- Cisco Community
- Technology and Support
- Security
- VPN
- IPsec Overlaps netowork with nat overload to internet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPsec Overlaps netowork with nat overload to internet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2016 05:23 PM - edited 02-21-2020 09:05 PM
Hello, Guys..
I have a doubt regarding a scenario that I built in the Unet Lab.
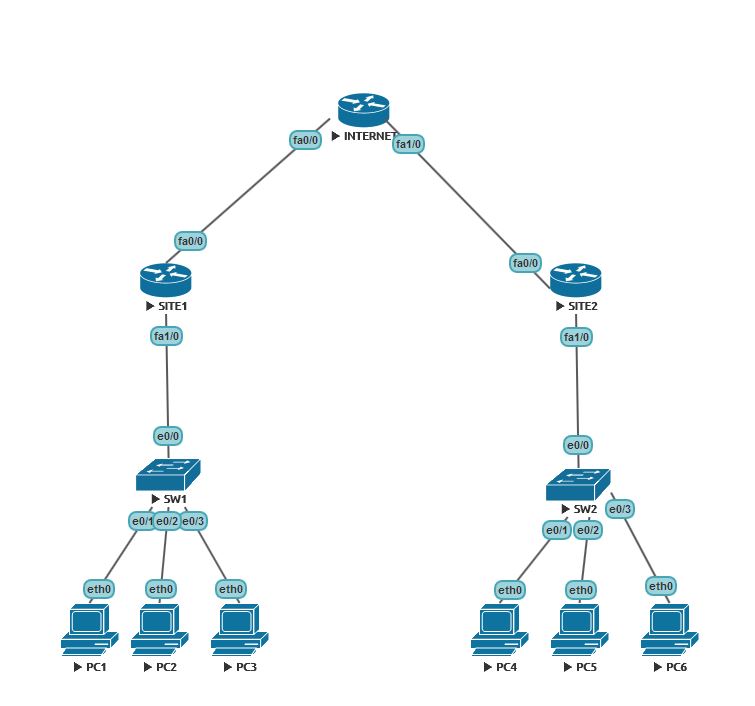
The image I have 2 Sites in a company: the LAN site 1 is 192.168.0.0/24 and the LAN 2 site is 192.168.0.0/16. I can successfully establish a VPN between the two site as evidence:
SITE 1:
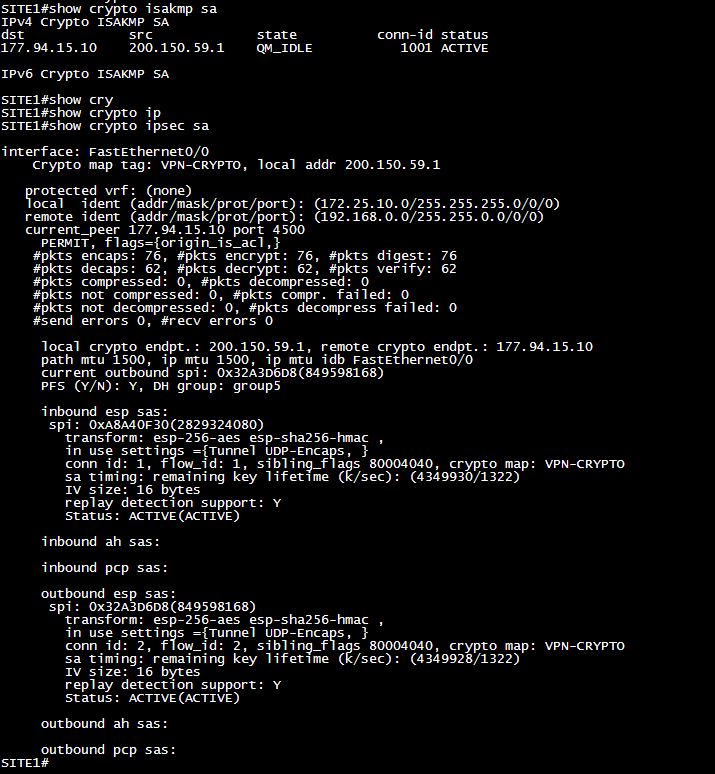
SITE 2:
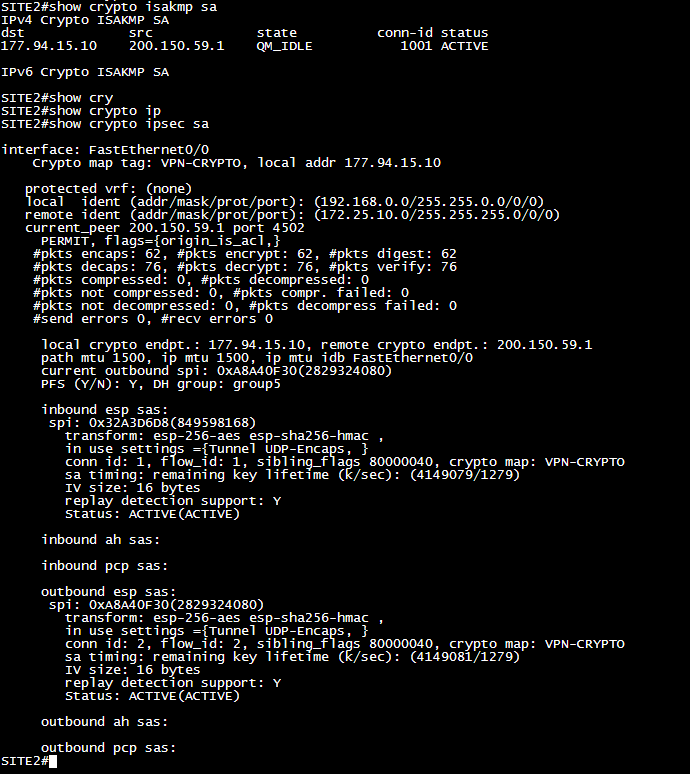
The main problem here is that I can't get out to the internet even with the NAT configuration correct. If I remove the NAT configuration used for the VPN, access to internet works normal, but the VPN crashes. Have any other strategy I can both access the internet as access resources of another site through the VPN?
The router of the two site are attached.
Thank you in advance!
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2016 02:43 AM
01. You have to create ACL permit and apply into the crypto map of internet interface .
----------------------------------------------------------------------------------------------------------------------
Configure the access-lists and map them to the Crypto map configured.
access-list 100 remark IPSec Rule
access-list 100 permit ip LANSITE1NW+Wildcardmask LANSITE2NW+Wildcardmask
Crypto map S2SVPN_1 ipsec-isakmp
set peer 177.94.X.X
set transform-set Router-IPSEC
match address 100
interface FastEthernet0
ip address 200.150.X.X
duplex auto
speed auto
crypto map S2SVPN_1
02. configure nat to allow the inside network to access internet
------------------------------------------------------------------------------
ip nat inside source route-map nonat interface fa0/0 overload
-------------------------------------------------------------------------------------------
-----------------------------------------------------------------------------------------------------
This ACL 110 identifies the traffic flows using route map
access-list 110 deny ip LANSITE1NW+Wildcardmask LANSITE2NW+Wildcardmask
access-list 110 permit ip LANSITE1NW+Wildcardmask any
route-map nonat permit 10
match ip address 110
----------------------------------------------------------------------------------------------------------
i hope this will help you.
Thanks,
Mani
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2016 04:48 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2016 10:07 AM
Hi ,
1. you have to remove
no ip nat inside source static network 192.168.0.0 172.25.10.0 /24
no ip nat outside source static network 192.168.0.0 10.199.0.0 /16
---------------------------------------------------------
2.change ACL at site 1 because you local Nw 192.168.0.0 and remote nw 172.25.10.0
#ip access-list extended NONAT
deny ip 192.168.0.0 0.0.255.255 172.25.10.0 0.0.0.255
permit ip 192.168.0.0 0.0.0.255 any
# ip access-list extended VPN-CRYPTO
permit ip 192.168.0.0 0.0.255.255 172.25.10.0 0.0.0.255
-----------------------------------------------------------------------------------
3. at site2 ACL should be
#ip access-list extended NONAT
deny ip 172.25.10.0 0.0.0.255 192.168.0.0 0.0.255.255
permit ip 172.25.10.0 0.0.0.255 any
# ip access-list extended VPN-CRYPTO
permit ip 172.25.10.0 0.0.0.255 192.168.0.0 0.0.255.255
-----------------------------------------------
4. clear isakmp - phase 1
#clear crypto isakmp
------------------------------
5. clear ipsec - phase 2
# clear crypto sa
------------------------
6. initate traffic from site1 to site2
# ping 172.25.10.X source 192.168.X.X
check the crypto isakmp & then ipsec inbound and outbound .
---------------------------------------------------------
7. site1 internal users will be able to access internet as well.
please give me rate if this helps you.
thanks ,
Mani
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2016 03:21 PM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide