- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Easy/Ez VPN unidirection traffic flow issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Easy/Ez VPN unidirection traffic flow issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2017 07:46 PM - edited 03-12-2019 04:42 AM
Hi All,
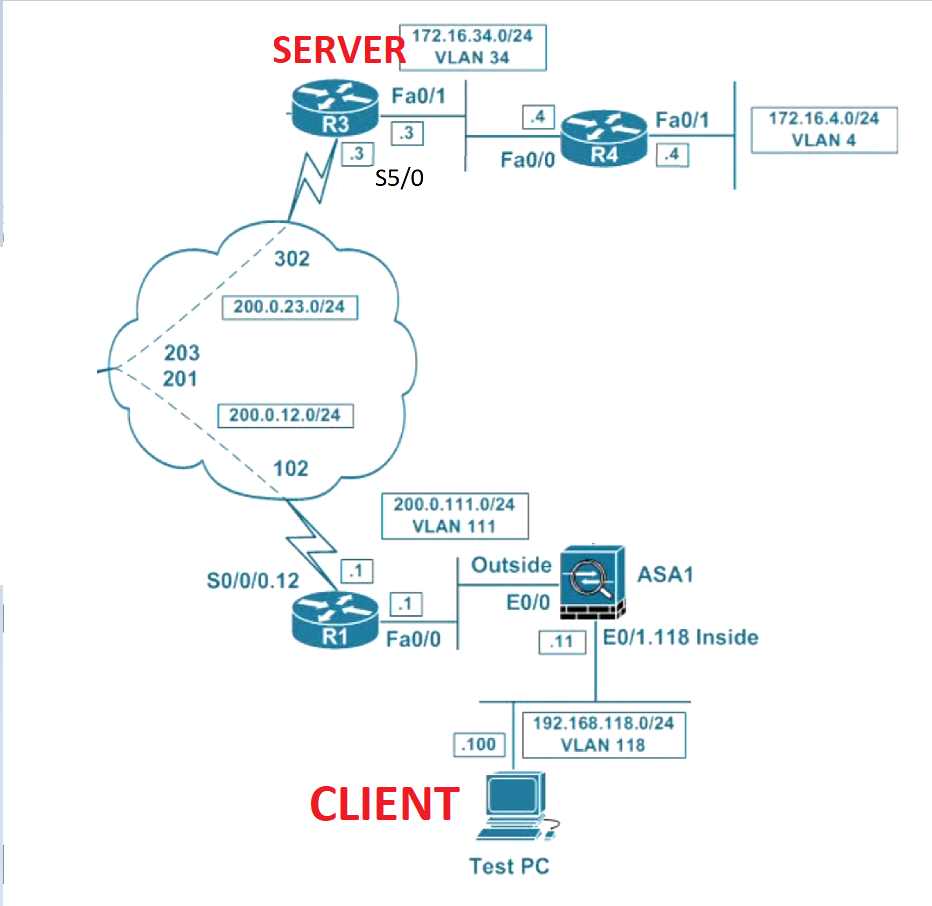
I have an EZ VPN setup where the client has sucessufully connected to the client. However, when the client pings the device behind the server, I do not see any response.
The device behind the server is responding. I could also see decaps/decrypt in server but no encaps/encrypt in the server
Below is the log and configuration:
R3(config-if)#do sho crypto ipsec sa
interface: Virtual-Access1
Crypto map tag: Virtual-Access1-head-0, local addr 200.0.23.3
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (172.16.100.2/255.255.255.255/0/0)
current_peer 192.168.118.100 port 58869
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 54, #pkts decrypt: 54, #pkts verify: 54
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 200.0.23.3, remote crypto endpt.: 192.168.118.100
path mtu 1500, ip mtu 1500, ip mtu idb Serial5/0
current outbound spi: 0xC042F9A7(3225614759)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x1CA4D994(480565652)
R3(config-if)#do sho run int virtual-template 1
Building configuration...
Current configuration : 144 bytes
!
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
tunnel mode ipsec ipv4
tunnel protection ipsec profile CRYPTO_PROFILE
end
R3(config-if)#do sho run | s crypto
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp client configuration group GROUP1
key cisco
pool POOL1
crypto isakmp profile ISAKMP_PROFILE
match identity group GROUP1
client authentication list AUTH_LIST
isakmp authorization list AUTH_LIST
client configuration address respond
client configuration group GROUP1
virtual-template 1
crypto ipsec transform-set TSET esp-3des esp-sha-hmac
mode tunnel
crypto ipsec profile CRYPTO_PROFILE
set transform-set TSET
aaa new-model
aaa authentication login AUTH_LIST local
aaa authorization network AUTH_LIST local
- Labels:
-
Other VPN Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2017 05:08 AM
Your traffic of interest looks weird:
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (172.16.100.2/255.255.255.255/0/0)
can you confirm?
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2017 03:51 PM
That is how it is dynamically created for EzVPN :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2017 05:02 PM
400+ views and just one response!! isin't there anyone who can help out on this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2017 05:57 PM
Share the running-config please. The configuration you shared is not enough.
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2017 06:27 PM
here you go:
R3#sho run
Building configuration...
Current configuration : 2496 bytes
!
version 15.2
service timestamps debug datetime msec
service timestamps log datetime msec
!
hostname R3
!
boot-start-marker
boot-end-marker
!
!
!
aaa new-model
!
!
aaa authentication login AUTH_LIST local
aaa authorization network AUTH_LIST local
!
!
!
!
!
aaa session-id common
no ip icmp rate-limit unreachable
!
!
!
!
!
!
no ip domain lookup
ip cef
no ipv6 cef
!
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
username salman password 0 cisco_user
!
!
!
!
!
ip tcp synwait-time 5
!
!
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
!
crypto isakmp client configuration group GROUP1
key cisco
pool POOL1
crypto isakmp profile ISAKMP_PROFILE
match identity group GROUP1
client authentication list AUTH_LIST
isakmp authorization list AUTH_LIST
client configuration address respond
virtual-template 1
!
!
crypto ipsec transform-set TSET esp-3des esp-sha-hmac
mode tunnel
!
crypto ipsec profile CRYPTO_PROFILE
set transform-set TSET
!
!
!
!
!
!
!
interface Loopback0
no ip address
!
interface FastEthernet0/0
ip address 192.10.192.3 255.255.255.0
duplex full
!
interface FastEthernet1/0
ip address 172.16.34.3 255.255.255.0
speed auto
duplex auto
!
interface FastEthernet1/1
no ip address
shutdown
speed auto
duplex auto
!
interface FastEthernet2/0
no ip address
shutdown
speed auto
duplex auto
!
interface FastEthernet2/1
no ip address
shutdown
speed auto
duplex auto
!
interface GigabitEthernet3/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet4/0
no ip address
shutdown
negotiation auto
!
interface Serial5/0
ip address 200.0.23.3 255.255.255.0
encapsulation frame-relay
serial restart-delay 0
!
interface Serial5/1
no ip address
shutdown
serial restart-delay 0
!
interface Serial5/2
no ip address
shutdown
serial restart-delay 0
!
interface Serial5/3
no ip address
shutdown
serial restart-delay 0
!
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
tunnel source Serial5/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile CRYPTO_PROFILE
!
!
router eigrp 1
network 172.16.0.0
network 192.10.192.0
network 200.0.23.0
!
ip local pool POOL1 172.16.100.1 172.16.100.100
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
!
!
!
!
!
control-plane
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line vty 0 4
!
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2017 06:51 PM
Tell me in which interface the device is connected and the output of show ip route.
Also, is this a GNS3 lab? Can you share with me the file? I have a EasyVPN on GNS3 here and it is working.
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2017 11:18 AM
Add a static route 172.16.100.0 /24 to the outside
or add reverse route injection.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide