- Cisco Community
- Technology and Support
- Security
- VPN
- Can you not simply configure
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to control access from mobile devices?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2016 05:32 PM
If we enable mobile licensing on our ASAs, what can we do to control which VPN users and devices can connect using iOS and Android vs connecting using a PC?
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2016 07:16 PM
You can control that With DAP(Dynamic Access Policy) and Endpoint posture Assessment, so if you want to Only allow Android and Not IOS, you may specify the vendors and so on, You may find an example of all of the options, but right there you can select the OS that should be allow to connect,:
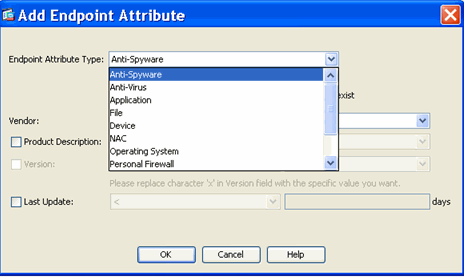
Also, you need to have CSD or Hostscan image in the ASA and enabled so you can get that kind of information from the computers that connects with the AnyConnect.
You can use the AnyConnect image as hostscan image. (remember to enable Endpoint Attributes through ASDM in the CSD section, otherwise this is not going to work).
Please dont forget to rate and mark as correct this post if it helped, keep me posted!
Regards,
David Castro,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2016 08:05 PM
Since some users will have Android and some will have iOS, we cannot restrict by OS. Even if we only chose one OS, that is still too wide of a filter since there are so many people with either or both Android and iOS devices available to them.
Can we restrict by user or by VPN group so that only users who belong to a specific security group can use a mobile device to connect? Can we create a new VPN group just for mobile devices with different access than if the same user connects with their employer provided laptop?
What about restricting specific mobile devices? Can we provide the user with a mobile device and restrict them to only using the device we provide and manage and block the same user from using their unmanaged personal iOS or Android device even if they download and install the same AnyConnect app from their device's app store?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2016 07:07 AM
Answering your questions:
Can we restrict by user or by VPN group so that only users who belong to a specific security group can use a mobile device to connect? Can we create a new VPN group just for mobile devices with different access than if the same user connects with their employer provided laptop?
- You can restrict by group, if you have LDAP enabled, you may see the MemberOf and map the memberOf with the group Policy of the ASA, though I guess the PC users will be the same to connect with the cel phones, so LDAP attribute mapping would not work properly, since the users will be the same. So I can recommend a DAP filtering the devices by the OUI MAC of the vendor, since IOS will have its own OUI and Android, you can use a LUA regular expression, so you may filter with the initial portion of the MAC address:
assert(function ()
local pattern = "^d067\.e5*"
local true_on_match = true
local match = false
for k,v in pairs(endpoint.device.MAC) do
print(k)
match = string.find(k, pattern)
if (match) then
if (true_on_match) then
return true
else return (false)
end
end
end
end)()
- Yes, you can create a new group policy with different access and Posture assessments.
What about restricting specific mobile devices? Can we provide the user with a mobile device and restrict them to only using the device we provide and manage and block the same user from using their unmanaged personal iOS or Android device even if they download and install the same AnyConnect app from their device's app store?
Yes, you can restrict specific mobile devices, but on that case the DAP should be defined to do the posture assessment with a specific text file or registry key in the Cel phones, so the others that try to connect wont be able to replicate the same text file or registry key, and cant connect.
You can restrict that access, though it is way too specific on that occasion, you may configure tunnel-all and Filter the traffic in a web filtering or by ports as well.
Please dont forget to rate and mark as correct this post if it helped, keep me posted!
Regards,
David Castro,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2016 07:30 AM
This still is not clear how we can stop unapproved smartphones from accessing the VPN.
We want only some of our VPN users to be able to use mobile devices to access resources with AnyConnect.
If a different VPN user buys the same model mobile device as the ones approved and goes to the app store and downloads the AnyConnect client app, they still should not be able to be allowed to connect to our VPN. If they use the device we provide to them, only then should they be able to connect.
Can we use device certificates or Meraki to limit which mobile devices can connect? If so, is there anything that can be done to prevent the same device certificate from being used on more than device?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2016 02:07 PM
As mentioned by David you can use DAP to restrict who and what connects to the VPN.
You can specify user attributes as well as the endpoint attributes. Ofcourse this depends a little on what version ASA you are running. I am running version 9.4.
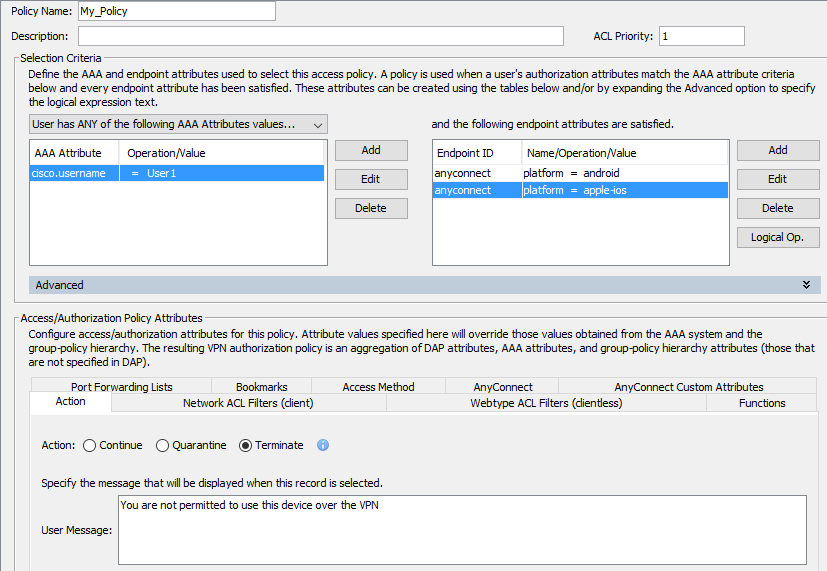
--
Please remember to select a correct answer and rate helpful posts
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2016 11:12 PM
Can you not simply configure connection via the mobile device licensing to only be available to certain users?
We need the default for all users to only be able to connect using a PC license and a limited group of users to be able to use the mobile license to log in.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2016 11:30 PM
I think you are misunderstanding what the license actually does. The license only enables a feature on the ASA, it cannot be used to limit the use of it to a specific group. Limiting the use of the license is additional configuration.
As I mentioned in my previous post you can use DAP to do what you want. There are many more options also, such as limiting connections based on if the user has an up-to-date antivirus, and more.
You can also, specify a RADIUS or LDAP server and then allow deny access based on the AD groups users are a member of.
--
Please remember to select a correct answer and rate helpful posts
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2016 11:50 PM
Some of the settings you refer to seem not applicable to smartphones and mobile OS tablets. There is not going to be antivirus or firewall on iOS and Android devices. Filtering by mobile OS (Android or iOS) is also very ineffective. What can we use that would recognize a specific smartphone or iPad that we have preapproved vs any random mobile device the user buys that happens to match the allowed Android or iOS version?
We already have LDAP to manage which users can use VPN and what network access they have after connecting.
What we need to do now is configure this with more granularity so of the users who are allowed to use VPN, we need to further filter which of those allowed users can use both mobile devices and PCs vs which of those users who can only use PCs to connect to the VPN.
.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2016 12:03 AM
Again, DAP will do what you are looking for! You can choose the platform type, define the platform version/s and device type. Here I am just showing Apple iOS but i assure you that you can also select Android
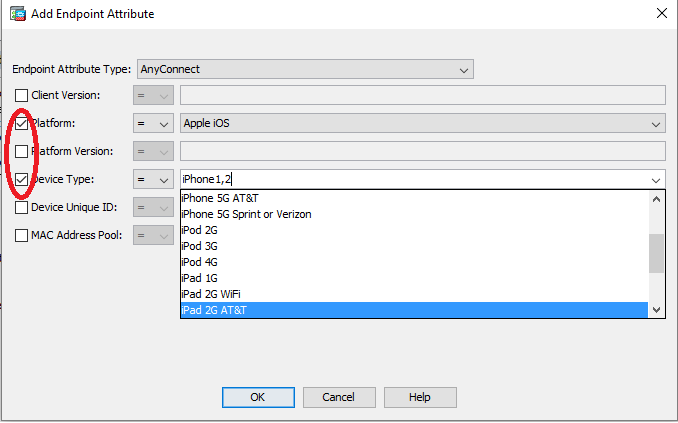
--
Please remember to select a correct answer and rate helpful posts
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2017 06:45 AM
Hi Community, I have the similar goal - controlling mobile device connected to ASA firewall.
I understand I can use DAP (Dynamic Access Policy). But I want to allow only company provided devices to use VPN AnyConnect client.
All comapny mobile devices have the same MDM(mobiole device management) profiles installed on them.
Do you know a rule in DAP I can create to check for MDM installed on mobile devices?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2017 08:09 AM
Use Identity Services Engine (ISE) for that.
ISE (with Apex licensing) integrates with many MDM solutions via API and can use their MDM enrollment and compliance status as a condition in determining endpoint authorization policy that should be applied.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2017 11:01 AM
Does ISE require purchausing a license or is it a free feature?
I haven't used this before.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2017 05:31 AM
ISE is a separate product requiring its own server (or set of servers in a large deployment) and licensing. It provide context-based network access control with a very rich set of features for wired, wireless and VPN users and devices.
https://www.cisco.com/c/en/us/products/security/identity-services-engine/index.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2017 12:37 AM
thank you for suggestion. Unfortunatelly we can't invest into new product. So, we ended up by disabling VPN on mobile devices using "OS check " policy for most of the users.
Now, we want to control domain joined MacBooks and Linux machines. Is there any regsitry or file we can check if MacBook or Linux on windows domain?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



