- Cisco Community
- Technology and Support
- Security
- VPN
- Re: FTD Client VPN no longer works after enabling Umbrella SIG
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2021 02:34 AM
Hello
We had a very nice Client VPN solution on our FTD 2100 to allow our users to connect with AnyConnect. Then came along Umbrella SIG ... and now we have no more VPN. The https connection to the VPN also doesn't work. But we can still ping the address.
On the bright side, SIG works.
There were some Policy changes made to allow the Umbrella "bypass" (I don't fully get my head around it)
Any clues on whether these two features should co-exist?
regards
Arne
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Remote Access
-
Umbrella
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2021 05:35 PM
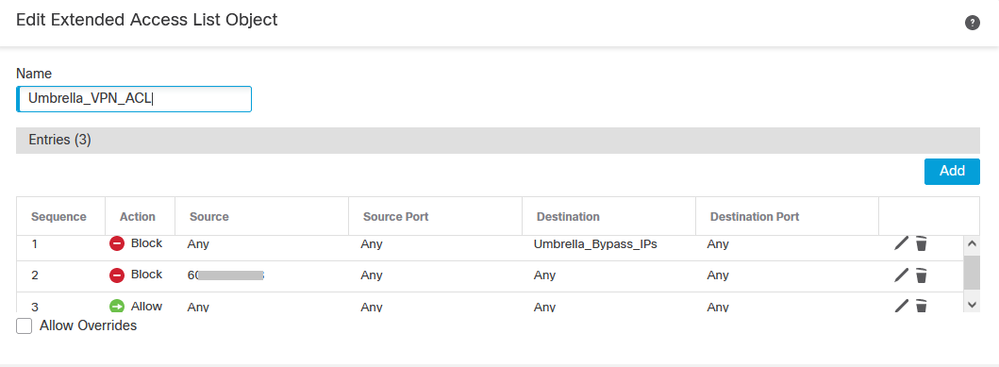
Finally solved the mystery. I had to add rule 2 below, which was to block the outside interface's IP address (public IP address) of the VPN service. Hey presto!
The Umbrella_Bypass_IPs Network Group contains all the Umbrella IP addresses and SIG IP's (208.67.222.222, 208.67.220.220, 146.112.0.0/16, 155.190.0.0/18 )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2021 09:17 PM
I haven't done a SIG deployment yet but there are a couple of caveats noted in the Umbrella documentation. I see them listed on this page:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2021 09:27 PM
Thanks Marvin. Before we implemented SIG we had no issues with VPN even with laptops that had umbrella roaming client and/AnyConnect with Umbrella module. That’s not the issue.
The issue is that the FTD that was hosting our VPN is broken ever since we enabled SIG. VPN not responding. We only have one private IPv4 address for the outside interface. I was wondering what could have broken the VPN? Can’t see where in the FMC I can monitor the AnyConnect connection attempts or even the attempts to the VPN https address of the FTD?
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2021 04:11 AM
Hmm. you can can check if the FTD is "listening " for SSL VPN clients with "show asp table socket". You should see something like this:
> show asp table socket Protocol Socket State Local Address Foreign Address SSL 0000f3b8 LISTEN 192.168.0.206:443 0.0.0.0:* DTLS 000163b8 LISTEN 192.168.0.206:443 0.0.0.0:* >
You can also setup more detailed logging under the platform settings in FMC (Devices > Platform Settings > Syslog > Logging Setup > VPN Logging Settings) and tell your FTD to log VPN events at informational (or even debug) level to FMC. You will then get the VPN-related syslog messages under the Devices > VPN > Troubleshooting menu.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2021 02:45 AM
thanks @Marvin Rhoads - I will have a look when I am back in the office.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2021 04:30 PM
@Marvin Rhoads - I see the asp table output is showing the correct data. Thanks for that handy command.
I didn't get far with the Syslog part. When I select Devices > Platform Settings in the FMC I only see this, and I can't figure out where those commands go? FMC 6.6.1 (build 91)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2021 07:12 AM
Did you whitelist your company public IPs in SIG?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2021 02:44 AM
@rschlayer - do you have an example of how one would do that?
I'm still looking for a SIG deployment guide on the FTD that makes sense. I think I have scoured the net only to find a lot of good documents on ASA - but not FTD. I didn't deploy this myself - I am trying to make sense of it all still ..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2021 05:35 PM
Finally solved the mystery. I had to add rule 2 below, which was to block the outside interface's IP address (public IP address) of the VPN service. Hey presto!
The Umbrella_Bypass_IPs Network Group contains all the Umbrella IP addresses and SIG IP's (208.67.222.222, 208.67.220.220, 146.112.0.0/16, 155.190.0.0/18 )
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide