- Cisco Community
- Technology and Support
- Security
- VPN
- Re: DAP Policy not matching Multiple Cert authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
DAP Policy not matching Multiple Cert authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2019 10:44 PM - edited 02-21-2020 09:40 PM
Hi all
I was wondering if someone would be able to help or advise if their are any additional requirements needed to get DAP to match a endpoint attribute relating to Multiple Certificates. I'm currently testing a solution for dap to check machine certificates and confirm that it is signed by our CA before approving access to the network.
From the ASA DAP_Trace debug output i can see the certificate being detected
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.certificate.user["7"].issuer_fulldn="C=##, O=##, OU=, CN=##"
DAP_TRACE: endpoint.certificate.user["7"].issuer_fulldn = ""
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.certificate.user["7"].issuer_cn="Network Devices CA V3"
DAP_TRACE: endpoint.certificate.user["7"].issuer_cn = "Network Devices CA V3"
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.certificate.user["7"].issuer_ou="9.9.9.9.9.9.9"
DAP_TRACE: endpoint.certificate.user["7"].issuer_ou = "9.9.9.9.9.9.9"
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.certificate.user["7"].issuer_o="Networks"
DAP_TRACE: endpoint.certificate.user["7"].issuer_o = "Networks"
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.certificate.user["7"].issuer_c="##"
DAP_TRACE: endpoint.certificate.user["7"].issuer_c = "##"
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.certificate.user["7"].version="V3"
DAP_TRACE: endpoint.certificate.user["7"].version = "V3"
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.certificate.user["7"].serial="#############################"
DAP_TRACE: endpoint.certificate.user["7"].serial = "#############################"
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.certificate.user["7"].time_valid_from="1528934442"
DAP_TRACE: endpoint.certificate.user["7"].time_valid_from = "1528934442"
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.certificate.user["7"].time_valid_to="1592006442"
DAP_TRACE: endpoint.certificate.user["7"].time_valid_to = "1592006442"
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.certificate.user["7"].sha1_hash="#########################"
DAP_TRACE: endpoint.certificate.user["7"].sha1_hash = "#########################"
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.certificate.user["7"].md5_hash="#########################"
DAP_TRACE: endpoint.certificate.user["7"].md5_hash = "#########################"
DAP_TRACE[128]: dap_install_endpoint_data_to_lua:endpoint.device.id="5CG7480GCP"
DAP_TRACE: endpoint.device.id = "5CG7480GCP"
However the result will always match the default catch all DAP created at the bottom of the ACL
DAP_TRACE: endpoint.anyconnect.macaddress["0"] = "44-03-bb-bb-bb-bb"
DAP_TRACE: Username: Blogs Joe, Selected DAPs: ,Default catch all
DAP_TRACE: dap_process_selected_daps: selected 1 records
DAP_TRACE: Username: Blogs Joe, dap_aggregate_attr: rec_count = 1
DAP_TRACE: Username: Blogs Joe, dap_concat_fcn: [Default Catch all] 17 490
DAP_TRACE: Username: Blogs Joe, DAP_close: 8F
DAP_TRACE: DAP_open: New DAP Request: C7
DAP_TRACE: DAP_add_CSD: csd_token = [732FA45E5613C99909E6A2E0]
The current basic DAP policy i have is
dynamic-access-policy-record "Default Catch all"
dynamic-access-policy-record DfltAccessPolicy
dynamic-access-policy-record "Certificate Check2"
user-message "Certificate Check"
priority 2
dynamic-access-policy-record "Certificate Check"
user-message "Certificate Issuer"
priority 1
Above i have created a number of policies for DAP to match the issuer CN on the certificate but it doesn't seem to be doing that, anyone advice would be greatly appreciated.
HW: ASA5545 Version: 9.8.2.38
- Labels:
-
AnyConnect
-
Other VPN Topics
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2019 10:58 PM
hi ,
Multiple certificate check has been introduced with hostscan4.6 and can be used only when AnyConnect MCA is used.
Or you can go for certificate check with LUA scripts
Thanks
Shakti
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2019 10:21 PM
When you say only when Anconnect MCA is used you mean only when you have MCA set as an authentication method?
I am currently trying to setup 2FA as authentication and use hostscan Machine certificate for DAP after client has been authenticated.
Regards
Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2020 07:58 AM
I am using hostscan for domain machines checking, but same time I also want to check the machine cert issued by AD to the client.
1 ) for the SSL VPN connection on the outside interface, I am using a global signed certificate.
2) Domain machines are using internally signed certificates.
Clients are using "Cisco AnyConnect Secure Mobility Client, Version 4.8.01090" and on the firewall using the host scan image "hostscan_4.8.01090-k9.pkg" with ASA image of "9.8(4)15"
I want to check the user is using Domain client machine, I can check with the hostscan registry scan to confirm that the machine is a member of the domain, but at the same time, I also want to check the Machine cert which is normally an internally signed cert and issue from AD.
Please advise what else is needed ! or any implementation guide?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2019 06:30 AM
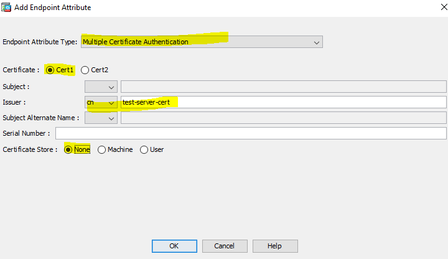
Please run "debug menu dap 2" from the CLI on you ASA to see the DAP policies create. To match the certificate in the machine store the DAP policy should look somethign like this. CN=test-server-cert
((EVAL(endpoint.cert[1].issuer.cn,"EQ","test-server-cert","string")))
ASDM screenshot
cert[1] is the machine certificate and is sent first during Multi cert Authentication(MCA)
Are you sure you are running code that supports MCA on both the ASA/Hostscan and AnyConnect?
The corrosponding DAP trace looks like this. Note the store ="machine" and the attribute is "endpoint.cert[1]". Your trace is showing as "endpoint.certificate.user" so I don't think you are performing MCA.
DAP_TRACE[128]: dap_add_to_lua_tree:endpoint.cert[1].store="machine"
DAP_TRACE: endpoint.cert[1].store = "machine"
DAP_TRACE: Username: Users, Added Certificate attribute endpoint.cert[1].store = "machine"
DAP_TRACE[128]: dap_add_to_lua_tree:endpoint.cert[1].subject.fulldn="cn=machine-name"
DAP_TRACE: endpoint.cert[1].subject.fulldn = "cn=machine-name"
DAP_TRACE: Username: Users, Added Certificate attribute endpoint.cert[1].subject.fulldn = "cn=machine-name"
DAP_TRACE[128]: dap_add_to_lua_tree:endpoint.cert[1].subject.cn[0]="machine-name"
DAP_TRACE: endpoint.cert[1].subject.cn[0] = "machine-name"
DAP_TRACE: Username: Users, Added Certificate attribute endpoint.cert[1].subject.cn[0] = "machine-name"
DAP_TRACE[128]: dap_add_to_lua_tree:endpoint.cert[1].subjectaltname.upn="machine-name@test.cisco.com"
DAP_TRACE: endpoint.cert[1].subjectaltname.upn = "machine-name@test.cisco.com"
DAP_TRACE: Username: Users, Added Certificate attribute endpoint.cert[1].subjectaltname.upn = "machine-name@test.cisco.com"
DAP_TRACE[128]: dap_add_to_lua_tree:endpoint.cert[1].serialnumber="6900000059CED7D70032BC5D42000000000059"
DAP_TRACE: endpoint.cert[1].serialnumber = "6900000059CED7D70032BC5D42000000000059"
DAP_TRACE: Username: Users, Added Certificate attribute endpoint.cert[1].serialnumber = "6900000059CED7D70032BC5D42000000000059"
DAP_TRACE[128]: dap_add_to_lua_tree:endpoint.cert[1].issuer.fulldn="cn=test-server-certtest-server-cert,dc=test,dc=cisco,dc=com"
DAP_TRACE: endpoint.cert[1].issuer.fulldn = "cn=test-server-cert,dc=test,dc=cisco,dc=com"
DAP_TRACE: Username: Users, Added Certificate attribute endpoint.cert[1].issuer.fulldn = "cn=test-server-cert,dc=test,dc=cisco,dc=com"
DAP_TRACE[128]: dap_add_to_lua_tree:endpoint.cert[1].issuer.cn[0]="test-server-cert"
DAP_TRACE: endpoint.cert[1].issuer.cn[0] = "test-server-cert"
DAP_TRACE: Username: Users, Added Certificate attribute endpoint.cert[1].issuer.cn[0] = "test-server-cert"
Hope this helps
Steve S.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide