- Cisco Community
- Technology and Support
- Security
- VPN
- FlexVPN with F-VRF and multiple tunnels
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FlexVPN with F-VRF and multiple tunnels
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2013 01:56 AM - edited 02-21-2020 06:53 PM
Hi There,
I have a burning question and initially need to understand the possibility of the following scenario, below is a diagram of a single point-to-point connection used for proof of concept. The Hub router acts as a local RADIUS and is to issue IP addresses for both the client tunnel interfaces.
Two separate tunnels are required, one between Virtual-template 1 and tunnel 1 and one between Virtual-template 2 and tunnel 2, hence they are within a separate VRF on both routers.
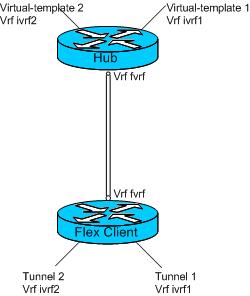
Basically I am wondering if this is possible as getting this to work is a struggle.. I am currently using PSK authentication, though also wondering if there would be issues using certificates, i.e. the hub would effectively receive two separate SAs with the same certificate.
The flex client and hub have separate profiles keyrings etc for each connection...
Has anyone got this working before??
Any help or suggestions/pitfalls would be appreciated.
- Labels:
-
FlexVPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2013 10:29 PM
Hello,
Currently you can't have 2 tunnels sharing the same source and destination [ However in a near future, it's something that will be possible too].
2 Options:
1. If you can have 2 public addresses on the hub [ One per tunnel] then it will work without issues.
- Downside:
U will lower the scalability of the hub by doubling the number of tunnels
2. use MPLS over flex to extend your vrf across the network. It's very easy to deploy or maintain.
- Downside:
Spoke to Spoke communication will be available only few months from now. Currently Spoke - Spoke would go via the hub.
Cheers,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2013 12:16 PM
Hi Olpeleri,
Many thx for the reply,
I have tried using two interfaces on the Hub, though no joy so far..... I want to have the hub tunnel end points in different VRFs, hence I have tried with two virtual templates A and B and interfaces A and B in different VRFs to each other.
i.e, looking at just one tunnel to start with,
HUB
interface Virtual-Template1 type tunnel
ip vrf forwarding VRF_A
ip unnumbered Loopback20
tunnel source Ethernet0/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSEC-PROFILE
end
!
interface e0/0
ip vrf forwarding VRF_A
ip address 172.16.0.2 255.255.255.0
!
Is this config correct, I have tried using a front door VRF for each interface also, though the tunnel fails to build when both interfaces are there
The profile looks like this repeated for each interface with different names and virtual template etc..
!
crypto ikev2 profile default
match fvrf any
match identity remote fqdn domain cisco.com
identity local fqdn Hub1.cisco.com
authentication remote pre-share
authentication local pre-share
keyring ALL
pki trustpoint cisco
dpd 10 2 periodic
aaa authorization group psk AUTHOR_LIST AUTHOR_POL
virtual-template 1
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2013 10:19 PM
2 questions;
1. VT1 is sourced from
tunnel source Ethernet0/0
That means you are trying to resolve spokes that are in that vrf [VRF_A]
U are missing tunnel vrf VRF_A in order to let the Virtual-Template the VRF where it needs to do for adjacency lookup
2. What version do you run? I see here the old CLI in regard of the keyring - Debugs are more readable in the new code. Can you try 152(4)M3?
Cheers,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-24-2013 02:17 PM
Hi there.... I believe that two tunnels are now possible between routers in hub and spoke, can you confirm?
I have a hub connected via Ethernet and the spokes on adsl/3G
Thanks
Sent from Cisco Technical Support iPad App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2014 11:28 PM
It has always been working If the endpoints have different IP's [ eg one tunnel sourced from ADSL / one tunnel sourced from 3G]
in 15.4(1)T, we have added support for 2 tunnels between the same IP endpoints.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2014 01:05 PM
Thanks for the confirmation
Sent from Cisco Technical Support iPad App
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide