- Cisco Community
- Technology and Support
- Security
- VPN
- IPSec with Dynamic routing- Explanation
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2023 11:27 PM
Hi Guys,
Need some clarification on this.
Some cisco docs say IPSec cannot work with dynamic routing as it only supports unicast traffic.
Some documents say that it can using VTI's can anyone elaborate this, please?
Thanks
Solved! Go to Solution.
- Labels:
-
IPSEC
-
Remote Access
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2023 01:39 AM
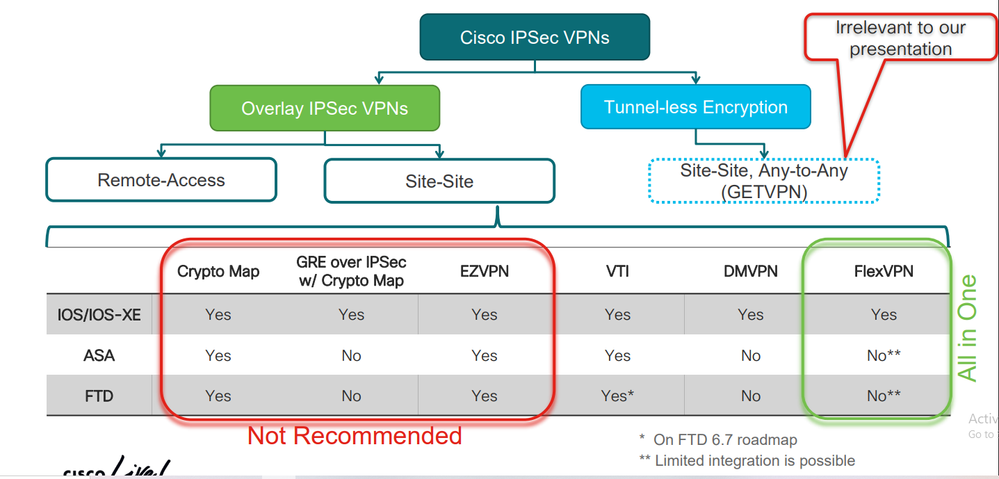
Policy Based VPNs have been around longer and have wider support on the hardware/software. Route Based VPNs (static VTIs) have only been supported on Cisco ASA since version 9.7 and FTD since 6.7 and only last year in version ASA 9.19 and FTD 7.3 did Cisco introduce Dynamic VTI functionality. Cisco routers have the widest support for VPNs, although crypto maps are depreciated from 17.6.6. Route Based VPNs are the preferred type of VPN to deploy.
Policy Based and Route Based VPN are standards of VPN supported by vendors, not just Cisco.
Policy Based VPNs might be preferred in smaller environments or less complex environments which do not use a routing protocol. Personal preference of the network administrator configuring the VPN might influence the design.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2023 01:21 AM - edited 03-17-2023 03:22 AM
@nwekechampion a Policy Based VPN does not support multicast and will not allow you to run a routing protocol, however a Route Based VPN using a VTI/DVTI/GRE over IPSec VPN supports multicast and allows you to run a dynamic routing protocol over an IPSec VPN tunnel.
Cisco Routers and ASA/FTD firewalls support both Policy and Route Based VPNs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2023 11:59 PM
Thanks @Rob Ingram ,
So why does anyone even bother to use Policy based VPN if it has this obvious limitation?
What are the use cases for Policy-based VPN?
Why did Cisco use/support policy based vpns in the first place?
What is it about policy based vpn that makes it incompatible with Dynamic routing (multicast)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2023 01:39 AM
Policy Based VPNs have been around longer and have wider support on the hardware/software. Route Based VPNs (static VTIs) have only been supported on Cisco ASA since version 9.7 and FTD since 6.7 and only last year in version ASA 9.19 and FTD 7.3 did Cisco introduce Dynamic VTI functionality. Cisco routers have the widest support for VPNs, although crypto maps are depreciated from 17.6.6. Route Based VPNs are the preferred type of VPN to deploy.
Policy Based and Route Based VPN are standards of VPN supported by vendors, not just Cisco.
Policy Based VPNs might be preferred in smaller environments or less complex environments which do not use a routing protocol. Personal preference of the network administrator configuring the VPN might influence the design.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2023 03:49 AM
the timeline
IPSec support only unicast not multicast so it can not support Dynamic routing
GRE/IPSec solve the problem of multicast so now we can run dynamic routing with GRE/IPsec but this give more overhead to packet
VTI which build on pure IPsec support both unicast and multicast and hence it can use for dynamic routing
you have these three option select one of them depend on your platform
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2023 12:01 AM
@Thankds @MHM Cisco World ,
Why did Cisco use/support policy based vpns in the first place?
Would there be an obvious use case for policy-based VPN?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2023 03:28 AM - edited 03-19-2023 04:33 AM
IPSec is old and wide used by all vendor,
which one is simple in config ? IPsec for P2P sure simple than VTI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2023 05:29 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2023 04:46 AM - edited 03-20-2023 04:47 AM
Hzllo @nwekechampion
Traditionally, IPSec VPNs have been configured using point-to-point tunnels, where each tunnel is manually configured between two endpoints. In this scenario, dynamic routing protocols cannot be used because the routing updates are broadcast or multicast traffic, and IPSec only supports unicast traffic.
However, with the introduction of Virtual Tunnel Interfaces [VTI], IPSec can be used with dynamic routing protocols. VTI allows IPSec to be configured as a virtual interface that supports dynamic routing, effectively eliminating the need for point-to-point tunnels.
With VTI, IPSec can be configured to encrypt traffic between two endpoints, while still allowing the use of dynamic routing protocols to exchange routing information between the endpoints. VTI works by creating a virtual interface that can be assigned an IP address and configured with routing information, just like a physical interface.
.ı|ı.ı|ı. If This Helps, Please Rate .ı|ı.ı|ı.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2023 09:51 PM - edited 03-25-2023 09:57 PM
Thanks for clarifying guys.
you have all been very helpful.
Really appreciate it.
Does anyone have any documentation that fully explains how VTI works under the hood?
Also do Vendors like Palo use VTIs for ipsec under the hood, as Plao altos seem to ipsec seem to be able to support dynamic routing. If they dont, how does it work on their platform?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide