- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Customizing AnyConnect MFA Prompts with DUO
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2021 08:14 AM
Hey all,
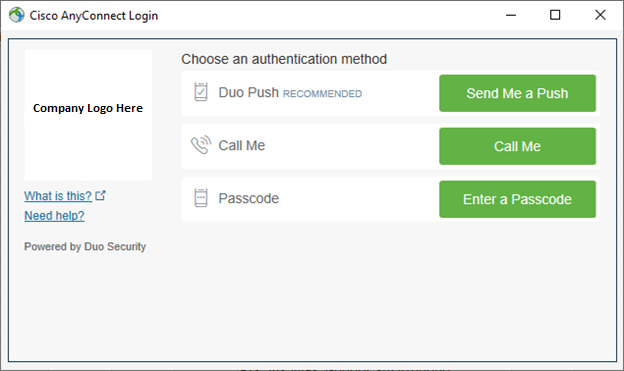
We have our Duo MFA setup with our Cisco ASA/Anyconnect in our environment. Up to this point, we've had all our users utilize the Duo App for push notifications, but recently we've had some users request pretty adamantly that they'd prefer to do text message notifications instead. In looking at our configuration options, it looks like we can setup AnyConnect with a "Second Password" field that the user can then enter either "push" (to receive a push notification) or "sms" (to receive a text message) [amongst other options]. The problem we're seeing is that when they enter "sms", the login screen essentially "resets", where the user has to enter their username/password and then in the "Second Password" field they THEN enter the code they received in the SMS text message.
We've spent some time tweaking the verbiage that we use in the little "administrative text box" that you can customize that sits just below the "Second Password" field to try and explain to our end users exactly what they're supposed to do here, but unfortunately not all of our users are very technical (read: *sometimes they have to be reminded where the Start button is in Windows*) -- so getting them to understand the process here has put kind of a burden on our HelpDesk support team.
My question is -- is there a way to make this less.....clunky? My ideal setup would be:
1.) User opens AnyConnect and selects the "vpn.mycompany.com" and hits "Connect"
2.) User is prompted for:
- Username [text input]
- Password [text input]
- **DROPDOWN** for how they want to receive their code/notification (with the option to save this preference, ideally)
3.) User clicks "OK" and either a push notification or SMS are sent
4.) If user selected SMS, a *new*, small prompt window opens asking for the code sent via text message.
5.) User enters SMS code and clicks "OK" and is allowed onto the network
Anything we can do on our end to make the experience more like this?
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Duo
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2021 10:41 AM
First, I just wanted to make sure you were aware that the use of SMS uses telephony credits on Duo. You will have to purchase additional credits as your users use them up so you will be incurring additional charges with this deployment.
Secondly, push notifications are more secure than SMS. NIST SP 800-63 states not to use SMS-based MFA because it's too easy to compromise by an attacker.
As for the ease of use for your end users: I'm assuming your are using the Duo Authenticating Proxy for this deployment. You might consider the Duo Access Gateway which will give users the ability to choose what method they want to use for their secondary authentication (check out the attached PowerPoint presentation for the full breakdown of the user experience. It uses animations).
In my experience, the Duo Access Gateway is much cleaner and provides more options for enrolling new users but it requires SAML. If you're using Firepower, you'll need to be at least on version 6.7
I know this hasn't been a direct answer to your question but does this help at all?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2021 10:41 AM
First, I just wanted to make sure you were aware that the use of SMS uses telephony credits on Duo. You will have to purchase additional credits as your users use them up so you will be incurring additional charges with this deployment.
Secondly, push notifications are more secure than SMS. NIST SP 800-63 states not to use SMS-based MFA because it's too easy to compromise by an attacker.
As for the ease of use for your end users: I'm assuming your are using the Duo Authenticating Proxy for this deployment. You might consider the Duo Access Gateway which will give users the ability to choose what method they want to use for their secondary authentication (check out the attached PowerPoint presentation for the full breakdown of the user experience. It uses animations).
In my experience, the Duo Access Gateway is much cleaner and provides more options for enrolling new users but it requires SAML. If you're using Firepower, you'll need to be at least on version 6.7
I know this hasn't been a direct answer to your question but does this help at all?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2021 01:16 PM
Thanks Tyson,
Yeah I was hoping we wouldn't have to change things up too much and there was some simple setting I was just missing in my AnyConnect GUI config, but ultimately we're going to go the DAG route. I appreciate the help!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide