- Cisco Community
- Technology and Support
- Security
- VPN
- Re: DMVPN SSH access to spoke from hub LAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
DMVPN SSH access to spoke from hub LAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2020 07:56 PM
Hey all,
I'm having a heck of a time trying to enable my spoke 5506 asa to allow remote management over a DMVPN tunnel from the hub side of the network. Finally got to a point where I can now ping the inside interface across the tunnel but when I try to ssh, I get the following error (Network error: Software caused connection abort)
I know that this is probably something stupid that I'm missing but I have gone over all the usual suspect commands and at this point could really use a second set of eyes to do a sanity check.
Config is attached
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2020 09:10 PM
What is your src ip from which you're trying to ssh the box?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2020 01:30 AM
Hey Francesco,
I’m specifically trying to ssh from the 192.168.20.X/24 subnet. Although I’m of the belief that I should be able to ssh from any of the subnets in the object-group dm_inline_network_1
Am I missing something that would allow ssh?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2020 10:06 AM
Your remote networks are:
object-group network DM_INLINE_NETWORK_1
network-object object NETWORK_OBJ_192.168.20.0_24
network-object object NETWORK_OBJ_192.168.250.0_24
network-object object NETWORK_OBJ_192.168.23.0_24
network-object object NETWORK_OBJ_10.250.0.0_16
Can you put this config in place and try out?
ssh 192.168.20.0 255.255.255.0 inside
ssh 192.168.250.0 255.255.255.0 inside
ssh 192.168.23.0 255.255.255.0 inside
ssh 10.250.0.0 255.255.0.0 inside
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2020 01:46 PM
I've added those ssh commands. Unfortunately it didn't work and I suspected that it wouldn't due to the previously configured command of (ssh 0.0.0.0 0.0.0.0 inside_2) not working either. See below for updated output of show run ssh.
ASA(config)# show run ssh
ssh scopy enable
ssh stricthostkeycheck
ssh 192.168.0.0 255.255.0.0 OUTSIDE
ssh 192.168.70.0 255.255.255.0 OUTSIDE
ssh 0.0.0.0 0.0.0.0 OUTSIDE
ssh 192.168.102.0 255.255.255.0 inside_2
ssh 0.0.0.0 0.0.0.0 inside_2
ssh 10.250.0.0 255.255.0.0 inside_2
ssh 192.168.23.0 255.255.255.0 inside_2
ssh 192.168.250.0 255.255.255.0 inside_2
ssh 192.168.20.0 255.255.255.0 inside_2
ssh 192.168.102.0 255.255.255.0 inside_3
ssh 192.168.102.0 255.255.255.0 inside_4
ssh 192.168.102.0 255.255.255.0 inside_5
ssh 192.168.102.0 255.255.255.0 inside_6
ssh 192.168.102.0 255.255.255.0 inside_7
ssh 192.168.102.0 255.255.255.0 inside_8
ssh timeout 15
ssh version 2
ssh key-exchange group dh-group1-sha1
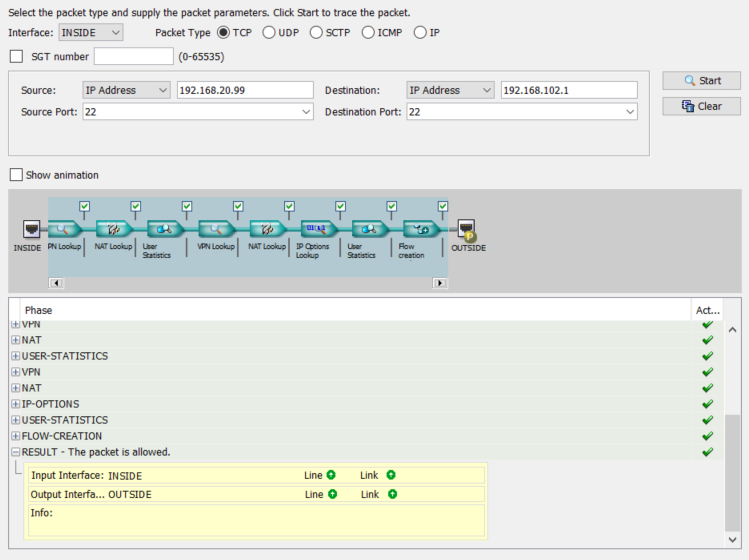
Also worth mentioning, is that when I do a packet trace using port 22 from the hub ASA it appears to be pass all ACL's configured.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2020 04:02 PM
Can you do a capture (tcpdump) on asa to see if packets are arriving?
Also do capture asp-drop to validate if there're packets dropped.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide