- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2016 03:23 AM
Hi,
today I have installed a new certificate for SSL Vpn on my Cisco ASA.
I followed the configuration steps: generate a new rsa key, send it to the CA authority and then install the certificate associated to the truspoint.
Below you can see the result after the installation process; I have two ASDM_Truspoint6, one still pending.
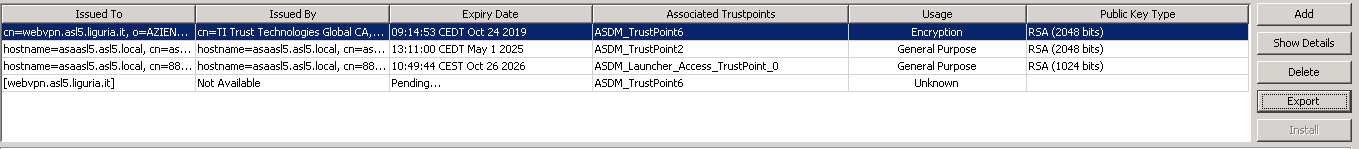
I tried to bind the certificate with the outside interface but I still receive a certificate error on the browser.
How can I fix this problem?
Many thanks,
Maury
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2016 09:25 AM
Hi Maury,
This certificate you are getting from you CA see to have an Encryption usage, can you get a certificate with General Purpose usage. *this is not something that you can do on the ASA, the certificate needs to be recreated with a General Purpose usage.
I tried to reproduce the issue with the same 8.2.5 version with a General Purpose cert and everything works.
Hope this info helps!!
Rate if helps you!!
-JP-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2016 05:44 AM
Hi m.pederneschi,
Which version of ASA are you running?
Hope this info helps!!
Rate if helps you!!
-JP-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2016 05:53 AM
Hi JP Miranda Z,
thanks for answering.
Below the version:
Cisco Adaptive Security Appliance Software Version 8.2(5)
Device Manager Version 7.3(2)102
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2016 05:56 AM
Can you share the following command:
sh run all ssl
How are you testing the certificate (AnyConnect or Webvpn)?
Hope this info helps!!
Rate if helps you!!
-JP-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2016 06:07 AM
Below the output requested:
asaasl5/pri/actNoFailover# show run all ssl
ssl server-version any
ssl client-version any
ssl encryption 3des-sha1 aes128-sha1 aes256-sha1 des-sha1 rc4-md5
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 outside vpnlb-ip
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 outside
I'm testing the certificate trough webvpn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2016 06:17 AM
As per the image attached before with the certificates, you don't have the right certificate applied to the outside interface, changing the cert to the ASDM_Truspoint6 everything should work fine, you can use the following commands:
no ssl trust-point ASDM_Launcher_Access_TrustPoint_0 outside vpnlb-ip
no ssl trust-point ASDM_Launcher_Access_TrustPoint_0 outside
ssl trust-point ASDM_Truspoint6 outside
Hope this info helps!!
Rate if helps you!!
-JP-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2016 06:26 AM
I try to change the trustpoint associated to the outside interface but nothing change.
Look at this output:
asaasl5/pri/actNoFailover# show crypto ca certificates ASDM_TrustPoint6
Certificate
Status: Available
Certificate Serial Number: xxxxxx
Certificate Usage: Encryption
Public Key Type: RSA (2048 bits)
Signature Algorithm: SHA256 with RSA Encryption
Issuer Name:
cn=TI Trust Technologies Global CA
ou=Servizi di certificazione
o=Telecom Italia Trust Technologies S.r.l.
c=IT
Subject Name:
cn=webvpn.xx.xxxx.it
o=xxxx
l=xxx
c=xx
st=xx
OCSP AIA:
URL: http://ocsp.tipki.it
CRL Distribution Points:
[1] http://ca.tipki.it/TTGlobalCA/CRL
Validity Date:
start date: 09:14:53 CEDT Oct 24 2016
end date: 09:14:53 CEDT Oct 24 2019
Associated Trustpoints: ASDM_TrustPoint6
Certificate
Subject Name:
Name: webvpn.asl5.liguria.it
Status: Pending terminal enrollment
Key Usage: General Purpose
Fingerprint: b32e9c47 0843870a 94644d2a d0b7500a
Associated Trustpoint: ASDM_TrustPoint6
asaasl5/pri/actNoFailover#
I was expecting that the second certificate would have disappeared after the installation of the certificate. But it remain in 'pending terminal enrollment'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2016 06:32 PM
Can you share the sh run all ssl again, if you are having a problem with a stuck trustpoint remove both and do the whole process again, you don't need to request the cert again since you can select the same RSA key and try again.
Hope this info helps!!
Rate if helps you!!
-JP-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2016 01:18 AM
Below the 'show run all ssl' output:
asaasl5/pri/actNoFailover# show run all ssl
ssl server-version any
ssl client-version any
ssl encryption 3des-sha1 aes128-sha1 aes256-sha1 des-sha1 rc4-md5
ssl trust-point ASDM_TrustPoint6 outside
How can I use the same RSA key if I delete both the certificate? There's a way to specify the RSA avoiding the automatic generation?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2016 07:29 AM
Hi m.pederneschi,
Before removing the cert, do you have the full certificate chain including the Root cert? if yes you can regenerate the CSR and install the cert again using the same RSA key:

You can select the key where says keypair.
Hope this info helps!!
Rate if helps you!!
-JP-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2016 08:03 AM
Hi,
thank you for help me. I'm a little bit confused about the procedure to remove and install again the certificate.
I have the root cert and the full certificate chain. I have installed them in the "CA Certificates", is that right?
Thanks again,
Maury
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2016 08:38 AM
Maury,
That is correct you need the full chain in order to have this working properly, now you can only delete the identity certificate and create a CSR again with the same keypair you used before but at this time you don' t need to request a new certificate because you already have it.
So just delete the certificate, create a new CSR using the same keypair you used before and over that CSR request install the certificate again.
Hope this info helps!!
Rate if helps you!!
-JP-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2016 09:06 AM
I tried to delete the identity certificate and create the new csr selecting the same rsa key I used before.
I install the certificate again but the results is the same as before.


- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2016 09:25 AM
Hi Maury,
This certificate you are getting from you CA see to have an Encryption usage, can you get a certificate with General Purpose usage. *this is not something that you can do on the ASA, the certificate needs to be recreated with a General Purpose usage.
I tried to reproduce the issue with the same 8.2.5 version with a General Purpose cert and everything works.
Hope this info helps!!
Rate if helps you!!
-JP-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2016 03:49 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

