- Cisco Community
- Technology and Support
- Security
- VPN
- LAN-to-LAN VPN between Cisco Router and Cisco ASA issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2017 02:32 AM
Hello.
We have some braches, connected with head office via VPN IPSec, as shown at schema below:
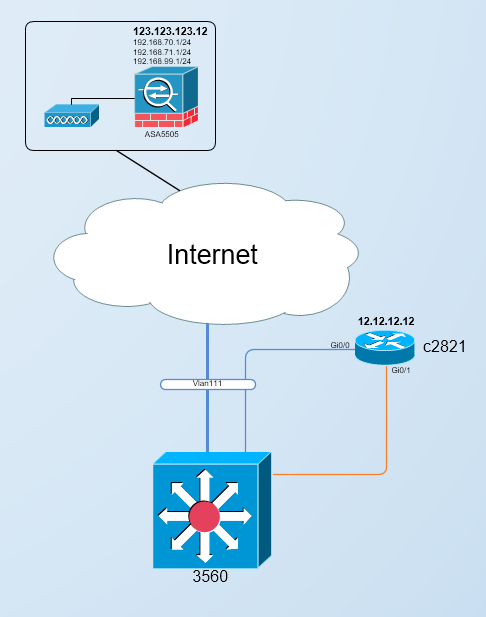
c2821 configured as:
!
crypto keyring SPOKES
pre-shared-key address 0.0.0.0 0.0.0.0 key vpn_key
!
crypto isakmp policy 2
hash md5
authentication pre-share
lifetime 3600
!
crypto isakmp policy 15
encr aes 256
authentication pre-share
group 5
!
crypto isakmp policy 20
encr aes 256
authentication pre-share
group 2
crypto isakmp keepalive 10 periodic
crypto isakmp profile L2L
description LAN-to-LAN for spoke router(s) connection
keyring SPOKES
match identity address 0.0.0.0
crypto ipsec security-association lifetime seconds 28800
!
crypto ipsec transform-set ESP-AES-256-SHA esp-aes 256 esp-sha-hmac
!
crypto dynamic-map VPN 10
set transform-set ESP-AES-256-SHA
set isakmp-profile L2L
reverse-route
!
crypto map VPN 11 ipsec-isakmp dynamic VPN
!
interface GigabitEthernet0/0
ip address 12.12.12.12 255.255.255.240
crypto map VPN
!
Cisco ASA's configured as:
object network branch_localnet
subnet 192.168.70.0 255.255.255.0
subnet 192.168.71.0 255.255.255.0
object-group network head_office_localnet
network-object 192.168.146.0 255.255.255.0
network-object 192.168.150.0 255.255.254.0
network-object 192.168.158.0 255.255.255.0
network-object 192.168.159.0 255.255.255.0
network-object 192.168.162.0 255.255.255.0
network-object 192.168.163.0 255.255.255.0
network-object 192.168.164.0 255.255.255.0
network-object 192.168.165.0 255.255.255.0
network-object 192.168.166.0 255.255.255.0
network-object 192.168.167.0 255.255.255.0
network-object 192.168.168.0 255.255.255.0
network-object 192.168.169.0 255.255.255.0
access-list vpn extended permit ip object branch_localnet object-group head_office_localnet
nat (inside,outside) source static branch_localnet branch_localnet destination static head_office_localnet head_office_localnet no-proxy-arp route-lookup
!
object network obj_any
nat (any,outside) dynamic interface
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map vpn_m 10 match address vpn
crypto map vpn_m 10 set peer 12.12.12.12
crypto map vpn_m 10 set ikev1 transform-set ESP-AES-256-SHA
crypto map vpn_m interface outside
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
So, VPN works, but I see some issue: I can't connect from head office to branch localnet, until something from localnet not trying to connect to this network. Some examples:
I try to ping resource 192.168.70.12 from network 192.168.146.134 - it doesn't works.
But when I started ping 192.168.146.0/24 network from 192.168.70.0/24 network, ping resource 192.168.70.12 from network 192.168.146.134 started work.
When I tried to debug ipsec inside Cisco ASA branch and found next:
asa# IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=1, saddr=192.168.70.134, sport=256, daddr=192.168.146.1, dport=256
IPSEC(crypto_map_check)-3: Checking crypto map vpn_m 10: matched.
Feb 10 10:24:25 [IKE COMMON DEBUG]Tunnel Manager dispatching a KEY_ACQUIRE message to IKEv1. Map Tag = vpn_m. Map Sequence Number = 10.
Feb 10 10:24:25 [IKE COMMON DEBUG]IKEv2 Doesn't have a proposal specified
IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=1, saddr=192.168.70.134, sport=256, daddr=192.168.146.1, dport=256
IPSEC(crypto_map_check)-3: Checking crypto map vpn_m 10: matched.
IPSEC: Received a PFKey message from IKE
IPSEC: Parsing PFKey GETSPI message
IPSEC: Creating IPsec SA
IPSEC: Getting the inbound SPI
IPSEC: New embryonic SA created @ 0xcda86e40,
SCB: 0xCDA71EE8,
Direction: inbound
SPI : 0x939F8D80
Session ID: 0x03695000
VPIF num : 0x00000003
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
IPSEC: Received a PFKey message from IKE
IPSEC: Parsing PFKey ADD message
IPSEC: Creating IPsec SA
IPSEC: Received a PFKey message from IKE
IPSEC: Parsing PFKey UPDATE message
IPSEC: Creating IPsec SA
Feb 10 10:24:25 [IKE COMMON DEBUG]IKEv1 was successful at setting up a tunnel. Map Tag = vpn_m. Map Sequence Number = 10.
Feb 10 10:24:25 [IKE COMMON DEBUG]Tunnel Manager Removed entry. Map Tag = vpn_m. Map Sequence Number = 10.
asa# IPSEC: Received a PFKey message from IKE
asa# IPSEC: Received a PFKey message from IKE
After that I can connect from head's network 192.168.146.0/24 to branch network 192.168.70.0/24. As I undestand, Cisco ASA (as initiator) not create SA for all object, defined in crypto map match access-list?
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2017 12:42 AM
The router is configured with a dynamic crypto map, rather than a static site to site crypto map. As such it can only "answer" incoming VPNs, and not initiate VPNs out.
That is why your outbound ping does not work (router can't make VPN out) until a ping has happened the other way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2017 12:42 AM
The router is configured with a dynamic crypto map, rather than a static site to site crypto map. As such it can only "answer" incoming VPNs, and not initiate VPNs out.
That is why your outbound ping does not work (router can't make VPN out) until a ping has happened the other way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2017 03:34 AM
Thanks for reply, Philip.
Dynamic map - is very good when you have more than 2 remote peer, so apparently will have to decide this issue by other method.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2017 07:03 AM
Philip is correct that what you describe is the expected behavior when you use a dynamic map on the router. So you have a choice to make. You can choose the convenience of the dynamic map so that there are multiple remote peers but not multiple map entries and with that choice is the restriction that you can only initiate the VPN from the remote. Or you can choose to have individual map entries for multiple remote peers and in that case you can initiate the VPN from either end. So you have a choice to make.
HTH
Rick
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide