- Cisco Community
- Technology and Support
- Security
- VPN
- FMC intrusion event Anyconnect
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FMC intrusion event Anyconnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 06:27 AM
Hello,
Is there a setting to change for an alert to get notified for a brute force login attempts to ravpn/anyconnect via the FMC?
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 09:40 AM
Hi,
When the user/client fails authentication, you'll get a message of "%ASA-6-611102: User authentication failed.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 10:18 AM
Right, so there is no way to send that or trigger an alert message via fmc?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 11:29 AM
are you using ASA with sfr sensor. or you using FTD?
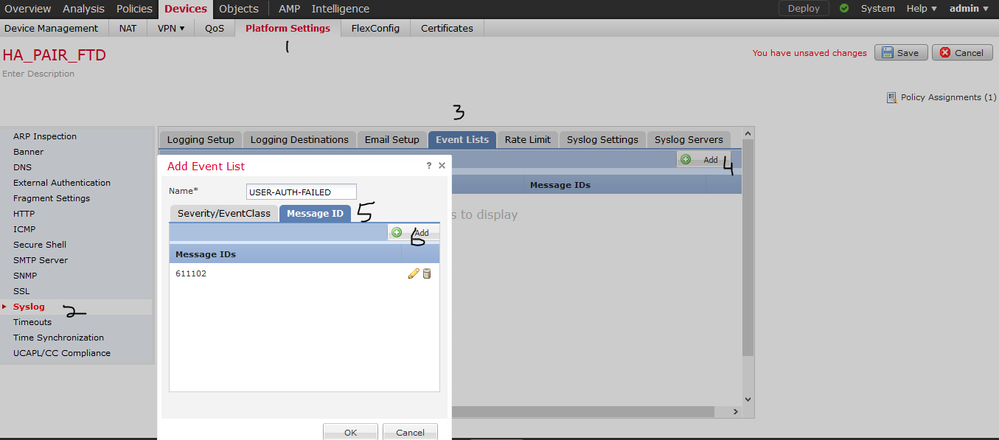
with ASA sfr sensor I am afraid you cant setup the alert on FMC. its only set up on ASA and could get a syslog message as @Cristian Matei mentioned.
however, if you using FTD than yes. you can configure the logging/alerts setup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 11:36 AM
I'm using FMC to manage my FTD appliances. They are not running in ASA mode.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 02:51 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2020 07:28 AM
Thanks, I just got around to testing this. I might open a case with tac. I tried the recommended filter and was not getting anything in my syslog. I deleted the filter, then just send anything informational to my syslog then I started to see the logs roll in. I tried some failed logins to my vpn, but I am not seeing them come in via syslog. If I grep for 611102, nothing shows up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2020 06:55 AM
The correct logging event is %ASA-6-113005.
There appears to be a bug where it doesn't show the username. But this is what I am looking for to monitor failed anyconnect login attempts.
https://networkengineering.stackexchange.com/questions/9620/cisco-vpn-logs-do-not-show-the-username
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide