- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Remote Site-2 ISP-Redundant IPSEC Tunnel - Failover Fail - SA Up
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Remote Site-2 ISP-Redundant IPSEC Tunnel - Failover Fail - SA Up
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 01:16 PM - edited 02-21-2020 09:43 PM
Hello,
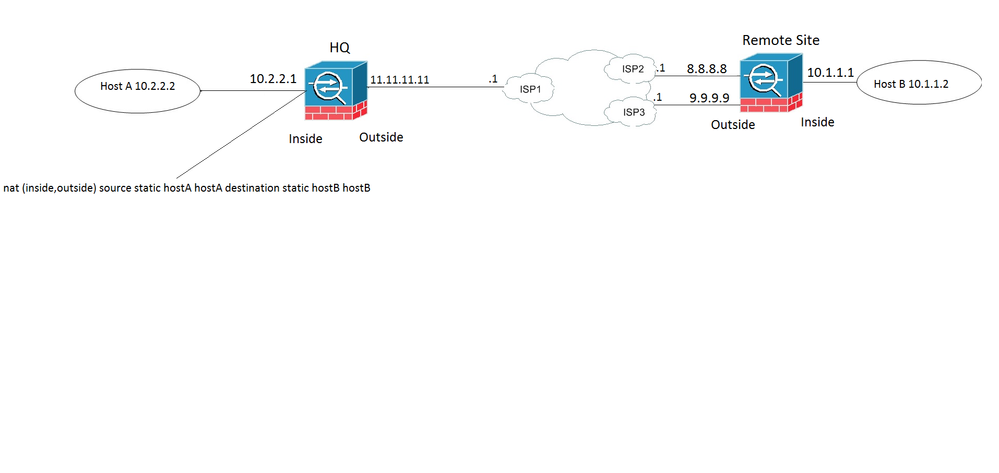
I have am having an issue with a remote site redundant IPSEC tunnel config. When the remote site is on the primary IPSEC tunnel, the traffic from Host A to Host B is successful. When the primary link fails, the second tunnel can be established but host to host communication fails. I should mention that when I initiate the fail over at the remote site by pulling the plug, I have to run packet tracer to get the tunnel to come over the backup ISP. The tunnel is created and the SA is active however the host traffic does not get reassigned. I am using an SLA and a track to test reach ability and remove the static route. The remote host's DG is the inside interface of the remote fw. Could anyone shine some light on what I may be missing. Here is the config and I appreciate any help.
Thanks,
HQ Config
crypto map map-outside 100 match address to-remote-site-interesting traffic
crypto map map-outside 100 set peer 8.8.8.8 9.9.9.9
crypto map map-outside 100 set ikev1 transform-set vpn-l2l
tunnel-group 8.8.8.8 type ipsec-l2l
tunnel-group 8.8.8.8 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group 9.9.9.9 type ipsec-l2l
tunnel-group 9.9.9.9 ipsec-attributes
ikev1 pre-shared-key *****
nat (inside,outside) source static hostA hostA destination static hostB hostB
route outside 10.1.1.0 255.255.255.0 11.11.11.1 1
Remote Config
Interface Name Security
GigabitEthernet1/1 OUTSIDE 0
GigabitEthernet1/2 INSIDE 100
GigabitEthernet1/4 OUTSIDE2 0
GigabitEthernet1/1 8.8.8.8
GigabitEthernet1/2 10.1.1.1
GigabitEthernet1/3 unassigned
GigabitEthernet1/4 9.9.9.9
crypto map CMAP 1 match address to-HQ-site-interesting traffic
crypto map CMAP 1 set peer 11.11.11.11
crypto map CMAP 1 set ikev1 transform-set vpn-l2l
crypto map CMAP interface OUTSIDE
crypto map CMAP interface OUTSIDE2
crypto ikev1 enable OUTSIDE
crypto ikev1 enable OUTSIDE2
tunnel-group 11.11.11.11 type ipsec-l2l
tunnel-group 11.11.11.11 ipsec-attributes
ikev1 pre-shared-key *****
sla monitor 123
type echo protocol ipIcmpEcho 4.4.4.4 interface OUTSIDE
num-packets 3
frequency 10
sla monitor schedule 123 life forever start-time now
track 1 rtr 123 reachability
route OUTSIDE 0.0.0.0 0.0.0.0 8.8.8.1 1 track 1
route OUTSIDE2 0.0.0.0 0.0.0.0 9.9.9.1 254
-Nathan
- Labels:
-
IPSEC
-
Other VPN Topics
-
Remote Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2019 06:55 AM
Update:
This config actually works. The issue was that the secondary ISP device did not have port forwarding properly configured and was silently dropping traffic.
-Nathan
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide