- Cisco Community
- Technology and Support
- Security
- VPN
- PPTP VPN on Cisco 2921 ISR G2
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
PPTP VPN on Cisco 2921 ISR G2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2014 06:48 AM
Hi,
I need to configure PPTP VPN in the following simple scenario:
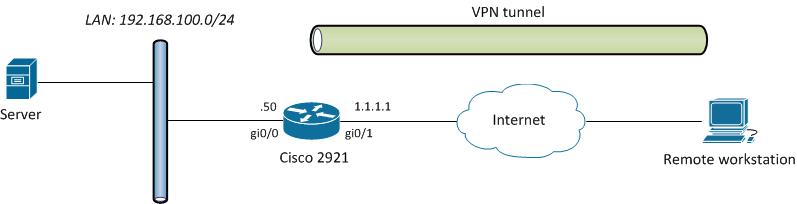
Remote workstation needs access to a server in LAN. There is a condition and I can't use IPsec (there are some servers inside LAN and NAT static translations are configured for them).
I configured PPTP according the steps on cisco.com, but in fact i have connectivity only to internal interface of Cisco2921. Not the network. I can ping Gi0/0 from remote workstation but can't ping Server.
Here is the part of config:
vpdn enable
vpdn-group 1
accept-dialin
protocol pptp
virtual-template 1
exit
exit
ip local pool REMOTE_VPN_USERS 192.168.100.100 192.168.100.110
interface virtual-template 1
encapsulation ppp
peer default ip address pool REMOTE_VPN_USERS
ip unnumbered gi0/0
no keepalive
ppp encrypt mppe auto
ppp authentication ms-chap-v2 eap
The final aim is to gain access to remote servers e.g. via RDP. Would appreciate for your help.
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2014 09:57 AM
Hello, Alexander.
I guess you are pinging G0/0 because it's installed on remote client as peer-address for the tunnel.
I'm not sure, but guess that remote client has no route over the tunnel (for MS Windows, it's a special checkbox under TCP/IP) for the remote subnet.
PS: EasyVPN allows to encapsulate IPSec into UDP and TCP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2014 09:30 PM
VV, thanks for reply
But how should I tune the tunnel in order this route to be installed automatically? Is it possible? I need this solution to be as simple as possible.
Basically I considered using EasyVPN as an option, but after discovering that it's using an IPsec (means with ESP) I thought that i can't use it (because of static translations mentioned above). Could EasyVPN serve as workaround for this problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2014 09:50 PM
Hello, Alexanger.
Try examine "route print" on your Windows client to see actual routing table.
How to tune routing on VPN - see Configuring Routing on a VPN Client (Microsoft).
EasyVPN supports UDP and TCP encapsulation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2014 11:07 PM
I've checked: route to 192.168.100.0/24 is present at the remote workstation. I've tried both tick and untick the checkbox but result is the same.
The server inside the LAN works good with IPsec clients through the tunnel terminated on another device on the same LAN. That's why i excluded it from troubleshooting.
Any more ideas about PPTP ?
P.S. I've started to discover EasyVPN tuning.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2014 11:47 PM
Hello, Alexander.
I guess there could be an issue on your LAN routing.
Could you try to trace clients' IP-address from the server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2014 04:25 AM
Yeah,
here it is (client ip is 192.168.100.102):
Tracing route to 192.168.100.102 over a maximum of 30 hops
1 1 ms <1 ms <1 ms 192.168.100.50
2 * * * Request timed out.
3 * * * Request timed out.
and so on
This router also performs PAT for 192.168.100.0/24. I'm not sure.. could it be the reason?
ip access-list standard LAN
permit 192.168.100.0 0.0.0.255
deny any
route-map NAT_WAN1 permit 10
match ip address LAN
match interface GigabitEthernet0/1
Maybe NAT process is performed earlier than traffic is encrypted and send off the tunnel??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 04:10 AM
Basically, routing seems good: default routes in one direction (with PAT) and static translations in back direction. Nothing complicated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2014 07:22 AM
Could you share the links (if you remember any) to materials, where EasyVPN encapsulation is mentioned? I would greatly appreciate it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2014 07:33 AM
Yeah! It seems i've found it! Cisco Tunnel Control Protocol (cTCP)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide