- Cisco Community
- Technology and Support
- Security
- VPN
- Hi Sam,It`s no problem at all
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ipsec ikev2 vpn microsoft CA problem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2014 03:52 AM - edited 02-21-2020 07:36 PM
Hi guys
Have been searching for a few days now and not been able to find the answer to my issue.
I've been given requirements to create an IPSec Ikev2 vpn using internal microsoft PKI (not digicert etc, but corporate), with windows 7 clients, cisco anyconnect mobile client, to access internal resources from external networks.
So far it's all working except that the client does not accept the certificate for its intended purpose as you can see in the image below.
The ID cert on the ASA has been installed from Microsoft PKI, and it has the root certificate installed on the ASA.
The root certificate is also installed in the win7 client's trusted root certificate store for both user and machine.
The PKI root CA is windows server 2003.
The requirements for IKEv2 certificates fulfilled in the ID cert (digital sig, key encipher, EKU for server auth) and have even made a new template with ALL EKU values with no difference.
I know a bit about certificates and have made sure that the root cert is installed in both the user store and machine store.
There is no issue with trusting the chain as far as I can see since opening a web page to the ASA am able to see the certificate and the chain with no issues.
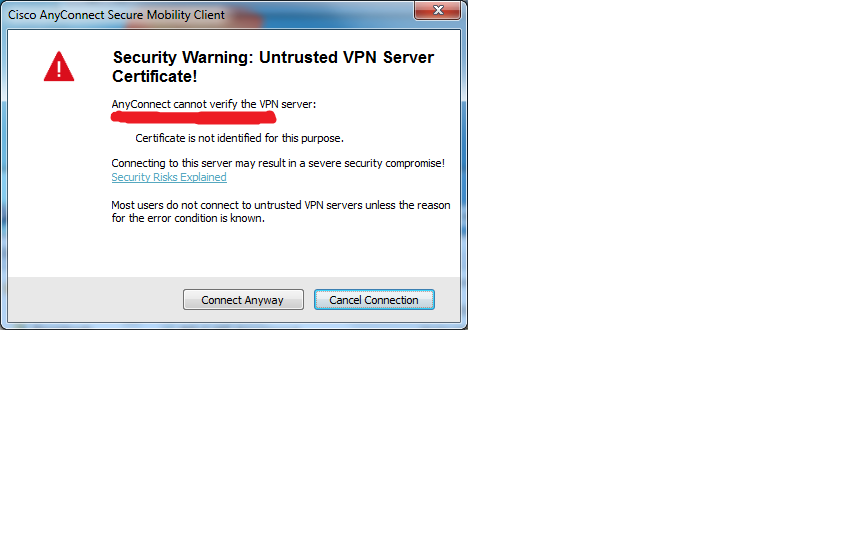
I'd be extremely grateful if anyone has any suggestions on what to try, before I goto TAC with this.
Cheers loads,
Sam
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2014 07:40 AM
It might well have been the reload that was necessary to upgrade (as opposed to the upgrade itself) that caused things to start working. I have seen other devices (Cisco ACE) require at least a warm reload when changing certificate-related parameters.
What was your old and what is the new version?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2014 07:46 AM
Hi,
I'm not sure am allowed to state version usage publicly, but we have another ASA built the same as the other with the old version still running. When we come to migrate that (soon) I'll find out if it has the same issues, first do a warm reload and then upgrade version if it didn't work.
Thanks
Sam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2015 12:12 PM
You're right on Marvin, On ASA ver 8.4 (2) I receive this same error "failed to update pki session with ikev2 trustpoint" after changing identity certs for Clientless SSL. It seems to yield this error regardless of the type of CA used, whether or not it includes the "server authenticatio" eku, as I was able to duplicate this behavior after issuing from a MS 2012 R2 CA and an IOS CA. After rebooting the ASA it's fine with the cert and everything works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2015 12:14 PM
You're right on Marvin, On ASA ver 8.4 (2) I receive this same error "failed to update pki session with ikev2 trustpoint" after changing identity certs for Clientless SSL. It seems to yield this error regardless of the type of CA used, as I was able to duplicate this behavior after issuing from a MS 2012 R2 CA and an IOS CA. It also doesn't seem to matter whether the eku "Server Authentication" is there or not (at least for Clientless Remote Access). After rebooting the ASA it's fine with the newly selected cert and everything works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2014 09:15 PM
Hi Sam,
I am labbing this so I can conclude what`s missing but I believe you are not enrolling correctly with the asa with the CA. Also, for Java applications such as any connect and the asdm you have to use a code certificate what means something is missing anyways. So far my any connect presents me with the correct trusted certificate. I`ll let u know when I am finished.
BR,
Bruno Silva.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2014 01:25 AM
wow you guys are going to loads of trouble for this, thanks loads.
I'll have another look at enrolling: but doing it again yesterday it didn't moan about the enrollment when adding the CA certificate..
Cheers
Sam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2014 04:24 AM
Hi Sam,
It`s no problem at all, I am also having certificate issues but concerns another area of expertise involving SCEP auto-enrollment. For some reason I think the problems are almost the same because when I authenticate using the new certificate it seems to be impossible to match the certificate properly and then it enrolls to a new certificate, it`s really giving me a hard time on solving it and I can`t find a way to match it. As per the certificate you are telling I am pretty sure it`s something related to the enrollment. When you enroll to this type of thing, you need to enroll in 3 different trust points for 3 different areas, the internal certificate, the SSL validation and the Code signer. The first is for the ASA itself, the second for the SSL vpn and the last for java applications such as any connect and ASDM. I am simulating, as soon as I get a proper conclusion I`ll let you know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2014 07:51 AM
OK Great thanks again Bruno I'm still trying different things I'll let you know if there's any more info.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2014 05:14 AM
Hi Sam,
When you check the Anyconnect configurations, does it show the correct certificate being used?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2014 05:20 AM
Hi Bruno,
I've created quite a few certificates from various templates and have been trying with this for a while: when I change the certificate under the Anyconnect configuration, I can see from trying from a web browser that the certificate has changed.
Templates I've used are ipsec, computer, web server and as far as I'm aware, web server should just work with very little configuration...
Thanks :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2014 05:22 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2014 03:58 AM
Hi Sam,
How many certificate trust points you have on the asa?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2014 04:02 AM
Hi,
Quite a few at the moment: testing between quite a few ID certificates, and two different PKI servers so there are a few trustpoints to choose from. When the client certificate is shown to the ASA by the anyconnect client, it is able to validate that certificate by a trustpoint.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

