1
.Nov 11 13:51:25.464: FIBipv4-packet-proc: packet routing succeeded
.Nov 11 13:51:25.465: IP: tableid=0, s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0) nexthop=XX.XX.XX.1, routed via FIB
.Nov 11 13:51:25.465: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:25.465: UDP src=51647, dst=53, feature skipped, Post-routing NAT Outside(26), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.465: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:25.465: UDP src=51647, dst=53, feature skipped, IPSec output classification(36), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.465: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:25.465: UDP src=51647, dst=53, feature skipped, IPSec: to crypto engine(85), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.465: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, output feature
.Nov 11 13:51:25.465: UDP src=51647, dst=53, feature skipped, Post-encryption output features(86), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.465: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), g=XX.XX.XX.1, len 65, forward
.Nov 11 13:51:25.465: UDP src=51647, dst=53
.Nov 11 13:51:25.465: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, pre-encap feature
.Nov 11 13:51:25.466: UDP src=51647, dst=53, feature skipped, IPSec Output Encap(1), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.466: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.4.4 (GigabitEthernet0/0/0), len 65, pre-encap feature
.Nov 11 13:51:25.466: UDP src=51647, dst=53, feature skipped, Crypto Engine(3), rtype 1, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.805: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (nil), len 66, input feature
.Nov 11 13:51:25.805: UDP src=57429, dst=53, Virtual Fragment Reassembly(40), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.805: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (nil), len 66, input feature
.Nov 11 13:51:25.805: UDP src=57429, dst=53, iEdge(99), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.805: IP: s=192.168.128.4 (Virtual-Access2.1), d=8.8.8.8 (nil), len 66, input feature
.Nov 11 13:51:25.805: UDP src=57429, dst=53, MCI Check(110), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
.Nov 11 13:51:25.806: FIBipv4-packet-proc: route packet from Virtual-Access2.1 src 192.168.128.4 dst 8.8.8.8
.Nov 11 13:51:25.806: FIBfwd-proc: packet routed by adj to GigabitEthernet0/0/0 XX.XX.XX.1
.Nov 11 13:51:25.806: FIBipv4-packet-proc: packet routing succeeded
Solved! Go to Solution.
- Labels:
-
IPSEC
-
Remote Access
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2022 02:03 PM
Thank you for your responses!
This is not NAT.
I found a description of a similar problem on another forum.
For the solution, it says that you need to add a license:
license boot level appxk9
After adding and rebooting the router, the VPN worked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 07:47 AM
@DmitrySoftlist the traffic between the VPN clients and the local networks maybe unintentially translated by your NAT rules. Recreate the NAT ACL as an extended ACL, deny traffic between your local network and VPN client network, then permit the rest of the traffic. This should ensure the traffic between the local and VPN client network is not NATTED.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 09:38 AM
Thanks for the reply, @Rob Ingram
But unfortunately it didn't help.
I first tried adding an extended access-list and when that didn't work I try removed all NAT rules.
Traffic is still not moving properly.
Also I didn't find NAT between internal networks in the output:
#sh ip nat translations
ip access-list extended NAT
10 deny ip 192.168.88.0 0.0.0.255 192.168.128.0 0.0.0.255
20 deny ip 192.168.128.0 0.0.0.255 192.168.88.0 0.0.0.255
30 deny icmp 192.168.128.0 0.0.0.255 192.168.88.0 0.0.0.255
40 deny icmp 192.168.88.0 0.0.0.255 192.168.128.0 0.0.0.255
50 permit icmp 192.168.88.0 0.0.0.255 any
60 permit icmp 192.168.128.0 0.0.0.255 any
70 permit ip 192.168.128.0 0.0.0.255 any
80 permit ip 192.168.88.0 0.0.0.255 any
localHome(config)#no ip nat inside source list 10 interface GigabitEthernet0/0/0 overload
%Dynamic mapping in use, cannot remove
localHome(config)#do clear ip nat translation forced
localHome(config)#no ip nat inside source list 10 interface GigabitEthernet0/0/0 overload
localHome(config)#ip nat inside source list NAT interface GigabitEthernet0/0/0 overload
localHome(config)#
localHome(config)#
localHome(config)#do clear ip nat translation forced
localHome(config)#no ip nat inside source list NAT interface GigabitEthernet0/0/0 overload
localHome(config)#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2022 03:00 AM
friend I see many issue like this and finally I find one hint how we can solve issue,
NAT depend on interface which is INISDE and OOUTSIDE but the virtual-template is from it name it virtual no real interface so NAT not work!!
how we can solve this issue ?
I suggest remove the IP NAT inside from virtual-template and add it to LOOPBACK interface you use it IP for virtual-template.
hope this solve your issue
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2022 08:07 AM - edited 11-12-2022 08:12 AM
Hello!
Thanks for your answer!
But it didn't work.
I change config to:
interface Loopback1
description --- l2tp vpn endpoint ---
ip address 192.168.128.1 255.255.255.0
ip nat inside
!
interface Virtual-Template1
ip unnumbered Loopback1
peer default ip address pool l2tp-pool
ppp authentication ms-chap-v2
!
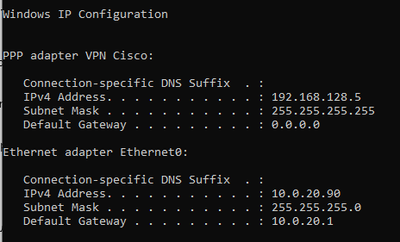
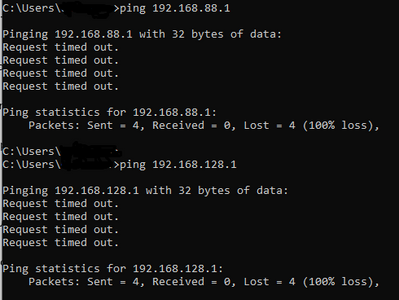
On the Windows client all looks good:
But no traffic:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2022 07:07 AM
debug ip nat <<- share the output of this debug when you ping
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2022 02:03 PM
Thank you for your responses!
This is not NAT.
I found a description of a similar problem on another forum.
For the solution, it says that you need to add a license:
license boot level appxk9
After adding and rebooting the router, the VPN worked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2022 07:44 PM
Thanks for sharing solution
Thanks a lot