- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Error after upgrade to AnyConnect 4.10.07061
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Error after upgrade to AnyConnect 4.10.07061
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2023 01:36 AM
After an upgrade from AnyConnect 4.10.06079 to 4.10.07061 we have this error on our clients "The VPN connection was terminated due to loss of the network interface. A new connection is necessary, which requires re-authentication."
We use Gina to log in the VPN before we use the Windows login. The first VPN login sucess and after the login in windows, AnyConnect destroy the VPN-Tunnel with the Error-Message "The VPN connection was terminated due to loss of the network interface. A new connection is necessary, which requires re-authentication."
Can Anybody help?
- Labels:
-
AnyConnect
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2023 01:26 AM
Keep an eye on https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwf67833.
Yesterday's info from TAC was: "I'm hoping that the next fix release for AnyConnect will be available shortly."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2023 09:12 PM
CSCwh51369 is recently raised to track this issue. It appears that there is no workaround at the moment, so please hold off upgrade activity in the production or downgrade to v4.10.06079 until fix comes out. Hope this helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 08:46 AM
I see the bug tracker page was updated. Status was updated to "Fixed" but I do not see the actual solution? I don't see a new client version available for download either.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 09:03 AM
Hi Jeremy,
The fix will go in CSC 5.1 FCS release, which is tentatively planned for end of Oct (subject to change due to any unforeseen reasons).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2023 09:05 AM
Will they not be fixing the bug in AnyConnect 4.x?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2023 07:54 AM
Hello,
i tried CSC 5.1.0.136 but the issue is still there Are there any updates for a fix?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2023 11:41 PM
Secure Clients 5.0.03072 and higher are affected by the Porxy Issue. The only/last version that is not affected is 5.0.02075.
And 5.0.02075 has the fix for the vulnerabitlity Cisco AnyConnect Secure Mobility Client Software for Windows and Cisco Secure Client Software for Windows Privilege Escalation Vulnerability.
So it is the last usable and secure version.
For 4.10 there's no version where the vulnerability is fixed and proxy settings are ok.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2023 11:19 PM
Unfortunately a fix in Version 5.x won't help.
We are using version 4.10 and implemented various scripts basing on V4.10.
Since V5 is very different from V4 in many ways, we would have to put a lot of effort into adapting it. We have to wait for a fix in version 4.10.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2023 10:54 AM
At this point, there is no ETA for next release in 4.10.x branch. I'll keep this thread posted as I know the ETA. Also, please note that 4.10 is going to be EoS on 31st March 2024 : https://www.cisco.com/c/en/us/products/collateral/security/anyconnect-secure-mobility-client/anyconnect-secure-mobility-client-v4x-eol.html . So, we recommend Customers to move to Cisco Secure Client (CSC) 5.x & 5.1 is planned for release before next release in 4.10.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2023 11:29 PM
Moving to V5 is no option, because there are too many changes in behaviour and modules to use the established automations we have. We will need nearly the whole time until EoL of V4 to adapt everything to V5. And I don't understand why we should spend our rare time trying to work around the issue. It was created within a version, so it should be possible to remove it within a version.
Since exactly the same issue was "invented" with the last update of V5 shows me, it must be the same module/library that is used for V4 and V5. When it is fixed in V5, why not in V4, if it is the same code snippet?
Is this a political decision to push customers to V5?
V4 has a massive security issue that was fixed, when the proxy issue was "introduced".
Cisco AnyConnect Secure Mobility Client Software for Windows and Cisco Secure Client Software for Windows Privilege Escalation Vulnerability
But the fix is not usable and the security issue still exists.
That's fact...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2023 07:55 AM - edited 10-03-2023 07:55 AM
These were the last responses I received from TAC before the ticket was closed.
Hello,
The default value of msie-proxy lockdown is enabled by default, it is not in the CLI config as it is not manually set.
You should be able to change it from ASDM as well. Edit the Group policy > Advanced> Browser Proxy > Proxy Lockdown, uncheck Inherit and check No.
As you can see from the document, this option allows Anyconnect to make changes to the browser proxy setting for the duration of the anyconnect session.
In certain conditions those changes may not be reverted. As my colleague mentioned the root cause of the issue is not yet isolated and Cisco is working with Microsoft for a permanent fix.
You can subscribe to the bug to follow up on any progress on it - https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwf67833
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2023 11:19 PM
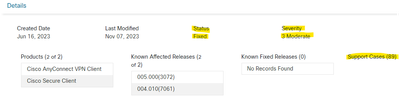
Is Cisco really working on this issue?
Status "Fixed", Severity "Moderate", no fixed releases but 89 support cases.
CSCwf67833 : Bug Search Tool (cisco.com)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2023 05:46 AM
This is affecting us on CSC 5.x also so I cant see how they wouldn't be addressing it, whether they fix in in 4.10 or not will be the question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2023 06:53 AM
Just got this from TAC for the CSC 5.x may help others.
Secure Client is not supported on ASA versions older than 9.14. If you want to continue using remote access VPN, you will need newer hardware.”
https://www.cisco.com/c/en/us/td/docs/security/asa/compatibility/asa-vpn-compatibility.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2023 04:22 AM
Here some news from Cisco:
"Initially, the problem was solved with the recommendation of disabling the lockdown setting. While checking the bug, it will be fixed on AnyConnect 4.10MR8. The latest available version in Cisco Downloads is AnyConnect 4.10MR7 (4.10.07073). Next release of AnyConnect should include the fix. As for the secure client, there's no need to download it in order to fix this issue.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide