- Cisco Community
- Technology and Support
- Security
- VPN
- FTD SCEP Enrollment Error - Identity Certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2021 04:57 AM
Alright, so I'm not an expert on PKIs, but this particular problem is perplexing me to the point of posting. Hoping someone has seen this one.
I have a deployment of FMC managing a few FTDs. Looking to terminate our RA VPN on these devices. Part of this whole thing is getting a certificate on the device, as is typical, and I'm hitting road blocks all over the place on this. Did manual. That was acting so weird I decided to do SCEP. This is also acting weird, but is now my preferred method of enrollment for this deployment.
Set it up with the following configurations (I can't post pictures):
Enrollment Type: SCEP
Enrollment URL: http://10.1.1.3/certsrv/mscep/mscep.dll
Challenge Password: Obtained from the mscep_admin, using the same http:// format as above
Include FQDN: Use device hostname (tried this without as well, no change)
Include Device IP: No
CN: vpn1.my.domain
OU, O, L, ST, C, E: All set
Include Serial Number: No
Key: RSA:2048
Ignore IPSec Key Usage: No, because I have the IPSec on the template referenced
Revocation Check: None
As far as SCEP, I'm using MSCEP on a Server 2019 Sub CA. I have modified the template key in the registry to use my custom template, however it doesn't work when setting back to IPSec Offline either. I have confirmed that the certificate is in the issuance state. I have used this exact same configuration (other than the CN changing) on all of our network appliances for DOT1X EAP TLS authentication identity certificates. So... I know it works.
But it doesn't. Normally I would assume communication is the issue, but after creating a Platform Settings profile (didn't know that was a thing, so at least I learned something on this) the strangest thing is happening: the CA certificate is retrieved, correct, and all the data within is correct. The identity certificate, however, is errored out and states in perfect English (sike): "Fail to configure Identity certificate".
So, that's where I'm at. Communication is established (retrieves the CA certificate) but I do not see the request for the certificate under Failed, Pending (not configured for this, but checked anyway) or Issued Certificates in the CA console.
Any help is sorely needed in this, as I feel my sanity slipping. Thank you.
Solved! Go to Solution.
- Labels:
-
Remote Access
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2021 02:10 AM
Hi never did SCEP I have expeirnce doing with manual enrollment. so might this help you. I know you asking for SCEP.
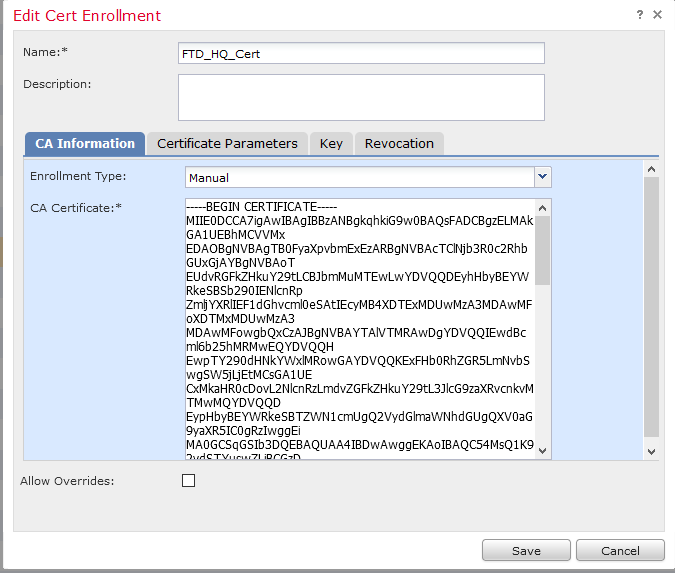
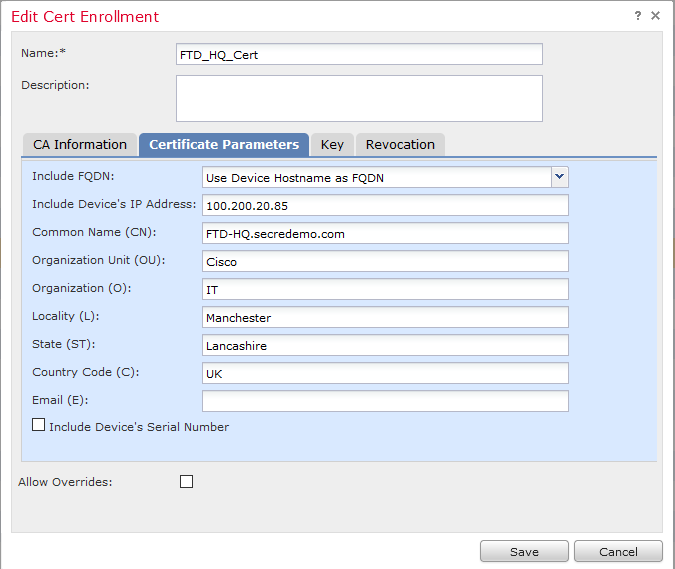
PKI-->Cert Enrollment Add Cert Enrollment
Than go to Devices ---- Certificates you will see Add (button) on the right top hand side. it will bring up a topup "Add New Certificate"
here you will call your FTD-HQ-Cert (Cert Enrolment) once the cert is uploaded. you will generate the CSR. To generate the CSR you will click on the "ID". once you have the CSR you have to take it to your CA and get it signed. Incase you have root CA and intermediate CA in that case you must have to enroll both of them as mentioned in PKI.
there is a cisco tac video uploaded for the anyconnect with cert here might find you useful
https://www.youtube.com/watch?v=ZZRVAFcSZCA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2021 02:10 AM
Hi never did SCEP I have expeirnce doing with manual enrollment. so might this help you. I know you asking for SCEP.
PKI-->Cert Enrollment Add Cert Enrollment
Than go to Devices ---- Certificates you will see Add (button) on the right top hand side. it will bring up a topup "Add New Certificate"
here you will call your FTD-HQ-Cert (Cert Enrolment) once the cert is uploaded. you will generate the CSR. To generate the CSR you will click on the "ID". once you have the CSR you have to take it to your CA and get it signed. Incase you have root CA and intermediate CA in that case you must have to enroll both of them as mentioned in PKI.
there is a cisco tac video uploaded for the anyconnect with cert here might find you useful
https://www.youtube.com/watch?v=ZZRVAFcSZCA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2021 04:30 AM
Yeah, this was the second of 10 different attempts I tried. It should be noted that only Self-signing has worked on the device, and this is unacceptable.
I get a different error when doing manual. Something to the effect that another certificate exists and reenrolling is necessary. I've legitimately left that thing running for over a week with no luck (even did the manual reenroll several times).
Wonder if it's something with that... Maybe I'll have to console in and see if there is some remnant of an identity cert on the box that is holding things up. That's actually an RMA so I don't think it should, but maybe. To clarify, the following has been attempted:
SCEP with Microsoft PKI (preferred) : Failed with "fail to configure Identity Certificate", but downloads CA
SCEP with Cisco ISE: Failed with "fail to configure Identity Certificate", doesn't download CA
Manual with Microsoft PKI Enrolled certificate: Failed with some error implying another certificate is pending
Self-signed : Works, but is never going to pass implementation reviews
Appreciate the response, and wish it actually would work for me as this could still be PKI and would be along the same implementation as the ASAs so it's not a big deal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2021 04:48 AM
Added note: I'm done working with this. I was able to add the Wildcard from a third party and am calling it quits on this thing. As this gave me the idea, and seeing a CCIE in Sec never use SCEP, I'll mark as Accepted so others can avoid this trap. Maybe next time.
Thanks!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide