- Cisco Community
- Technology and Support
- Security
- VPN
- PSK for IKEv2 not persistent
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
PSK for IKEv2 not persistent
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2024 07:00 AM
Hi all,
We are planning to replace ASA 5525 with virtualized ASA on Firepower. While checking the configuration which we restored from our running ASA(which contains a folder named VPNPresharedKeys with a single file for each VPN profile), we noticed PSK for IKEv2 is not persistent, it is missing from Crypto map Entry.
As the equipment is not yet in place, there are no active VPNs.
Is this a normal behavior until we connect it to the internet and the PSK will persist once the tunnels will negotiate?
Anyone stumbled in to this so far?
Thank you!
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2024 07:05 AM - edited 04-04-2024 01:38 AM
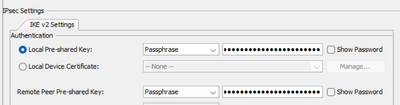
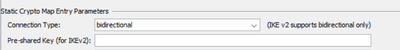
@IulianaNegura EDIT: you can configure the PSK either under the connection profile/tunnel-group or under the crypto map sequence for that peer.
crypto map outside_map2 1 match address outside_cryptomap
crypto map outside_map2 1 set peer 2.2.2.1
crypto map outside_map2 1 set ikev2 pre-shared-key **********
!
tunnel-group 2.2.2.1 ipsec-attributes
ikev2 local-authentication pre-shared-key **********
ikev2 remote-authentication pre-shared-key **********
Typically the PSK is configured just under the tunnel-group/connection profile and not under the crypto map, so that should not be a problem that the PSK is not configured under the crypto map.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2024 09:05 AM
As I see there is PSK for local and remote peer auth.
And in cli we config it under the tunnel group
This second field (empty) I will check for what it used.
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide