- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Static route over IPSec Tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2020 12:07 AM - edited 07-23-2020 12:09 AM
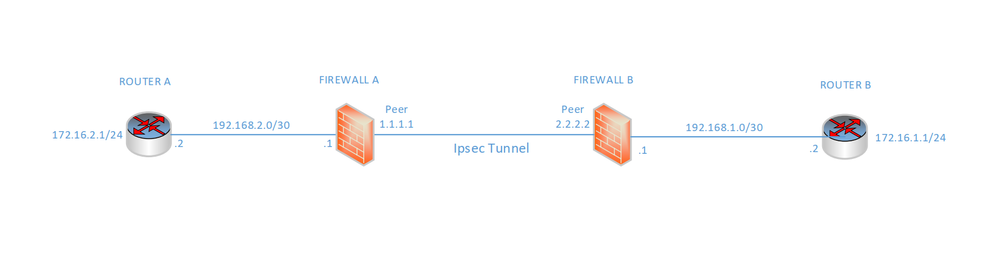
Hi, I need to reach a secondary router internal subnet which is at the end of an ASA ipsec tunnel (see attached)
For clients on Router A (172.16.2.1/24) to reach clients on Router B (172.16.1.1/24), would it just be a case of entering a static route eg
Router A
ip route 172.16.1.0 255.255.255.0 192.168.1.2
Router B
ip route 172.16.2.0 255.255.255.0 192.168.2.2
assuming that Router A (192.168.2.1/30) can see Router B (192.168.1.2/30) and vice versa ie tunnel is up and running
Solved! Go to Solution.
- Labels:
-
IPSEC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2020 08:32 AM
access-list VPN extended permit ip 172.16.2.0 255.255.255.0 172.16.1.0 255.255.255.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2020 12:41 AM
yes it should work as expected to reach far end device, hope far end device has only 1 exit and static route towards .1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2020 03:51 AM
I assume the ASA's are using a crypto map rather than a VTI?
Router A would not have a next hop of 192.168.1.2, it's next hop IP address would be Firewall A's inside IP address of 192.168.2.1.
Router B would not have a next hop of 192.168.2.2, it's next hop IP address would be Firewall B's inside IP address of 192.168.1.1.
Both Firewall's would need to have a default route pointing to it's next hop IP address via the outside interface and an ACL defining the interesting traffic in order to establish the VPN.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2020 04:38 AM
Sorry, typo there.
Yes router A has a next hop address of Firewall A (192.168.2.1)
Firewall A also has a route like so:
ip route 172.16.2.0 255.255.255.0 192.168.2.2 (Router A)
The IPsec tunnel on has a security association like so:
192.168.2.0/30>1.1.1.1 ------ 2.2.2.2< 192.168.1.0/30
One side is an ASA, the other a Sophos UTM
Does the ASA have to have an ACL for the vpn interesting traffic or will it be sufficient to just put a route statement on it like:
ip route 172.16.1.0 255.255.255.0 192.168.1.1 if firewall B has a route statement like :
ip route 172.16.1.0 255.255.255.0 192.168.1.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2020 04:48 AM
If you were using a VTI would you specify a static route, but via the tunnel interface rather than the outside interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2020 07:27 AM
So for the interesting traffic on Firewall A,
i would have to add an ACL like:
permit ip 172.16.2.0 0.0.0.255 192.168.1.0 0.0.0.3
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2020 08:32 AM
access-list VPN extended permit ip 172.16.2.0 255.255.255.0 172.16.1.0 255.255.255.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2020 09:20 AM
Brill thank you
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide