- Cisco Community
- Technology and Support
- Security
- VPN
- FPR 1010 Debugging Ipsec
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FPR 1010 Debugging Ipsec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 07:54 AM
Hi all,
i have a FPR 1010 with site-to-site tunnel configured with preshared key but it dosent connect to remote peer
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 07:56 AM
many reason may cause this
but the first is
can you ping the remote peer ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 08:28 AM
Yes i can ping the peer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 10:08 AM
are you have dual WAN interface ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 10:21 AM
No i have one Wan interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2022 10:33 AM
Please share your sanitized configs for review.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2022 03:03 AM
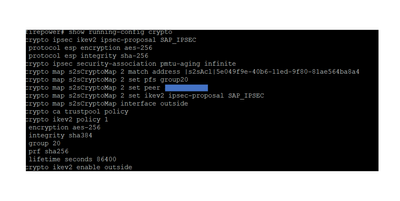
this is my configuration
show running-config crypto
crypto ipsec ikev2 ipsec-proposal SAP_IPSEC
protocol esp encryption aes-256
protocol esp integrity sha-256
crypto ipsec security-association pmtu-aging infinite
crypto map s2sCryptoMap 2 match address |s2sAcl|5e049f9e-40b6-11ed-9f80-81ae564ba8a4
crypto map s2sCryptoMap 2 set pfs group20
crypto map s2sCryptoMap 2 set peer xxx.xxx.xxx.xxx
crypto map s2sCryptoMap 2 set ikev2 ipsec-proposal SAP_IPSEC
crypto map s2sCryptoMap interface outside
crypto ca trustpool policy
crypto ikev2 policy 1
encryption aes-256
integrity sha384
group 20
prf sha256
lifetime seconds 86400
crypto ikev2 enable outside
crypto ikev1 policy 150
authentication rsa-sig
encryption des
hash sha
group 5
lifetime 86400
crypto ikev1 policy 160
authentication pre-share
encryption des
hash sha
group 5
lifetime 86400
when i check the tunnel is down and there isn't assocation with ikev2 e isakmp..
how can i debug the process of connection?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2022 03:25 AM
crypto ikev2 enable outside
but you dont have any IKEv2 policy config ??
the config is for IKEv1 not for IKEv2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2022 03:49 AM
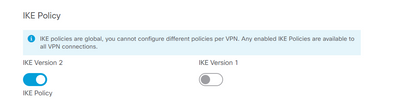
i create the tunnel from the web interface and i select IkeV2 policy
to enable crypto ikev2 on outside interface i need f the console ( usb cable ) or ssh session from the managment interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2022 05:56 AM - edited 10-03-2022 06:02 AM
use the management Interface (ssh to it). login to it and give these command
>
> expert
FTD:~$ sudo sfconsole
debug crypto condition peer x.x.x.x
debug crypto ikev2 platform 255
debug crypto ikev2 protocol 255
debug crypto ipsec 255
have to configure the NAT rules (NAT exmption) I do not see it. unless you have not posted them.
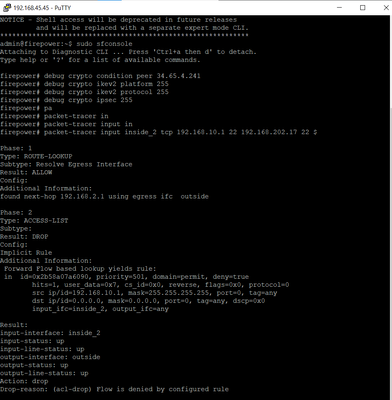
you can run the packet-trace command on your CLI.
packet-tracer input inside tcp c.c.c.c.c 22 d.d.d.d.d 22 detail
where c.c.c.c is source and d.d.d.d is destination of the remote network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2022 07:22 AM
this is the output
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2022 07:26 AM
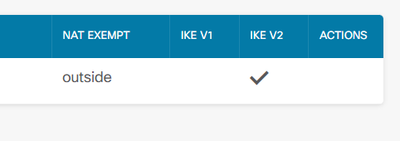
this is the configuration with nat and ikev2 only enabled but i cant see the vpn tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2022 07:49 AM - edited 10-03-2022 07:52 AM
In order to see the live logs you have to put a command "terminal monitor"
looking into your screen shots you are not hitting your ACL rule. have you define the ACL and NAT rules?
have a look on this provided link I guess you are using stand-a-lone FTD
Configure Site-to-Site VPN on FTD Managed by FDM - Cisco
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2022 01:07 AM
You had a NAT issue once fixed the traffic was going through the tunnel.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide