- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Two IPSEC to work in active/standby mode
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Two IPSEC to work in active/standby mode
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2022 06:23 AM
Hello Community,
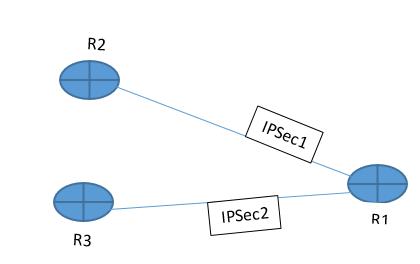
I have to configure two IPSec tunnels on a cisco 4221 router, each tunnel should be established with a different router but the two tunnels should work in active/standby mode, how can I do this please?
Topology is as below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2022 06:26 AM - edited 05-19-2022 01:51 PM
you must config
in R1 under IPSec map
set peer R2
set peer R3
in R2 and R3 you must config
set route <-reverse-route
this make R1 know the LAN behind R2 and R3 only when the IPSec tunnel is establish, and hence the R1 have two peer it will try R2 then if not response it will try R3.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2022 06:43 AM
Hi MHM,
Thanks for your reply, could you please provide me some sample configuration?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2022 03:45 AM - edited 05-20-2022 07:28 AM
just one more Q are R2 and R3 are HSRP peer?
Anyway check this link
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2022 06:26 AM - edited 05-19-2022 06:28 AM
@isbou1986 use FlexVPN. Several options, use a dynamic routing protocol and establish an adjacency to both routers, then set a priority to prefer one tunnel over the other. The other option is to use the FlexVPN client configuration, this specifies a primary VPN, if that fails it will utilise the next router and establish a tunnel. Example here.
The first option using a routing protocol is the fastest at failing over, as the VPN is already established.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2022 01:22 AM
Hi Rob,
This solution look complicated for me as I'm a beginner
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2022 01:29 AM - edited 05-20-2022 01:32 AM
@isbou1986 what configuration do you already have?
Here is the example of the FlexVPN client I was referring to, where the list called "Flex_Client" defines the active and standby peer IP addresses used for failover.
SPOKE
crypto ikev2 keyring Flex_key
peer Spokes
address 0.0.0.0 0.0.0.0
pre-shared-key local cisco
pre-shared-key remote cisco
crypto ikev2 profile Flex_IKEv2
match identity remote address 0.0.0.0
authentication remote pre-share
authentication local pre-share
keyring local Flex_key
crypto ikev2 dpd 30 5 on-demand
crypto ikev2 client flexvpn Flex_Client
peer 1 1.1.1.1
peer 2 2.2.2.1
client connect Tunnel1
crypto ipsec transform-set IKEv2 esp-gcm
mode transport
crypto ipsec profile default
set ikev2-profile Flex_IKEv2
interface Tunnel1
description FlexVPN tunnel
ip address negotiated
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source Ethernet0/0
tunnel destination dynamic
tunnel path-mtu-discovery
tunnel protection ipsec profile default
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2022 03:13 AM
Hi,
I don't have any configuration, they are new routers, but what is important here is the configuration on R1, because R2 and R3 belong to another organization with whom I should make secure connexion. I should have two VPN on R1 that will work as one master and one standby.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2022 03:14 AM
The VPN peers have different IP
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide