- Cisco Community
- Technology and Support
- Security
- VPN
- Site to Site VPN failover with Cisco ASA or ASA FTD ??
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Site to Site VPN failover with Cisco ASA or ASA FTD ??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 02:33 AM
Hi,
We are running two Cisco firewalls(Cisco ASA firewall & Cisco ASA FTD).
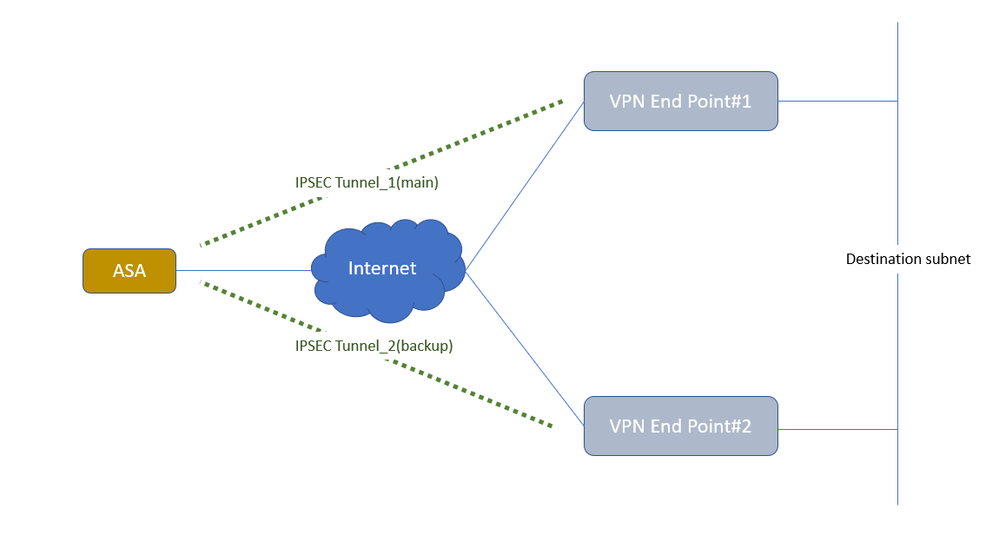
And, we are planning to set two IPSec tunnels to different endpoints pointing the same destination on each firewall as attached snapshot shows.
What I look after is how we can set IPSec failover which make one IPSec is main and the other one is backup.
I am not sure if the way to configure is different between Cisco ASA firewall & Cisco ASA FTD).
If it is, please advise me how to make it work on each firewall platform.
- Labels:
-
IPSEC
-
Other VPN Topics
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 02:39 AM
@kay.kang on the ASA you can define 2 peers i.e., - "crypto map CMAP 1 set peer 1.1.1.5 2.2.2.5". With this configuration the ASA will connect to 1.1.1.5 (VPN Endpoint #1) until it fails and then will failover to 2.2.2.5 (VPN Endpoint #2).
Alternatively you can use VTI's on both the ASA and FTD, you'd use BGP to prefer one VPN tunnel over the other, in the event of failure the routes would be removed from the primary peer and traffic will be routed over the secondary peer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 02:42 AM
Hi Rob,
We're not using BGP routing.
The routing on the Internet link on the ASA firewall will be static default route.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 02:48 AM - edited 07-27-2022 02:49 AM
@kay.kang the BGP option was an alternative suggestion if you used VTIs, so you can use the first option.
Besides, BGP would be run over the VTI tunnels not on the underlay.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 02:56 AM
We don't see VTI option on our FMC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 02:57 AM
Is VTI only option to achieve the goal for that Site to Site VPN failover?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 03:00 AM
VTI was only introduced in version 6.7 https://www.cisco.com/c/en/us/td/docs/security/firepower/670/relnotes/firepower-release-notes-670/features.html
No, I provided 2 options. The first option does not require VTIs
On the ASA you can define 2 peers i.e., - "crypto map CMAP 1 set peer 1.1.1.5 2.2.2.5". With this configuration the ASA will connect to 1.1.1.5 (VPN Endpoint #1) until it fails and then will failover to 2.2.2.5 (VPN Endpoint #2).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 03:04 AM
Is crypto map option available only Cisco ASA?
How about Cisco FTD?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 03:06 AM - edited 07-27-2022 03:12 AM
@kay.kang both options, crypto map and VTIs are available on both the ASA and FTD.
However VTI were introduced in ASA v9.7 and FTD 6.7, crypto map (Policy Based VPN) are available on both ASA and FTD for a lot longer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 03:18 AM
Hi Rob,
I see crypto map option on ASDM(Cisco ASA).
But, I don't see the option about crypto map on FMC.
Where can I see the crypto map part on FMC?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 03:23 AM
@kay.kang the terminology is different on the FTD, you would want a P2P (point-to-point) VPN, this uses a crypto ACL just like the ASA to define interesting traffic.
This is an example to configure a VPN between an FTD and an ASA https://integratingit.wordpress.com/2020/08/26/ftd-site-to-site-vpn/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 03:34 AM
I see we set crypto map type static on FMC.
And, the endpoint IP is single IP (not listed backup peer IP using comma).
Is that how to set the failover if I add one more peer IP using command on Endpoint setup?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 03:43 AM - edited 07-27-2022 03:47 AM
@kay.kang No, as per your diagram the ASA is the firewall that needs 2 peers defined. Which is why I provided the ASA configuration to use.
On the FMC, you need to define 2 topologies. One topology with VPN Endpoint #1 to ASA and another topology for VPN Endpoint #2 to ASA. The configuration of the ASA dictates which FTD to connect to first.
Refer to the Cisco live session - BRKSEC-3629 which has more examples and screenshots of HA VPN topologies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 03:48 AM
If I create two IPSec tunnels on FMC like below.
How can we make which IPSec is main and which one is backup IPSec tunnel?
IPSec setup_1
Node A: FTD firwall public IP
Node B: Endpoint#1 public IP
IPSec setup_1
Node A: FTD firwall public IP
Node B: Endpoint#2 public IP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2022 04:04 AM - edited 07-27-2022 04:55 AM
Node A is an FTD? So what is Endpoint #1 and Endpoint #2? Which device is the ASA, because in your example above I'd expect Node A to be the ASA, but you've said it's an FTD....it makes a difference. Please be clear which firewall is where in relation to your diagram.
Regardless, set configuration of the VPN topologies of Endpoint's #1 and #2 to "answer-only", refer to Connection Type https://www.cisco.com/c/en/us/td/docs/security/firepower/660/configuration/guide/fpmc-config-guide-v66/firepower_threat_defense_site_to_site_vpns.html - this way it ensures only traffic initiated by the other device (the ASA device on the left of your diagram) will establish a VPN tunnel. It will establish the VPN tunnel to the peer defined first, when that fails it will failover to the secondary peer.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide