- Cisco Community
- Technology and Support
- Security
- VPN
- Re: RA VPN configuration in FDM with Azure AD certification issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RA VPN configuration in FDM with Azure AD certification issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2022 02:06 AM
Hi,
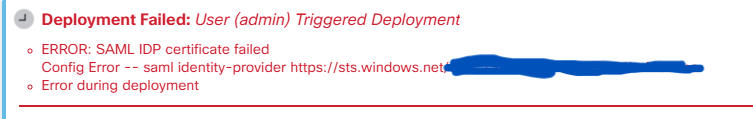
I try to configure RAVPN using Azure AD SSO in FDM. When I download Microsoft original certificate to configurate, I got the following error.
When I use self signed certificate, it can configure successfully but not able to connect from Anyconnect client due to untrusted site problem.
Is anyone can configure using Microsoft certificate?
Banny
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 03:38 PM
Hi @banny.chim,
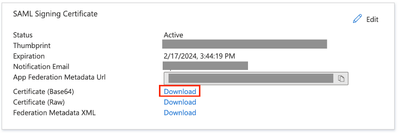
To me, it loooks like you haven't imported or configured certificate that you must download from Azure app (or to upload it, if you create it offline). This certificate is used for communication between FTD and Azure. You have to download it from Azure side and import it under Objects / PKI.
You can use Duo config guide for this, and use parts which are relevant to you.
You can use certificate generated on your own, but you must configure that certificate on Azure side as well. Using self-signed certificate which is not configured on Azure side will give you this result - you can configure it on FTD, but it will not work.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2022 12:24 AM
Hi Milos,
In the beginning, I following this tutorial. https://docs.microsoft.com/en-us/azure/active-directory/saas-apps/cisco-anyconnect
Download certificate and import to using FDM.
And setup everything in FTD using FDM. When I deploy, I got the error I posted in original message. Then I guess it is certificate issue. Then I use XCA to generate my own certificate and update to AZURE AD and in my Firepower 1010. It deploy successfully. When I connect to https://<MyVPNIP> the browser prompt me for non-trusted certificate and ask me to manually accept. After I accept, I can login to https://<MyVPNIP> by Azure AD.
When I try to connect using AnyConnect client. When I select the VPN profile which using Azure AD to authenticate, the client show a page say this is an non-trusted site and not allow me to accept to continuous login. It is disconnect me.
I think my main problem it how to ask AnyConnect client to accept my XCA self signed certificate.
Banny
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2022 12:07 PM
Hi Banny,
Just because you are getting untrusted certificate message, this must not interfeere with SSO process. Initial landing page is presented by ASA/FTD. Upon accepting this one, you should proceed with SSO, where Microsoft certificate will be used, and which has nothing with certificates you are using or configuring.
Certificate that you have configured from above screenshot is used to encrypt communication between ASA/FTD and Azure. This process is transparent to end user, so no certificate warnings will be presented to user for this part. However, if misconfigured, it will cause authentication process to fail.
For this part, I believe you should proceed with downloading certificate from Azure portal and importing it to FTD. Once imported, you should verify that it is properly imported before proceeding with next steps.
Certificate that is used for landing page, if used with https://<MyVPNIP> will almost always cause warnings, as certificates are issued for FQDN and not IPs (you can use it for IP as well, but you have to put IP in SAN field, and no public CA will sign this). You should create certificate for https://<myhost.mydomain>, and, if you can't create public DNS at this phase, you can modify hosts file on local PC in order to create DNS record. Once certificate is created, you must import it in trusted credentials store on local PC, and this way, you'll avoid certificate warning. Please be aware that certificate used for landing page and one used for IdP are different ones.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2022 09:09 AM
Hi Milo,
Thanks for your suggestion. I will try it later this week.
BR,
Banny
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide