- Cisco Community
- Technology and Support
- Security
- VPN
- Tunnel Group clarification
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Tunnel Group clarification
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2015 04:25 AM
Hi, i would like to know what exactly the tunnel groups are used for and how they're "called" in VPN's etc...
Basically, i would like to know what the actual use of them are and what would happen if they weren't configured in the VPN process. Also, how are they actually "called" in terms of what activates them? I know you set them to the "peers" address, so is it the peers address when its triggered and contacted it automatically activates the tunnel group?
Sorry i am a bit new to configuring VPN's, i have most of the concepts down now, its just certain things that I'm not getting and these are pretty much the only ones left i need to figure out.
Thanks
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2015 07:11 AM
Hello.
Tunnel group need if you want to use a different rules for each type of users. For wxample one group can have a rules for connecting no more than 20 users at the same time, 20 minutes of idle time (before droping connection) and have access only to email server. And another group can have access to all servers, has a 60 min idle time (before droping VPN connection) and etc.
For this you can create a different tunnel group.
For identification to the group user can send a group-name/password or a certificate.
Best Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2015 11:31 PM
Hi, thanks for the reply, this is the one concept i am having trouble understanding with VPN's, so i appreciate the help.
So the tunnel group is "triggered" or "called" when a certain user logs in using a certain username and password and then it ?
What about if its a site to site VPN and there are no usernames and passwords but still tunnel groups? What distinguishes each tunnel group then?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 12:05 AM
Hi.
Tunnel groups are the part of EzVPN technology. When you configure your VPN this way you are allways providing group-name/password or certificate with mapping data to group.
At the site to site (or lan to lan) VPN usually uses a crypto maps with IPSec profiles without tunnel groups. Or you can also use a GRE with IPSec. At this way you don't need a tunnel group too.
Best Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 01:39 AM
Hi
So for remote access, the client will have some kind of VPN software on their PC, then will they enter the tunnel group credentials such as the tunnel group name or address along with a PSK or certificate they have? Then the ASA will have the exact name of the tunnel group and then from there the user has his own username and password which is then entered and then as long as its vaild, verified on the ASA or possibly an AAA server?
Thanks for your help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 10:14 PM
Hello.
Yes, it is like this. For example here is how it looks at the CiscoVPN Client:
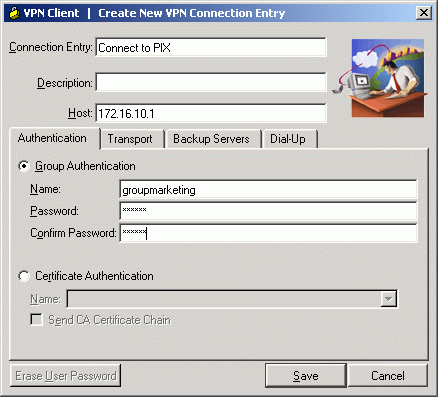
You can chose to send a group name + password or use a certificate. And after this it will ask you for a AAA data:

Cisco devices can connect to VPN server without any additional software.
BTW Cisco ASA can authenticate users not only by local AAA or RADIUS serever but by a AD server (LDAP) as well.
Best Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 10:50 PM
Thank you very much, you have been very helpful with this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2015 01:51 AM
Tunnel Group = Connection Profile. The Tunnell Group (Connection Profile) distinguishes different connection types from each other.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 11:05 PM
crypto ipsec ikev1 transform-set VPN esp-aes 256 esp-sha-hmac
!
crypto map VPN_MAP 1 match address VPN_1
crypto map VPN_MAP 1 set peer 172.16.20.2
crypto map VPN_MAP 1 set security-association lifetime seconds 8600
crypto map VPN_MAP 1 set ikev1 transform-set VPN
crypto ikev1 policy 1
encr aes
authentication pre-share
group 5
lifetime 8600
Also, along with configuring pre shared keys with site to site. I was wondering where exactly do i configure the the PSK password? i cant seem to find the right syntax in packet tracer?
Thanks again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2015 04:00 AM
Hello.
One of the way is:
#conf t
#crypto isakmp key ? ("?" to see possible commands)
Another way is creating a crypto keyring.
Best Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2015 10:40 AM
Hi
These commands are unfortunately not avaiable in packet tracer. I have had to create a tunnel group and do it this way, will this work?
tunnel-group 172.16.20.2 type ipsec-l2l
tunnel-group 172.16.20.2 ipsec-attributes
ikev1 pre-shared-key cisco
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2015 10:18 PM
Hello.
Sorry, my commands was for a router. Your commands are for ASA and it will work this way well (at the ASA device).
Best Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2016 11:12 PM
Hi, you mentioned that there are no need for crypto maps for site to site normally. I have a couple of questions on how the tunnel groups are "called" and recognised with clinetless SSL and the site to site config i have set up here.
For my site to site i have this config:
crypto ipsec ikev1 transform-set VPN esp-aes 256 esp-sha-hmac
!
crypto map VPN_MAP 1 match address VPN_1
crypto map VPN_MAP 1 set peer 172.16.20.2
crypto map VPN_MAP 1 set security-association lifetime seconds 8600
crypto map VPN_MAP 1 set ikev1 transform-set VPN
crypto map VPN_MAP interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
encr aes
authentication pre-share
group 5
lifetime 8600
!
tunnel-group 172.16.20.2 type ipsec-l2l
tunnel-group 172.16.20.2 ipsec-attributes
ikev1 pre-shared-key cisco
!
I need the tunnel group for the pre shared key in packet tracer. But say for example if i create another tunnel group now with the same "type" and "attributes" and the same key but with a different address, will it not be called because of the "set peer 172.16.20.2" in the crypto map? I'm not quite sure how the tunnel group is called in this situation?
!
!
Plus for clientless SSL which i have got working:
!
tunnel-group webvpn type remote-access
tunnel-group webvpn general-attributes
default-group-policy webvpn
!
group-policy webvpn internal
group-policy webvpn attributes
vpn-tunnel-protocol ssl-clientless
webvpn
url-list value test1
!
username bob password 4IncP7vTjpaba2aF encrypted
username bob attributes
vpn-group-policy webvpn
!
How is the "webvpn" tunnel group being called here? I understand how it associates with the group policy via the username attributes but whats to stop me from creating webvpn2 tunnel group with the same stuff in it, what is the difference and which one is called the?
Thanks for all your help by the way!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2016 03:23 AM
Hi.
Sorry for a long responce.
I need the tunnel group for the pre shared key in packet tracer. But say for example if i create another tunnel group now with the same "type" and "attributes" and the same key but with a different address, will it not be called because of the "set peer 172.16.20.2" in the crypto map? I'm not quite sure how the tunnel group is called in this situation?
At this case it looks at the "match" part. Look at this like a programmer: if it hits this conditions (match part) the do this (set part). So, for examlpe if you send traffic from this network to that network use "this" rules for encryption and "this" peer.
but whats to stop me from creating webvpn2 tunnel group with the same stuff in it
If you will try to make a line "vpn-group-policy webvpn2" at the username attributes it will change the current line instead of adding a new one. So you can have only one linked group policy to the one username.
And the tunnel group itself colling by the name of the tunnel group (tunnel group and policy group should have the same name).
Best Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 06:01 AM
Hi there,
I believe I completely understand what you are looking for. Sorry - I am not the one who can answer, in fact I am someone who has this same question as you (perhaps that's why I understand what you are precisely asking for, time and again in your question and the comments).
In case you have figured this out by now, would you please enlighten me as well?
Thanks & Regards,
Mit
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide