- Cisco Community
- Technology and Support
- Security
- VPN
- Re: facing challenge to integrate AD Security Group in ASA.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2018 07:41 AM - edited 03-12-2019 05:11 AM
Hi
we integrated Active Directory with ASA for Anyconnect VPN Authentication. in AD we have created 2 x Security Group ( both security groups are part of the same OU ).
on ASA we created 2 different VPN group and want to integrate each vpn group with separate Security Group in AD.
here we are facing challenge
we used Dynamic Access Policy to restrict users. in DAP we called both Security Groups.
now any user which is not part part of the these 2 security Group will not authenticate ( this is ok )
Issue
users in both security groups can use both vpn group ( we want to restrict one VPN group with one Security group in AD which is somehow not working and security group users can access both VPN group )
is there any way that we can restrict each AD security group with VPN group policy/ tunnel group so users in one security group should not authenticate for other VPN group
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2018 12:47 PM
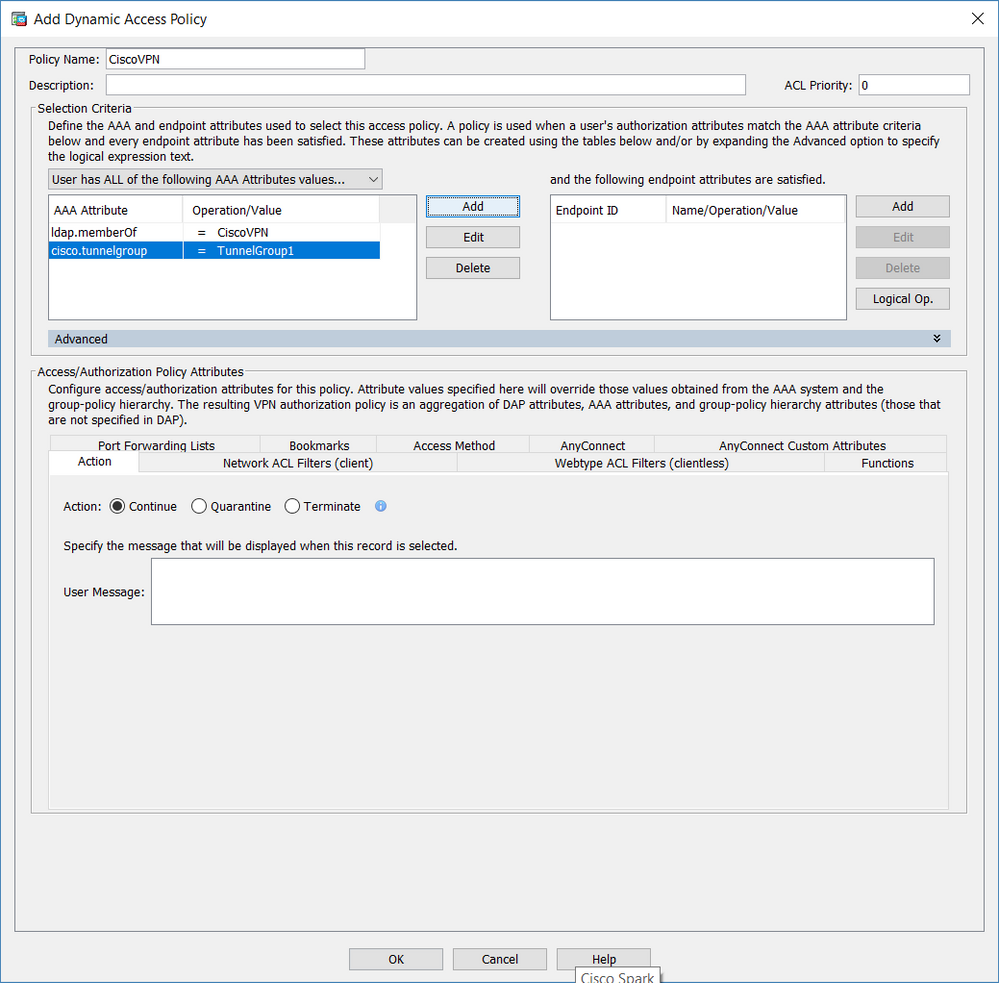
The condition for your DAP policy is only AD group.
DAP record [ CiscoVPN ]: (EVAL(aaa.ldap.memberOf,"EQ","CiscoVPN","caseless"))
Add another condition to the DAP policy to check Tunnel-group or connection profile. Look the picture attached carefully.
Make the change for both DAP records.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2018 08:33 AM
Can you share a snippet of your DAP policy?
Also, your issue was not clear:
is there any way that we can restrict each AD security group with VPN group policy/ tunnel group so users in one security group should not authenticate for other VPN group
So do you want to make sure user who is part of AD group A should only be able to access VPN tunnel-group A and not tunnel-group B? If your DAP policy is set up with condition like below this should be possible:
DAP 1 - If AD group A (and) Tunnel group A - Then Allow
DAP 2 - If AD group B (and) Tunnel group B - Then Allow
DAP 3 - Deny
There may be other ways to do this without DAP using Radius and LDAP attributes. Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2018 11:56 AM - edited 04-10-2018 12:07 PM
Hi Rahul
DAP 1 - If AD group A (and) Tunnel group A - Then Allow
DAP 2 - If AD group B (and) Tunnel group B - Then Allow
DAP 3 - Deny
yes, you are right but i am not able to bind AD security group with Tunnel group in DAP but only able to bound AD security group with ACL ( so in this case user belong to one AD Security group can still login and authenticate with other group tunnel group but cannot use other group resources.
dynamic-access-policy-record DfltAccessPolicy
action terminate
dynamic-access-policy-record VPNUser
network-acl ldap_user
dynamic-access-policy-record VPNAdmin
network-acl ldap_admin
in Active Directory we have one User Group ( OU ) = Local Users . in Local Users group we have multiple users. suppose we have 2 users ( appadmin + auditor )
we created 2 Security group ( vpnadmin + vpnusers ) inside Local Users group (OU)
security group vpnadmin contain user appadmin
security group vpnusers contain user auditor
OU=local user >>> security group = vpnadmin >>> user = appadmin
OU=local user >>> security group = vpnusers >>> user = auditor
in ASA we want to map security group vpnadmin with tunnel group admin and security group vpnusers with tunnel group users
i did following configuration for LDAP
aaa-server MALA-LDAP protocol ldap
aaa-server MALA-LDAP (inside) host DC-172.20.10.140
ldap-base-dn dc=RI,dc=local
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn ciscodirsync@RI.local
server-type microsoft
Tunnel group
tunnel-group RASMALA-PK type remote-access
tunnel-group RASMALA-PK general-attributes
address-pool RASMALA_POOL
authentication-server-group RASMALA-LDAP
default-group-policy GroupPolicy_RASMALA-PK
tunnel-group RASMALA-PK webvpn-attributes
group-alias RASMALA-PK disable
group-alias ul enable
group-url https://secure.mala.com/ul enable
tunnel-group RASMALA-ADMIN type remote-access
tunnel-group RASMALA-ADMIN general-attributes
address-pool Rasmala-Pool2
authentication-server-group RASMALA-LDAP
default-group-policy GroupPolicy_RASMALA-Admin
tunnel-group RASMALA-ADMIN webvpn-attributes
proxy-auth sdi
group-alias ad enable
group-url https://secure.mala.com/ad enable
we disabled login option for users so when a users from particular security group try to login it should not see connection profile selection option.
We used DAP and mapped each security group with desired ACL ( interesting traffic which the user will access after authentication )
dynamic-access-policy-record DfltAccessPolicy
action terminate
dynamic-access-policy-record VPNUser
network-acl ldap_user
dynamic-access-policy-record VPNAdmin
network-acl ldap_admin
ISSUE
user belong to any security group can login to both tunnl group but user cannot access the other group network resource as in DAP we bound the security group with ACL
Our requirement
If user belong to one AD security group and try to login other security group then it should not authenticate
In our case user can login but since we are binding security group with ACL in DAP then user cannot use resources but
We want to bind Security Group with Tunnel Group but in DAP I am not able to bind Security group with Tunnel Group but only security group with ACL
Is there any way I can bind security group with Tunnel group so user should not authenticate while try to login other tunnel group.
Currently user can authenticate but cannot access the network because of DAP and we don’t even want user to authenticate as well. But in DAP I don’t see any option to bind security group with tunnel group
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2018 03:37 PM
Paste the output of "debug menu dap 2"
If you have the DAP policy as I had mentioned, a user in Group B should not be able to authenticate to tunnel-group A. The only DAP policy that will match is the default DAP set to deny.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2018 09:34 AM
Hi Rahul
debug output
RMGVASA01/act/pri# debug menu dap 2
DAP record [ CiscoVPN ]:
(EVAL(aaa.ldap.memberOf,"EQ","CiscoVPN","caseless"))
DAP record [ CiscoVPNAdmin ]:
(EVAL(aaa.ldap.memberOf,"EQ","CiscoVPNAdmin","caseless"))
DAP record [ imsvpn ]:
(EVAL(aaa.cisco.username,"EQ","imsvpn","caseless"))
RMGVASA01/act/pri#
both DAP policy are map with Network ACL ( in DAP there is no option to map with Group )
RMGVASA01/act/pri(config)# dynamic-access-policy-record VPNAdmin
RMGVASA01/act/pri(config-dynamic-access-policy-record)# ?
dynamic access policy record configuration commands:
action Enter the action for this policy
description Enter a quote "" delimited description for this policy
exit Exit from dynamic-access-policy-record configuration mode
help Help for dynamic access policy record configuration commands
network-acl Enter an access-list identifier
no Remove an attribute value pair
priority Specify the priority number for this policy
quit Exit from dynamic-access-policy-record configuration mode
user-message Enter a quote "" delimited user message for this policy
webvpn Configure dynamic-access-policy for WebVPN specifics
is there any other way that i can map tunnel group policy with AD Security group ( not AD OU )
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2018 12:47 PM
The condition for your DAP policy is only AD group.
DAP record [ CiscoVPN ]: (EVAL(aaa.ldap.memberOf,"EQ","CiscoVPN","caseless"))
Add another condition to the DAP policy to check Tunnel-group or connection profile. Look the picture attached carefully.
Make the change for both DAP records.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2018 09:11 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide