- Cisco Community
- Technology and Support
- Security
- VPN
- I think in this case then
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Disable Split Tunnel surf via internal network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2016 03:14 AM
Hi
I have setup a VPN in our Cisco Firewall with Split Tunneling but i would like to be able to create a VPN which can use our internal gateway to surf via our internal network for IP blocking problems with some customers.
Would appreciate all help here is the config
: Saved
:
ASA Version 8.2(5)
!
hostname comodo
domain-name comodo.local
names
name 192.78.250.210 DNS-Extern
name 19.4.41.12 DNS-Intern
name 192.78.250.211 Devel-Extern
name 192.78.250.212 Time-Extern
name 192.78.250.214 Fw-Extern
name 192.78.250.213 Mail-Extern
name 19.4.41.220 Devel-Intern
name 19.4.41.9 Mail-Intern
name 19.4.41.8 Time-Intern
name 19.4.41.1 Fw-Intern
name 192.99.23.26 mailfilter.itsnordic.se
name 192.45.120.10 mailfilter2.itsnordic.se
name 192.78.250.209 ownit-route description default
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
switchport access vlan 5
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address Fw-Intern 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address Fw-Extern 255.255.255.248
!
ftp mode passive
clock timezone CEST 1
clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00
dns server-group DefaultDNS
domain-name comodo.local
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object-group service comodo tcp
port-object eq 21212
object-group service comodo-Webclient tcp
port-object eq 843
port-object eq 8787
object-group network DM_INLINE_NETWORK_1
network-object host mailfilter2.itsnordic.se
network-object host mailfilter.itsnordic.se
object-group service DM_INLINE_TCP_1 tcp
group-object comodo
group-object comodo-Webclient
port-object eq www
port-object eq https
object-group service DM_INLINE_SERVICE_1
service-object tcp-udp eq domain
service-object tcp eq www
service-object tcp eq https
object-group service Forward-SSH tcp
port-object eq 20022
object-group service DM_INLINE_TCP_2 tcp
group-object comodo-Webclient
port-object eq ftp
port-object eq www
port-object eq https
port-object eq ssh
group-object Forward-SSH
object-group service DM_INLINE_TCP_3 tcp
port-object eq www
port-object eq https
port-object eq smtp
port-object eq imap4
port-object eq pop3
object-group service IPSEC-L2TP tcp-udp
port-object eq 1701
port-object eq 500
port-object eq 5500
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group protocol ESP
protocol-object esp
object-group service VPNIPSECL2TP udp
port-object eq 1701
port-object eq 4500
port-object eq isakmp
object-group service DM_INLINE_TCP_4 tcp
port-object eq https
port-object eq smtp
port-object eq www
access-list outside_access_in extended permit icmp any interface outside
access-list outside_access_in extended permit tcp object-group DM_INLINE_NETWORK_1 host Mail-Extern object-group DM_INLINE_TCP_4
access-list outside_access_in extended permit tcp any host Time-Extern object-group DM_INLINE_TCP_1
access-list outside_access_in extended permit tcp any host Devel-Extern object-group DM_INLINE_TCP_2
access-list outside_access_in extended permit object-group DM_INLINE_SERVICE_1 any host DNS-Extern
access-list outside_access_in extended permit tcp any host Mail-Extern object-group DM_INLINE_TCP_3
access-list inside_nat0_outbound extended permit ip any any
access-list DefaultRAGroup_splitTunnelAcl standard permit 19.4.41.0 255.255.255.0
access-list inside_nat0_outbound_1 extended permit ip 19.4.41.0 255.255.255.0 10.5.2.0 255.255.255.0
access-list External standard permit host DNS-Intern
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
ip local pool comodoVPN 10.5.2.10-10.5.2.254 mask 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list inside_nat0_outbound_1
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) Time-Extern Time-Intern netmask 255.255.255.255 dns
static (inside,outside) Devel-Extern Devel-Intern netmask 255.255.255.255 dns
static (inside,outside) DNS-Extern DNS-Intern netmask 255.255.255.255 dns
static (inside,outside) Mail-Extern Mail-Intern netmask 255.255.255.255 dns
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 ownit-route 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
aaa-server AD protocol ldap
aaa-server AD (inside) host Mail-Intern
ldap-base-dn DC=comodo,DC=local
ldap-scope subtree
ldap-login-password *****
ldap-login-dn administrator
server-type microsoft
http server enable
http 192.168.1.0 255.255.255.0 inside
http 192.168.1.0 255.255.255.255 inside
http 19.4.41.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec transform-set TRANS_ESP_3DES_SHA esp-3des esp-sha-hmac
crypto ipsec transform-set TRANS_ESP_3DES_SHA mode transport
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5 TRANS_ESP_3DES_SHA
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto map inside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map inside_map interface inside
crypto isakmp enable inside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh timeout 5
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy DefaultRAGroup internal
group-policy DefaultRAGroup attributes
dns-server value 19.4.41.9
vpn-filter none
vpn-tunnel-protocol IPSec l2tp-ipsec
default-domain value comodo.local
group-policy DefaultRAGroup_1 internal
group-policy DefaultRAGroup_1 attributes
dns-server value 19.4.41.9
vpn-tunnel-protocol l2tp-ipsec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value DefaultRAGroup_splitTunnelAcl
default-domain value comodo.local
group-policy External internal
group-policy External attributes
vpn-filter value External
username test password fOIfF8Cu5/uc66Uy0FRq1g== nt-encrypted privilege 0
service-type remote-access
tunnel-group DefaultRAGroup general-attributes
address-pool comodoVPN
default-group-policy DefaultRAGroup_1
tunnel-group DefaultRAGroup ipsec-attributes
pre-shared-key *****
tunnel-group DefaultRAGroup ppp-attributes
authentication ms-chap-v2
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect pptp
inspect ils
inspect ipsec-pass-thru
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:******
: end
asdm location DNS-Intern 255.255.255.255 inside
asdm location DNS-Extern 255.255.255.255 inside
asdm location Devel-Extern 255.255.255.255 inside
asdm location Time-Extern 255.255.255.255 inside
asdm location Mail-Extern 255.255.255.255 inside
asdm location Fw-Extern 255.255.255.255 inside
asdm location Time-Intern 255.255.255.255 inside
asdm location Mail-Intern 255.255.255.255 inside
asdm location Devel-Intern 255.255.255.255 inside
asdm location Fw-Intern 255.255.255.255 inside
asdm location mailfilter.itsnordic.se 255.255.255.255 inside
asdm location mailfilter2.itsnordic.se 255.255.255.255 inside
asdm location 0.0.0.0 255.255.255.255 inside
asdm location ownit-route 255.255.255.255 inside
no asdm history enable
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2016 09:12 AM
Hi,
I'm a little confused with the description of what you what to do with your remote VPN client traffic. When you say surf do you mean internet traffic or just the split tunnel traffic generated from the VPN clients be sent to your internal gateway?
In either case you can use a tunneled default route to influence the VPN traffic to be send to a specific host, note that any other route in the routing table that is more specific will be used instead of this one since it is a default route.
The command is the same as a default route just that at the end you add the tunneled keyword:
route outside 0 0 x.x.x.x tunneled
x.x.x.x = Next hop IP address
Let me know if this helped or if I misunderstood what you wanted to do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2016 11:42 PM
Hi
The issue we are currently facing is that some companies block so only specific ip addresses can reach them. Currently we use Split Tunneling so we cant access these networks outside of our network.
What i would like is route the VPN traffic via the office so that all the traffic seems to come out of the office so our users can access these networks which require them to be at the office.
I think the solution you posted does that but im not sure how my current default route would affect it?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2016 12:34 AM
I think in this case then what you want to achieve is to NOT use split tunneling, but send all VPN users out of your network, is that correct?
You could disable split tunneling and use a PAT rule such that everyone connecting to your VPN will get PAT'd to your firewalls external IP for example when going out to the Internet. You would also need to use 'same-security permit intra-interface' command
This is covered right here: https://supportforums.cisco.com/discussion/12058841/cisco-asa-connect-ip-outside-remote-access-vpn
Hopefully I have understood what you mean correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2016 11:55 AM
Hello David99,
Adding to what William just recommended, using "tunnelall" the ASA will do the following: Remote users reach internet networks through the corporate network and do not have access to local networks. Instead with the split tunnel the user can access the local Internet with the IP address of your Local ISP, so by using tunnelall the traffic when going to another corporation that is Outside of your network will need to get back to the ASA Outside's interface(Interface where you connect) and with the U-turn (same-security permit intra-interface) the traffic will be sent out outside once again but reaching anything on internet but this time will be translated either to the outside interface of your ASA (PAT'd) or you use another IP address for it, you may find an example of U-turn in the following image:
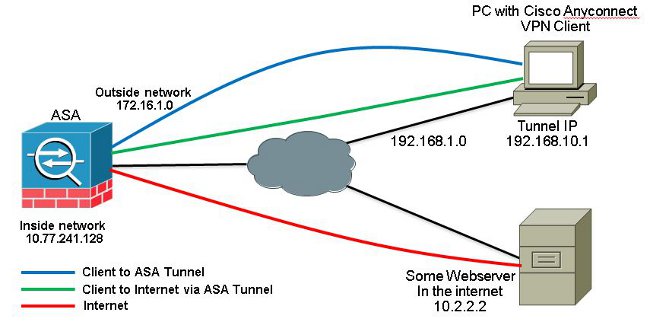
So you configure this commands in order to get this working according to your configuration:
1. NAT (PAT translation from the AnyConnect pool to the Interface)
nat (outside) 1 10.5.2.0 255.255.255.0
2. U-turn command:
same-security permit intra-interface
3. Tunnelall option:
group-policy DefaultRAGroup_1 internal
group-policy DefaultRAGroup_1 attributes
split-tunnel-policy tunnelall
Please proceed to rate and mark as correct this post if it helped you, keep me posted!
David castro,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2016 12:19 PM
Hi,
Ok in this case you have a few options, if you still want to use the split tunnel feature and if you know what the public IPs are for these companies then you can simply add then to the split tunnel configuration so they can be sent through the VPN tunnel and arrive on your firewall.
Once on the firewall the tunneled default route will take care of the routing for your VPN traffic (unless you have a more specific route to that destination, which in your case I believe you don't have). The tunnel default route will only affect your VPN traffic,all other traffic will use the normal routing you have configured.
if you don't know the destination IPs you will be trying to reach for these companies then your best option is to move from a "tunnelspecified" to a "tunnelall" policy. With the tunnelall policy all traffic will be sent to the ASA and from there the ASA will route the traffic where you need it, again the tunnel default gateway can also help you if you what these clients to have internet access through some other device on your internal network.
here is some helpful links with configuration examples, let me know if this is what your were looking for:
Configuring Tunnel Default Gateway Implementations
http://www.cisco.com/c/en/us/products/collateral/security/ios-easy-vpn/prod_white_paper0900aecd805f0bd6.html
ASA 8.X: Routing SSL VPN Traffic through Tunneled Default Gateway Configuration Example
http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/112182-ssl-tdg-config-example-00.html
ASA 9.x: AnyConnect VPN Client U-turning Configuration Examples
http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/100918-asa-sslvpn-00.html
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide